在现今社会APP已经是泛滥了,任何一个公司或者企业或多或少的都会有自己的APP,而APP的安全也是一块新天地。发布多少,这次帖子主要是从APK逆向分析出手。
1、利用吾爱破解论坛的demoapk实战破解分析;
下载论坛上的debug.apk(https://wwi.lanzoup.com/iGJzi012bscf);

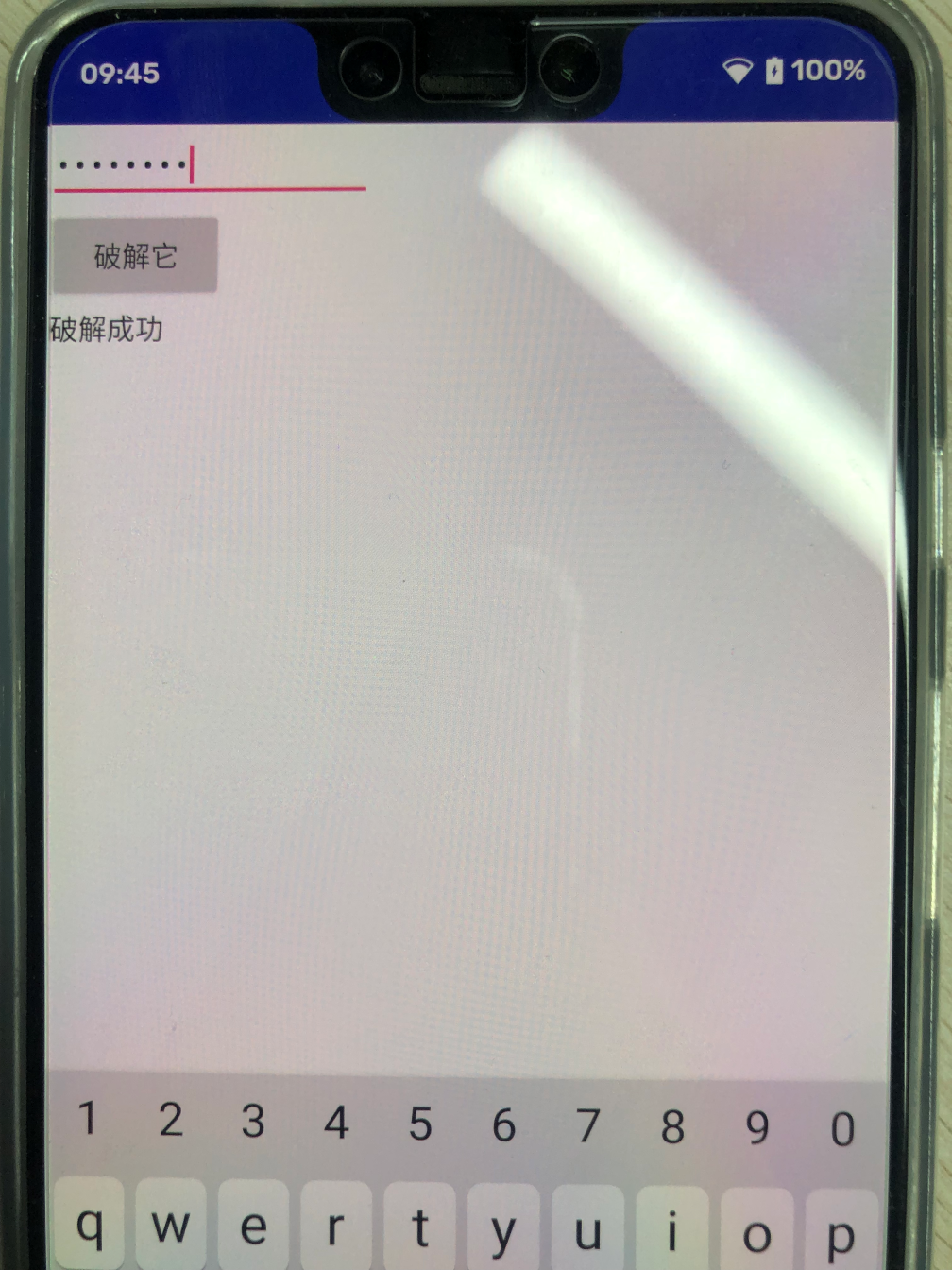
随便输入都是破解失败。接下来我们就让他随便输入都是破解成功;
2、下载相关破解工具;
apktool_2.6.1.jar(https://bitbucket.org/iBotPeaches/apktool/downloads/)
3、反编译目标apk(这里由于使用的demo,没有加壳,对于加壳的APP还需要使用frida或BlackDex64等其他工具进行脱壳)
java -jar apktool.jar d debug.apk
4、方便过后得到一个debug文件夹
5、找到smali文件;
通过jeb动态分析逻辑或AndroidKiller_v1.3.1工具都可以,这里根据论坛上的指引,找到了反编译之后的Screen1.smali文件;
6、打开Screen1.smail文件,定位到需要破解的位置;
原始代码中的判断逻辑方法在u6309u94ae1$Click方法中,找到if-eq v0, v1, :cond_0,这里 如果v0 等于v1 的值,那么就执行const-string v2, "\u7834\u89e3\u5931\u8d25"破解失败;
这里改了一下
if-eq v0, v1, :cond_1如果v0等于v1的值,那么就执行const-string v2, "\u7834\u89e3\u6210\u529f" 破解成功
.method public u6309u94ae1$Click()Ljava/lang/Object;
.locals 4
.prologue
.line 29
invoke-static {}, Lcom/google/youngandroid/runtime;->setThisForm()V
sget-object v0, Lcom/google/youngandroid/runtime;->yail$Mnequal$Qu:Lgnu/expr/ModuleMethod;
sget-object v1, Lappinventor/ai_test/guess/Screen1;->Lit11:Lgnu/mapping/SimpleSymbol;
invoke-static {v1}, Lcom/google/youngandroid/runtime;->lookupInCurrentFormEnvironment(Lgnu/mapping/Symbol;)Ljava/lang/Object;
move-result-object v1
sget-object v2, Lappinventor/ai_test/guess/Screen1;->Lit17:Lgnu/math/IntNum;
invoke-static {v1, v2}, Lgnu/lists/LList;->list2(Ljava/lang/Object;Ljava/lang/Object;)Lgnu/lists/Pair;
move-result-object v1
sget-object v2, Lappinventor/ai_test/guess/Screen1;->Lit18:Lgnu/lists/PairWithPosition;
const-string v3, "="
invoke-static {v0, v1, v2, v3}, Lcom/google/youngandroid/runtime;->callYailPrimitive(Ljava/lang/Object;Ljava/lang/Object;Ljava/lang/Object;Ljava/lang/Object;)Ljava/lang/Object;
move-result-object v0
sget-object v1, Ljava/lang/Boolean;->FALSE:Ljava/lang/Boolean;
if-eq v0, v1, :cond_1
:cond_1
sget-object v0, Lappinventor/ai_test/guess/Screen1;->Lit19:Lgnu/mapping/SimpleSymbol;
sget-object v1, Lappinventor/ai_test/guess/Screen1;->Lit15:Lgnu/mapping/SimpleSymbol;
const-string v2, "\u7834\u89e3\u6210\u529f"
sget-object v3, Lappinventor/ai_test/guess/Screen1;->Lit6:Lgnu/mapping/SimpleSymbol;
invoke-static {v0, v1, v2, v3}, Lcom/google/youngandroid/runtime;->setAndCoerceProperty$Ex(Ljava/lang/Object;Ljava/lang/Object;Ljava/lang/Object;Ljava/lang/Object;)Ljava/lang/Object;
move-result-object v0
:goto_0
return-object v0
:cond_0
sget-object v0, Lappinventor/ai_test/guess/Screen1;->Lit19:Lgnu/mapping/SimpleSymbol;
sget-object v1, Lappinventor/ai_test/guess/Screen1;->Lit15:Lgnu/mapping/SimpleSymbol;
const-string v2, "\u7834\u89e3\u5931\u8d25"
sget-object v3, Lappinventor/ai_test/guess/Screen1;->Lit6:Lgnu/mapping/SimpleSymbol;
invoke-static {v0, v1, v2, v3}, Lcom/google/youngandroid/runtime;->setAndCoerceProperty$Ex(Ljava/lang/Object;Ljava/lang/Object;Ljava/lang/Object;Ljava/lang/Object;)Ljava/lang/Object;
move-result-object v0
goto :goto_0
.end method
7、改好之后进行重新打包,我这里是通过JDK自带的进行签名打包的(APK如果不签名,是无法安装的)
java -jar java -jar apktool_2.6.1.jar b 【apk反编译后的目录名称】
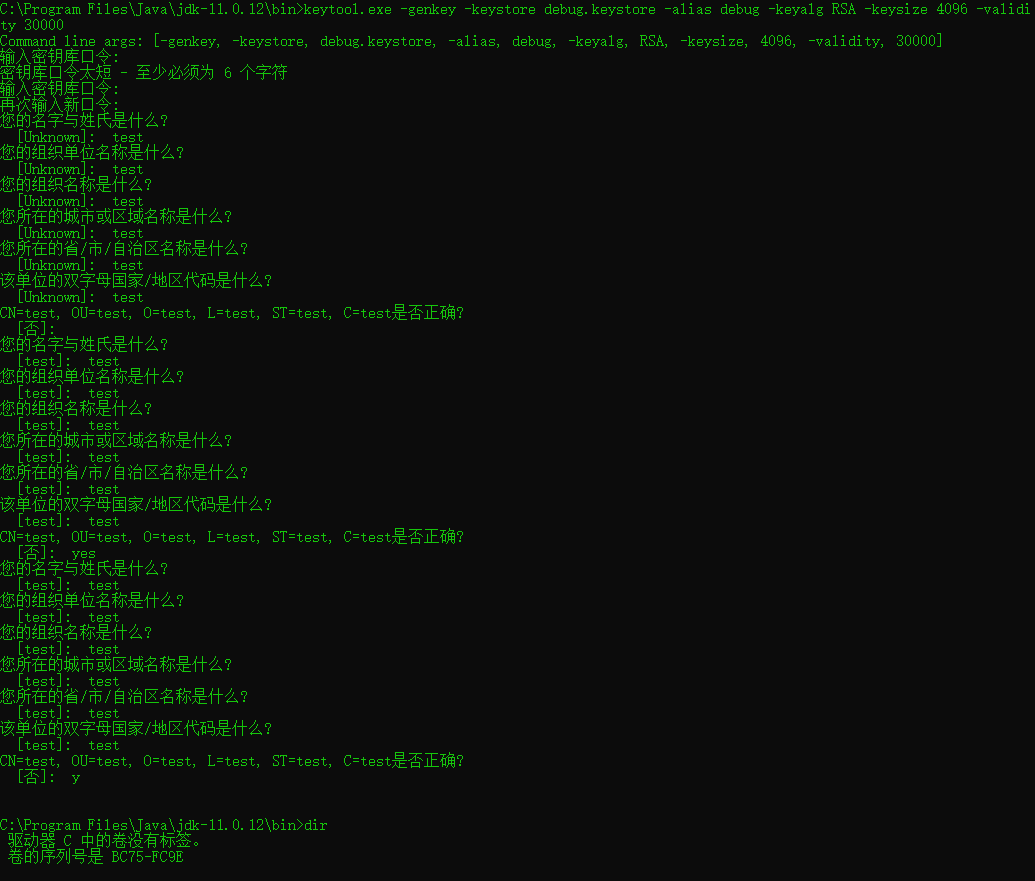
1) keytool -genkey -keystore debug.keystore -alias debugkey -keyalg RSA -keysize 4096 -validity 30000 (debug.keystore是签名证书的密钥,debugkey是证书的别名)
Windows:keytool -genkey -keystore debug.keystore -alias debugkey -keyalg RSA -keysize 4096 -validity 30000
MACOS:keytool -genkey -keystore debug.keystore -alias debugkey -keyalg RSA -keysize 4096 -validity 30000
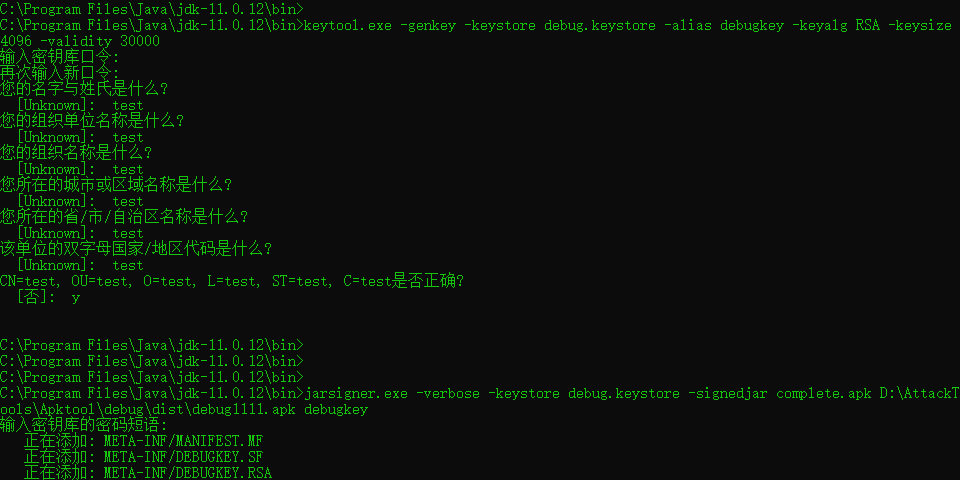
2).jarsigner -verbose -keystore [您的私钥存放路径] -signedjar [签名后文件存放路径] [未签名的文件路径] [您的证书的别名]
请看最后一个参数:[您的证书的别名],不是我们的 keystore 的 文件名就是因为这个问题
Windows:jarsigner -verbose -keystore debug.keystore -signedjar happycomplete.apk happy.apk debugkey
MACOS:jarsigner -verbose -keystore lvjuren.keystore -signedjar lvjuren_complete.apk lvjuren.apk lvjurenkey
8、发送到手机运行,随便输入都会显示破解成功;