背景
无意中看到一个分享关于如何编写脚本进行渗透前期信息收集的视频,感觉很不错,整理成文,学习一下思路。
视频 可以从 1:33:00 开始观看
纲要
在渗透前期,我们都会进行信息收集。比如子域名的获取,对子域名的端口扫描和目录扫描。前期的简单工作如图所示。
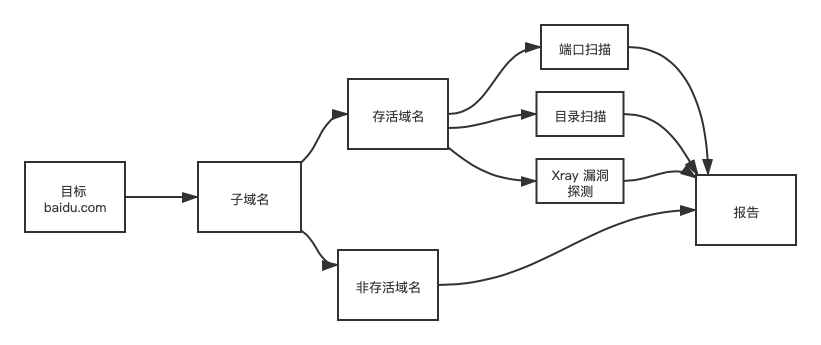
针对上面的几个步骤,视频中使用脚本即可实现。
子域名
调用网上的接口即可获取。
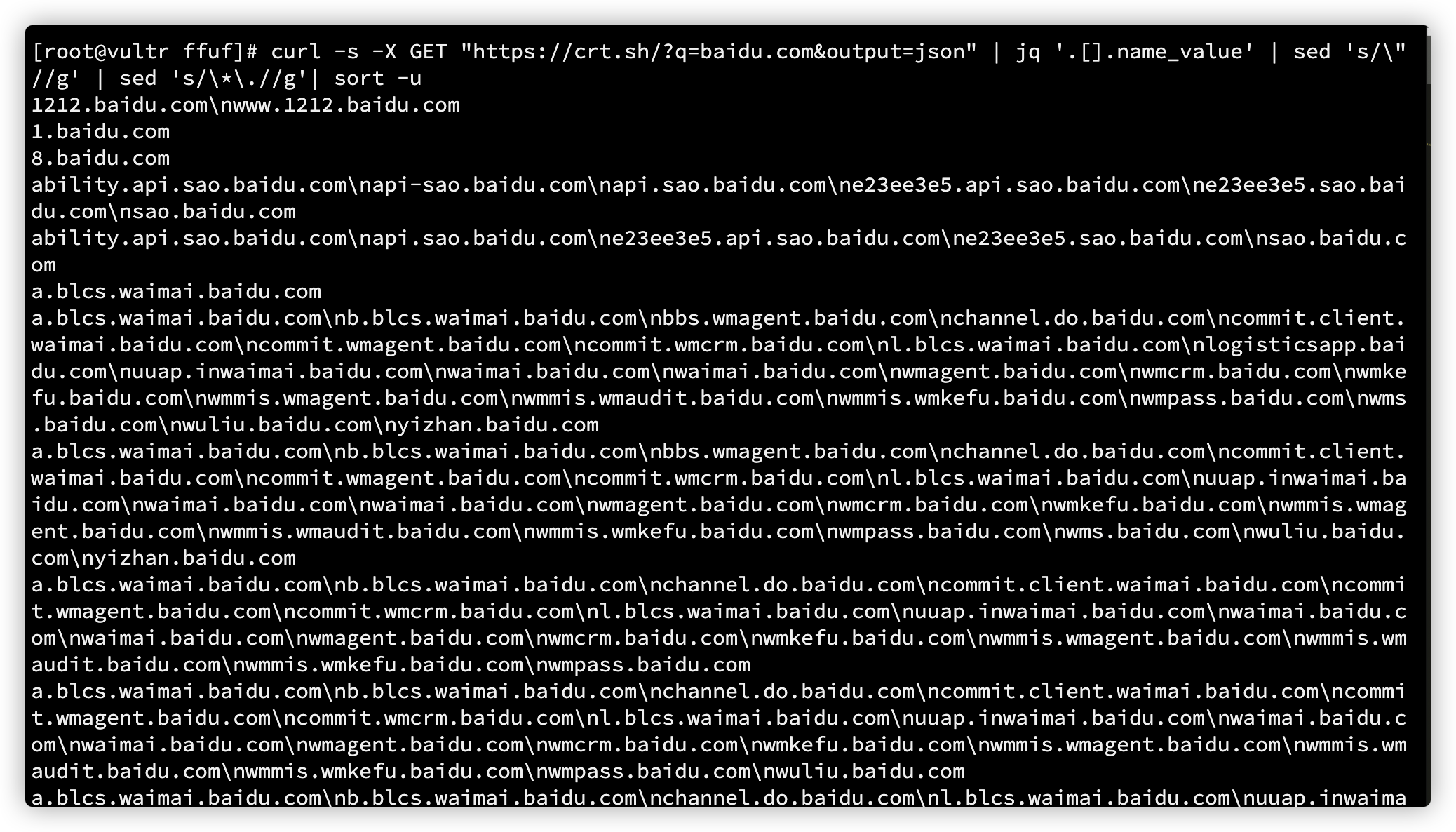
crt.sh
curl -s -X GET "https://crt.sh/?q=baidu.com&output=json" | jq '.[].name_value' | sed 's/\"//g' | sed 's/\*\.//g'| sort -u
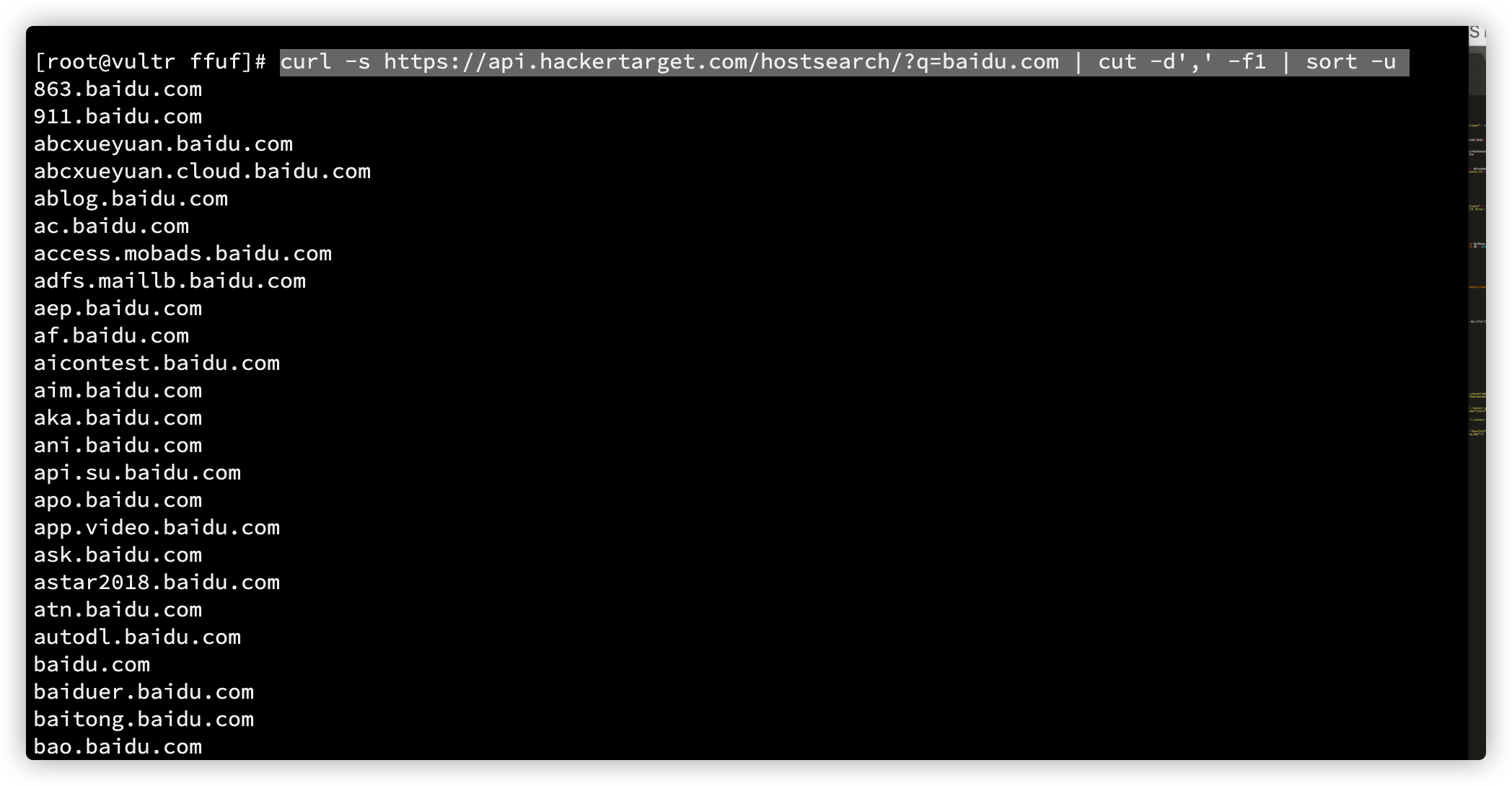
api.hackertarget.com
curl -s https://api.hackertarget.com/hostsearch/?q=baidu.com | cut -d',' -f1 | sort -u
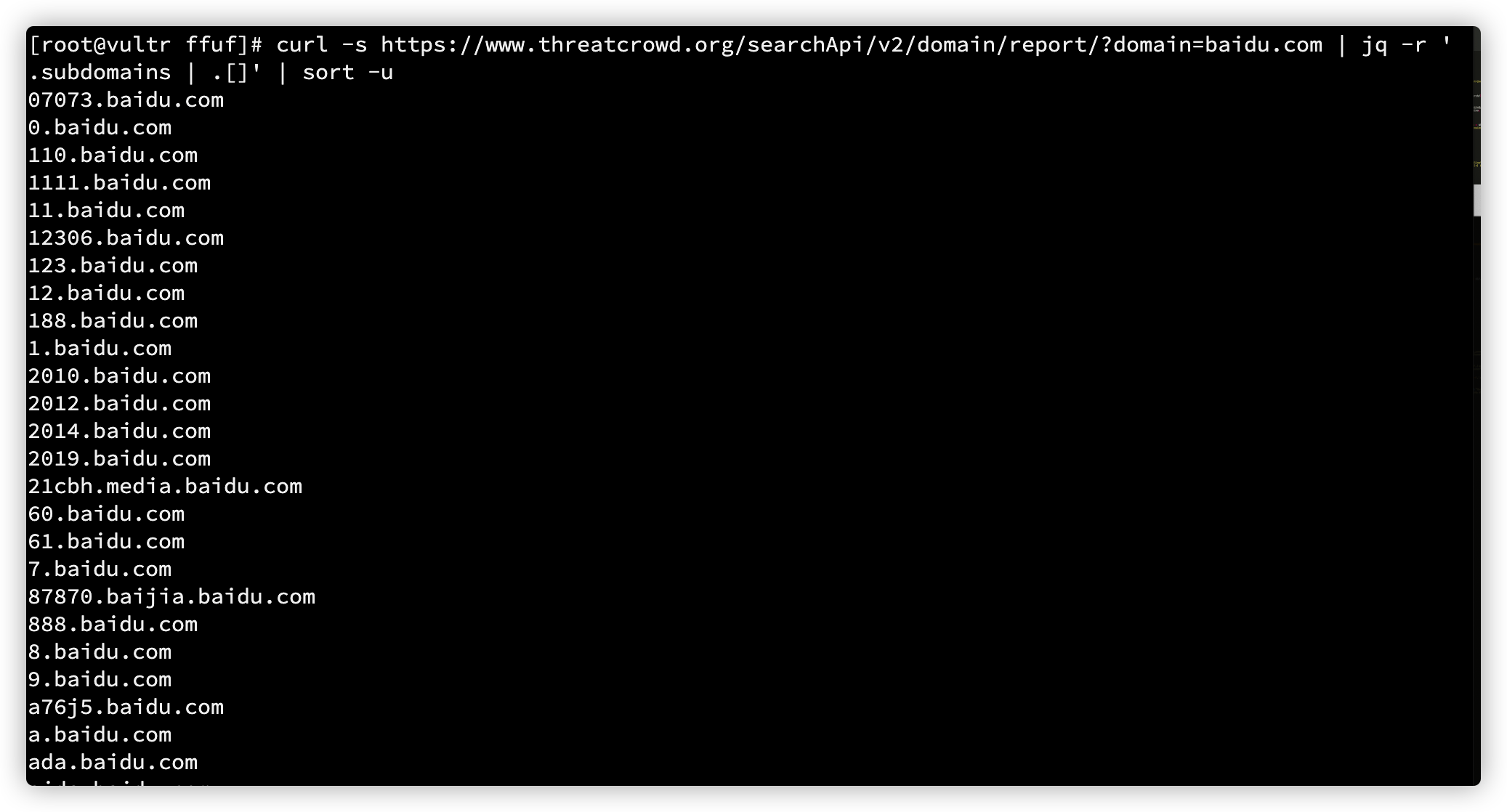
threatcrowd.org
curl -s https://www.threatcrowd.org/searchApi/v2/domain/report/?domain=baidu.com | jq -r '.subdomains | .[]' | sort -u
对上面获取的子域名进行合并整理并去重。
# Remove previous record
[ -e $1 ] && rm $1 -r
mkdir $1
echo "[-] Subdomain Enumeration";
echo "";
echo " [*] Sraeching crt.sh... ";
curl -s -X GET "https://crt.sh/?q=%.$1&output=json" | jq '.[].name_value' | sed 's/\"//g' | sed 's/\*\.//g'| sort -u >> .subdomains;
echo " [*] Searching Hackertarget... ";
curl -s https://api.hackertarget.com/hostsearch/?q=$1 | cut -d',' -f1 | sort -u >> .subdomains;
echo " [*] Searching ThreadCrowd... ";
curl -s https://www.threatcrowd.org/searchApi/v2/domain/report/?domain=$1 | jq -r '.subdomains | .[]' | sort -u >> .subdomains;
#Summing up
echo ""
cat .subdomains | sed 's/\\n/\n/g' | sort -u > $1/subdomains.txt
echo "[!] Subdomains Found: $(wc -l $1/subdomains.txt | sed 's/subdomains.txt//')";
rm -rf .subdomains;
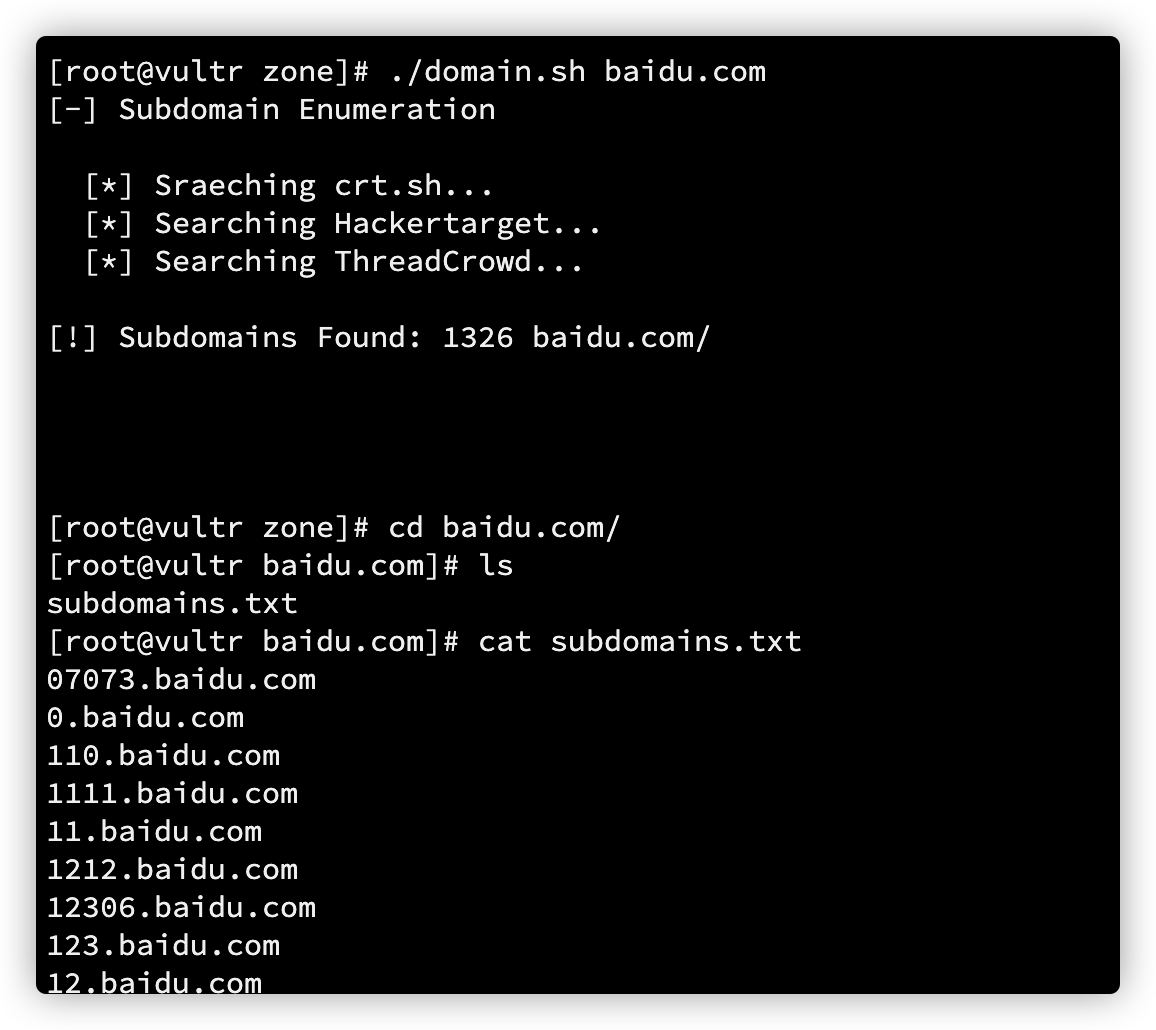
子域名存活判断
获取到的子域名不一定都是可以直接访问的。来简单判断一下,存活的域名会有对应的IP。
dig baidu.com +short
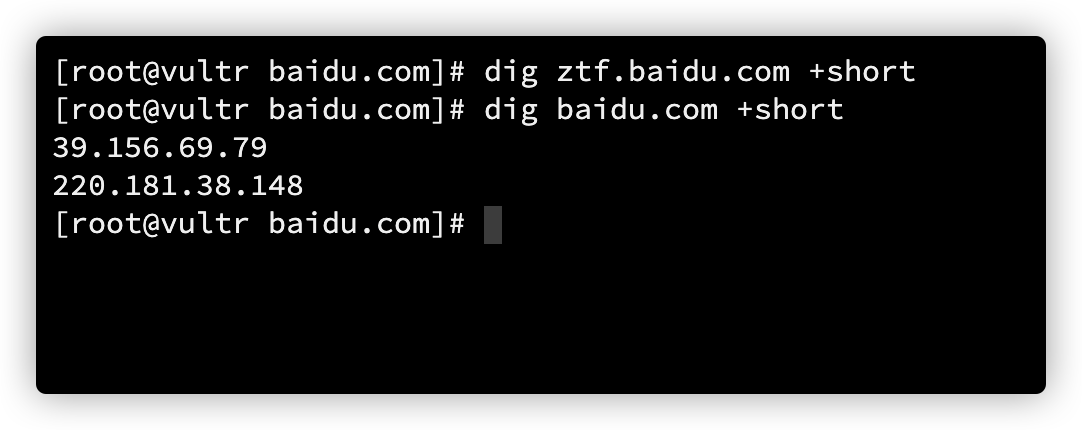
存活域名端口扫描
对上面获取到的子域名,进行快速top50端口扫描。使用grep和cut命令获取开放的端口
nmap -Pn --min-rate 1000 --top-ports 50
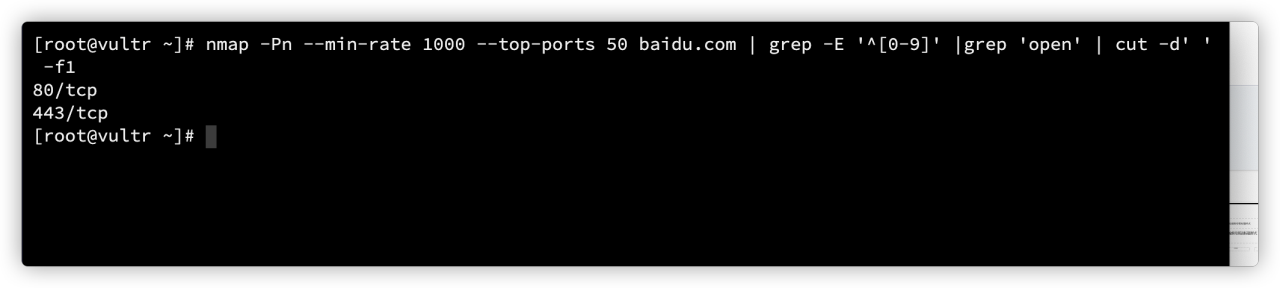
xray 基础爬虫扫描
使用xray基础爬虫模式对存活子域名进行漏洞扫描。
./xray_linux_amd64 webscan --basic-crawler http://testphp.vulnweb.com/ --html-output xray-crawler-testphp.html
目录扫描
对存活的域名使用ffuf工具进行目录扫描。
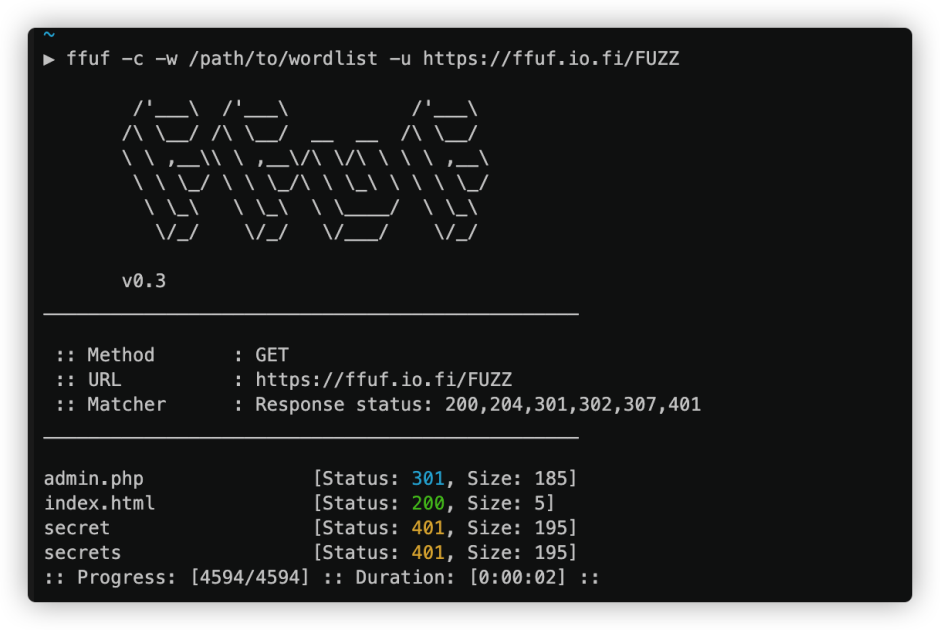
总结
对于上面的几个步骤,使用脚本来完成。
# Remove previous record
[ -e $1 ] && rm $1 -r
mkdir $1
echo "[-] Subdomain Enumeration";
echo "";
echo " [*] Sraeching crt.sh... ";
curl -s -X GET "https://crt.sh/?q=%.$1&output=json" | jq '.[].name_value' | sed 's/\"//g' | sed 's/\*\.//g'| sort -u >> .subdomains;
echo " [*] Searching Hackertarget... ";
curl -s https://api.hackertarget.com/hostsearch/?q=$1 | cut -d',' -f1 | sort -u >> .subdomains;
echo " [*] Searching ThreadCrowd... ";
curl -s https://www.threatcrowd.org/searchApi/v2/domain/report/?domain=$1 | jq -r '.subdomains | .[]' | sort -u >> .subdomains;
#Summing up
echo ""
cat .subdomains | sed 's/\\n/\n/g' | sort -u > $1/subdomains.txt
echo "[!] Subdomains Found: $(wc -l $1/subdomains.txt | sed 's/subdomains.txt//')";
rm -rf .subdomains;
printf "\n\n\n\n"
#Filtering Subdomains
echo "[-] Filtering Dead Domain";
echo "";
while read line;
do
[[ "$(dig $line +short)" ]] && printf "$line\n" >> $1/LiveSubDomains.txt
[[ "$(dig $line +short)" ]] || printf " [*] $line : [Dead]\n";
done<$1/subdomains.txt
printf "\n\n\n\n"
#Filtering Running Nmap
echo "[-] Scanning Open Ports ";
echo "";
while read line;
do
echo "[*]Scanning Ports on $line" | tee -a $1/Nmap_Report.txt
nmap $line -Pn --min-rate 1000 --top-ports 50 | grep -E '^[0-9]' |grep 'open' | cut -d' ' -f1 >> $1/Nmap_Report.txt
printf "\n\n\n" >> $1/Nmap_Report.txt
done < $1/LiveSubDomains.txt
printf "\n\n\n\n"
echo "[-] Running Xray scan ";
while read line;
do
echo " [*]Xray Scanning $line"
./xray_linux_amd64 webscan --basic-crawler https://$line --html-output $1/$line.html
done < $1/LiveSubDomains.txt
printf "\n\n\n\n"
echo "[-] Running Disearch";
while read line;
do
echo " [*]Scanning Files $line"
ffuf -u https://$line/FUZZ -w 1w.txt -o $1/.ffuf.ffuf -of csv -s
printf "\n\n\n" >> $1/ffuf.txt
cat $1/.ffuf.ffuf >> $1/ffuf.txt
done < $1/LiveSubDomains.txt
执行结果。
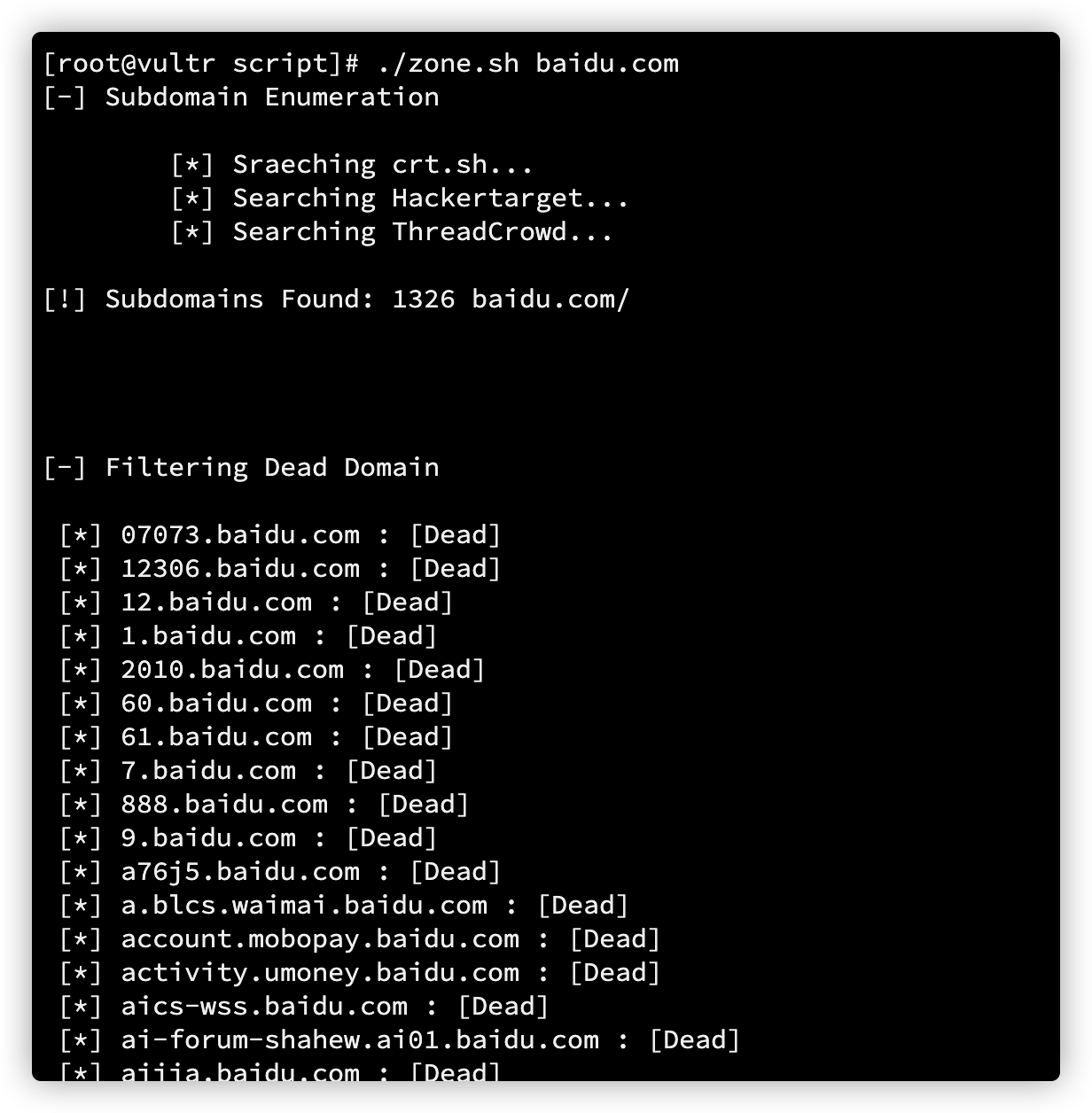
以上就是对视频中大佬讲解信息收集的整理,抛砖引玉,火线的白帽子可以评论分享你渗透测试中的小技巧~
本文迁移自知识星球“火线Zone”